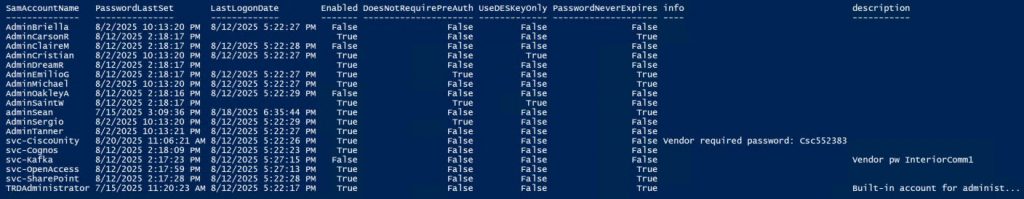
A critical part of Active Directory security is regularly reviewing your AD admins. The simplest way to do this is to recursively enumerate the membership of the domain Administrators group (that group’s members and all member group members).
Check the AD Admins output for the following:
- Are all the admin accounts associated with people expected?
- Are there service accounts that shouldn’t require AD admin rights (VMware, Exchange, LDAP, VPN, Sharepoint, etc.)?
- Are the associated passwords current?
- Are they as expected with no outliers (all within 2 years but one has a password that’s 10 years old)?
- Has the default domain Administrator account logged on recently?
- Is that expected/known?
- Are all accounts enabled?
- Disabled accounts should be removed from being an AD Admin.
- Do all accounts require Kerberos preauthentication?
- They must if they are AD admins.
- Do any use Kerberos DES?
- If so fix that.
- Are any set to never expire their password?
- Is that expected?
- Accounts with this set rarely change their password.
- Are there any passwords in Active Directory user attributes (commonly description notes/info, Exchange custom attributes, etc.)?
- Practically all of the attributes are visible to users.
PowerShell code (using Active Directory PowerShell modules):
https://github.com/PyroTek3/Misc/blob/main/Get-ADAdmins.ps1

1 comment
Thanks for this . Great compliment to my OSCP journey . Keep up the great work