This week let’s look at Active Directory domain permissions which are configured on the domain root and apply to the domain. There are many different type of concerning permissions, but let’s look at the most egregious.
Category: Security
Nov 04 2025
Active Directory Security Tip #14: Group Managed Service Accounts (GMSAs)
Group Managed Service Accounts (GMSAs) User accounts created to be used as service accounts rarely have their password changed. Group Managed Service Accounts (GMSAs) provide a better approach (starting in the Windows 2012 timeframe). The password is managed by AD and automatically changed. This means that the GMSA has to have security principals explicitly delegated …
Oct 19 2025
Improve Entra ID Security More Quickly
At BSides Northern Virginia (BSides NoVa) in October 2025, I presented a talk on how to improve Entra ID security quickly. This post captures the key information from my talk slides. This article describes the Entra ID settings and configuration that should be set to improve security including:
Oct 12 2025
BSides NoVa 2025 Presentation Slides Posted
Oct 11 2025
Microsoft Interview
Dec 19 2020
Kerberos Bronze Bit Attack (CVE-2020-17049) Scenarios to Potentially Compromise Active Directory
Introduction & Attack Overview Jake Karnes (@jakekarnes42) with NetSPI published 3 articles (that’s right 3!) describing a new attack against Microsoft’s Kerberos implementation in Active Directory. He posted an Overview article, describing how the attack works, an Attack article on practical exploitation, and if you need further background on Kerberos, a Theory article. This article …
May 29 2020
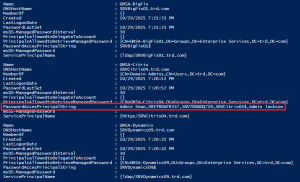
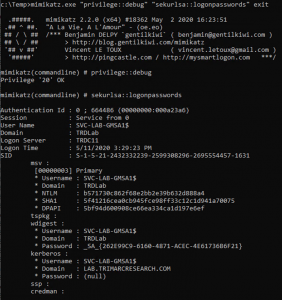
Attacking Active Directory Group Managed Service Accounts (GMSAs)
In May 2020, I presented some Active Directory security topics in a Trimarc Webcast called “Securing Active Directory: Resolving Common Issues” and included some information I put together relating to the security of AD Group Managed Service Accounts (GMSA). This post includes the expanded version of attacking and defending GMSAs I covered in the webcast.I …





Recent Comments