There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Tag: MS14068
Dec 31 2015
Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
Microsoft’s Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. This legacy support is enabled when using Kerberos RC4 encryption …
Nov 30 2015
Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation)
At the RSA Conference in Abu Dhabi earlier this month, Stefano Maccaglia (Incident Response Consultant with RSA) presented “Evolving Threats: dissection of a Cyber-Espionage attack.” The slides for this talk are available on the RSA Conference site (UPDATE: RSA removed the slides from their site, Presentation Slides on Yumpu). This post covers and adds some …
Dec 15 2014
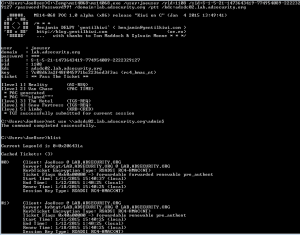
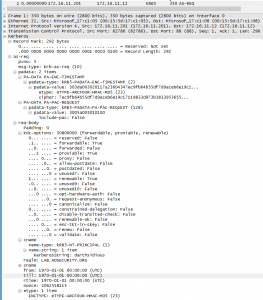
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
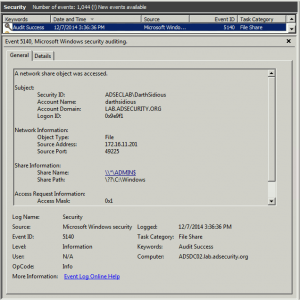
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
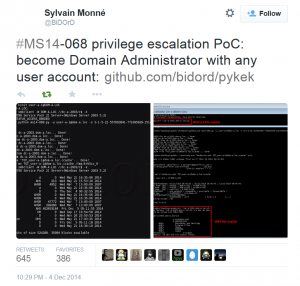
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …
Nov 21 2014
MS14-068: Active Directory Kerberos Vulnerability Patch for Invalid Checksum
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works The folks at BeyondTrust have …
Nov 19 2014
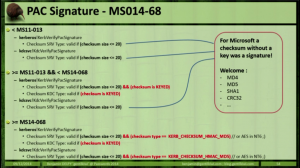
Kerberos Vulnerability in MS14-068 (KB3011780) Explained
Thanks to Gavin Millard (@gmillard on Twitter), we have a graphic that covers the issue quite nicely (wish I had of thought of it!) Exploit Code is now on the net! As of December 4th, 2014, there is Proof of Concept (POC) code posted that exploits MS14-068 by Sylvain Monné by using Python to interact with …
Nov 18 2014
MS14-068: Vulnerability in (Active Directory) Kerberos Could Allow Elevation of Privilege
Active Directory leverages the Kerberos protocol for authentication. The vulnerability patches an issue with how the Domain Controller validates group membership in Kerberos tickets (hint: the ticket is always validated by the DC if the checksum is set to certain values). Microsoft KB3011780 patches this issue. According to Microsoft: “When this security bulletin was issued, …


Recent Comments