In Active Directory, there has been a method that’s been around for many years which changes the password last set date but not the actual password. This is what I call a “fake password change” since the account appears to have a recent password when scanning for old passwords based on password last set, but the underlying password hasn’t actually changed.
I spoke about this in my 2015 BSides Charm talk which was my first conference talk.
Why does this happen?
There are times where service account (or admin accounts) need to have password changes, but someone doesn’t want to do the work to change them. The ability to fake a password change requires modify rights on the pwdLastSet attribute which provides the ability to check/uncheck the setting “User must change password at next logon”. This setting is enabled when you want the user to change their own password when they logon.
How does this work?
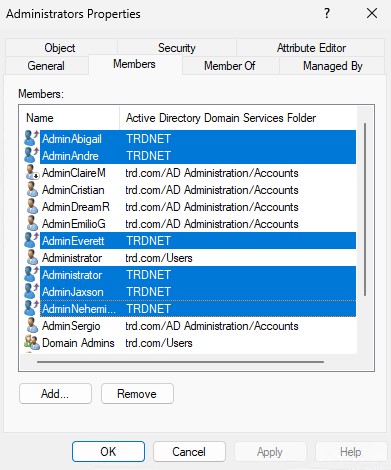
To see how this works, we’ll focus on the service account “svc-AGPM” in my lab. This account last changed its password on August 20th in 2025.
Continue reading


Recent Comments