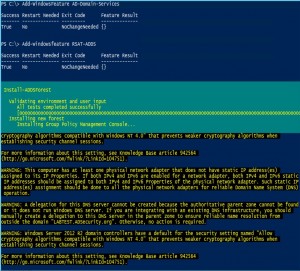
This post is not meant to describe the ultimate lab configuration. Instead the focus is on a lab environment that can be stood up quickly and easily as a learning tool. The best way to learn about computer networking and security is to have a home lab. The great thing is that a home lab …
Category: Continuing Education
Jan 29 2015
ShmooCon 2015 Presentation Videos
ShmooCon2015 was held in Washington, DC from January 16th -18th, 2015. The ShmooCon 2015 videos are now posted: https://archive.org/details/shmoocon-2015-videos-playlist ShmooCon 2015 FireTalks Videos The complete list of all presentations at ShmooCon 2015 including video download links: Keynote Address: Joseph Lorenzo Hall https://archive.org/download/shmoocon-2015-videos-playlist/Keynote%20%5BSC2015%5D.mp4Joseph Lorenzo Hall is the Chief Technologist at the Center for Democracy & Technology, …
Nov 25 2014
BlueHat Security Briefings: Fall 2014 Sesions
Microsoft has posted videos and slides from the Microsoft internal “BlueHat” security conference from October 2014. BlueHat Security Briefings educate Microsoft engineers and executives on current and emerging security threats as part of continuing efforts to help protect our customers and secure our products, devices, and services. BlueHat serves as a great opportunity for invited …
Nov 24 2014
Microsoft Consolidated Technology Conference: Microsoft Ignite
Microsoft announced over the Summer they are merging the individual technology conferences such as the SharePoint Conference, Exchange Conference, and TechEd into a single unified technology conference. Details are finally available for the Microsoft Ignite Conference which promises to be the conference to attend if you are interested in Microsoft technology solutions. Who is Ignite …
Nov 05 2014
Black Hat 2014 Presentation Video Play List
Attending Black Hat USA 2014 was a sobering and exciting experience. Here’s a playlist of interesting presentations from Black Hat conferences in 2014: KEYNOTE: Cybersecurity as Realpolitik by Dan Geer presented at Black Hat USA 2014 BadUSB – On Accessories that Turn Evil by Karsten Nohl + Jakob Lell Windows: Abusing Microsoft Kerberos Sorry You …
Oct 01 2014
Program like a Monkey – I mean an Orangutan – It’s OOK!
Learning PowerShell & Python isn’t enough… I need to learn OOK! Introduction Ook! is a programming language designed for orang-utans. Ook! is essentially isomorphic to the well-known esoteric language BrainF***, but has even fewer syntax elements. Design Principles A programming language should be writable and readable by orang-utans. To this end, the syntax should be …
Sep 12 2014
Kerberos, Active Directory’s Secret Decoder Ring
Kerberos Overview Kerberos is a protocol with roots in MIT named after the three-headed dog, Cerberus. Named because there are 3 parties: the client, the resource server, and a 3rd party (the Key Distribution Center, KDC). Kerberos can be a difficult authentication protocol to describe, so I will attempt to simplify it as best as …
May 22 2014
Microsoft TechEd 2014 Sessions Posted
One of the toughest parts of being in the IT field is staying up to date with technology trends, directions, and products. I have found that free-to-view online content is a great way to do this. Microsoft has TechEd sessions posted going back to 2008: 2014 2013 2012 2011 2010 2009 2008 Here are some …
Mar 06 2012
My Journey to Become a Microsoft Certified Master (MCM) Part 2: The MCM Program
NOTE: I do not work for Microsoft, nor have I ever worked for Microsoft. The information in this post is my thoughts and not those of Microsoft or any other company. Unless said company read my mind and placed some thoughts there… I should buy a Dell… 🙂 The content in this post belongs to …
Feb 28 2012
My Journey to Become a Microsoft Certified Master (MCM) Part 1: The Journey Begins
Just a quick note before I start. I do not work for Microsoft and have never worked for Microsoft. The information in this post is my thoughts and not those of Microsoft, or any other company. Unless said company read my mind and placed some thoughts there… I should buy a Dell… 🙂 The content …

Recent Comments