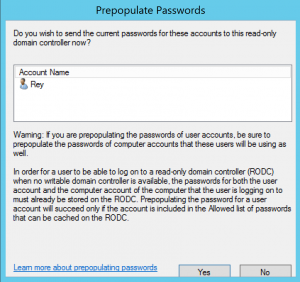
I have been fascinated with Read-Only Domain Controllers (RODCs) since RODC was released as a new DC promotion option with Windows Server 2008. Microsoft customers wanted a DC that wasn’t really a DC. – something that could be deployed in a location that’s not physically secure and still be able to authenticate users. This post …
Tag: Invoke-Mimikatz
Aug 13 2016
PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection
This post is a follow-up of sorts from my earlier posts on PowerShell, my PowerShell presentation at BSides Baltimore, and my presentation at DEF CON 24. Hopefully this post provides current information on PowerShell usage for both Blue and Red teams. Related posts: BSides Charm Presentation Posted: PowerShell Security: Defending the Enterprise from the Latest …
Apr 24 2016
BSides Charm Presentation Posted: PowerShell Security: Defending the Enterprise from the Latest Attack Platform
This was my second year speaking at BSides Charm in Baltimore. Last year I spoke about Active Directory attack & defense and it was my first time speaking at a conference. 🙂 The presentation slides for my talk “PowerShell Security: Defending the Enterprise from the Latest Attack Platform” are now on the Presentations tab here …
Mar 02 2016
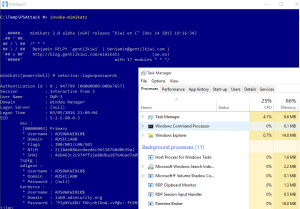
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference Updated for Mimikatz v2.1 alpha 20160229
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference page is updated for the new modules/features in Mimikatz v2.1 alpha 20160229. According to Mimikatz author, Benjamin Delpy, the following updates are included in the most recent Mimikatz version(s): Mimikatz Release Date: 2/29/2016 2.1 alpha 20160229 (oe.eo) edition System Environment Variables & other stuff [new] System Environment …
Feb 11 2016
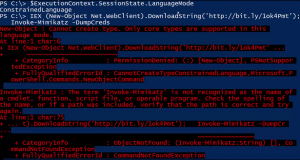
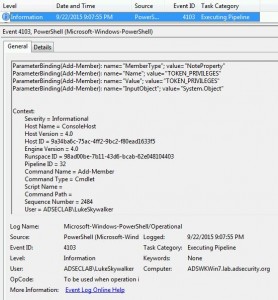
Detecting Offensive PowerShell Attack Tools
At DerbyCon V (2015), I presented on Active Directory Attack & Defense and part of this included how to detect & defend against PowerShell attacks. Update: I presented at BSides Charm (Baltimore) on PowerShell attack & defense in April 2016. More information on PowerShell Security: PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection The most …
Jan 03 2016
How Attackers Dump Active Directory Database Credentials
I previously posted some information on dumping AD database credentials before in a couple of posts: “How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller” and “Attack Methods for Gaining Domain Admin Rights in Active Directory“. This post covers many different ways that an attacker can dump credentials from Active Directory, both …
Dec 14 2015
Unofficial Guide to Mimikatz & Command Reference
A new page on ADSecurity.org just went live which is an “unofficial” guide to Mimikatz which also contains an expansive command reference of all available Mimikatz commands. Screenshots, descriptions, and parameters are included where available and appropriate. This page includes the following topics: Mimikatz Overview Mimikatz & Credentials Available Credentials by OS PowerShell & Mimikatz …
Nov 22 2014
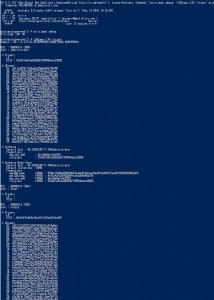
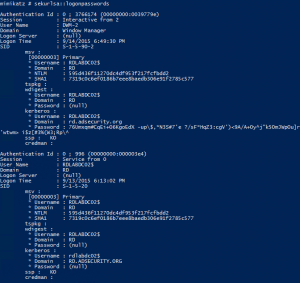
Mimikatz and Active Directory Kerberos Attacks
NOTE: While this page will remain, the majority of the Mimikatz information in this page is now in the “Unofficial Mimikatz Guide & Command Reference” which will be updated on a regular basis. Mimikatz is the latest, and one of the best, tool to gather credential data from Windows systems. In fact I consider Mimikatz …

Recent Comments