ShmooCon2015 was held in Washington, DC from January 16th -18th, 2015. The ShmooCon 2015 videos are now posted: https://archive.org/details/shmoocon-2015-videos-playlist ShmooCon 2015 FireTalks Videos The complete list of all presentations at ShmooCon 2015 including video download links: Keynote Address: Joseph Lorenzo Hall https://archive.org/download/shmoocon-2015-videos-playlist/Keynote%20%5BSC2015%5D.mp4Joseph Lorenzo Hall is the Chief Technologist at the Center for Democracy & Technology, …
January 2015 archive
Jan 27 2015
Enabling Windows 8 Hyper-V for a Portable Lab
Installing Hyper-V: Requirement: Windows 8 Pro or Windows 8 Enterprise which include Client Hyper-V. Requirement: Your computer processor must support virtualization technology (VT), though most processors in the past 5 years support VT (pretty much all Intel i-series processors, i3, i5, i7). Enable virtualization technology (VT) on your computer’s processor by editing the BIOS settings …
Jan 23 2015
Shmoocon 2015 FireTalks Videos
The ShmooCon 2015 Presentation Videos are posted. The ShmooCon Firetalks (2015) are posted: Opening – @grecs PlagueScanner: An Open Source Multiple AV Scanner Framework – Robert Simmons (@MalwareUtkonos) I Hunt Sys Admins – Will Schroeder (@harmj0y) Collaborative Scanning with Minions: Sharing is Caring – Justin Warner (@sixdub) Chronicles of a Malware Hunter – Tony Robinson …
Jan 22 2015
Group Policy Settings Reference for Windows 8.1 and Windows Server 2012 R2
These spreadsheets list the policy settings for computer and user configurations that are included in the Administrative template files delivered with the Windows operating systems specified. You can configure these policy settings when you edit Group Policy Objects. The Group Policy Settings reference for Windows & Windows Server can be downloaded here. Here are …
Jan 19 2015
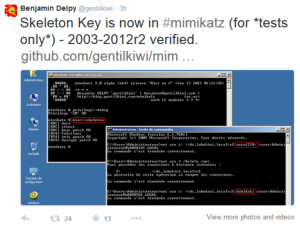
Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
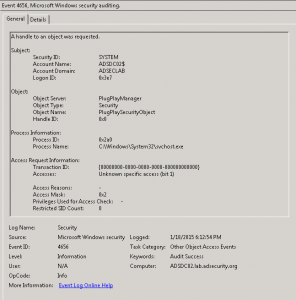
Once an attacker has gained Domain Admin rights to your Active Directory environment, there are several methods for keeping privileged access. Skeleton Key is an ideal persistence method for the modern attacker. More information on Skeleton Key is in my earlier post. Note that the behavior documented in this post was observed in a lab …
Jan 16 2015
Active Directory Domain Controller Skeleton Key Malware & Mimikatz
Dell SecureWorks posted about the Skeleton Key malware discovered at a customer site. The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS. The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins. This enables the attacker to …
Jan 14 2015
Windows Server 2012 & Windows Server 2012 R2 Complete Documentation
Microsoft took all the Windows Server 2012 (& 2012 R2) documentation and posted it as a single PDF! Version: 1.0 File Name: WS12_R2_and_WS12_TechNet.pdf Date Published: 2/18/2014 File Size: 125.9 MB This download is an Adobe® PDF of the entire contents of the Windows Server 2012 R2 and Windows Server 2012 section of the Microsoft TechNet …
Jan 13 2015
“Hacker” Movies to Watch before the Blackhat Movie
Over the years, there have been lots of “hacker” movies of varying quality. Here are some good ones to watch before the movie “Blackhat” is out starring Chris Hemsworth. My favorites in bold. Tron (1982) 8.2/10 imdb Wargames (1983) 7.1/10 imdb Sneakers (1992) 7.1/10 imdb Jurassic Park (1993) 8/10 imdb Disclosure (1994) 6/10 imdb The …
Jan 07 2015
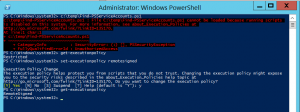
PowerShell Security: Execution Policy is Not An Effective Security Strategy – How to Bypass the PowerShell Execution Policy
If you have worked with PowerShell recently, you may have run into an Execution Policy message: c:\temp\Find-PSServiceAccounts.ps1 : File C:\temp\Find-PSServiceAccounts.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170. At line:1 char:1 + c:\temp\Find-PSServiceAccounts.ps1 + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : SecurityError: (:) [], PSSecurityException + FullyQualifiedErrorId : …

Recent Comments