I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Nov 04 2025
Active Directory Security Tip #14: Group Managed Service Accounts (GMSAs)
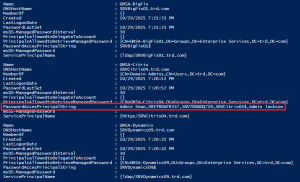
Group Managed Service Accounts (GMSAs) User accounts created to be used as service accounts rarely have their password changed. Group Managed Service Accounts (GMSAs) provide a better approach (starting in the Windows 2012 timeframe). The password is managed by AD and automatically changed. This means that the GMSA has to have security principals explicitly delegated …
Oct 19 2025
Improve Entra ID Security More Quickly
At BSides Northern Virginia (BSides NoVa) in October 2025, I presented a talk on how to improve Entra ID security quickly. This post captures the key information from my talk slides. This article describes the Entra ID settings and configuration that should be set to improve security including:
Oct 12 2025
BSides NoVa 2025 Presentation Slides Posted
Oct 11 2025
Microsoft Interview
Oct 08 2025
Active Directory Security Tip #13: Reviewing Foreign Security Principals (FSPs)
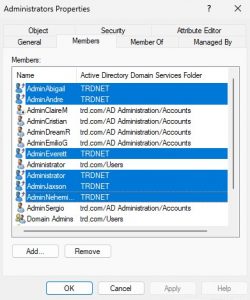
Review the membership of groups for accounts and groups from another Active Directory forest (technically another domain, but using forest here). These are called “Foreign Security Principals” (FSPs) like the ones highlighted in the image. These FSPs are accounts that exist in another forest but have rights in the AD forest. Any FSPs should be …
Oct 06 2025
Active Directory Security Tip #12: Kerberos Delegation
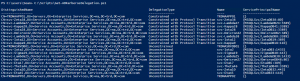
I have mentioned in several presentations that Kerberos delegation is impersonation. Kerberos delegation is used when a service (ex. web server) needs to impersonate a user when connecting to a resource (ex. database). There are a 4 types of Kerberos delegation: Unconstrained delegation should be converted to constrained delegation due to security concerns. Any Kerberos …
Oct 04 2025
The History of Active Directory Security
During the Summer of 2024, I had a talk at Troopers called “A Decade of Active Directory Attacks:What We’ve Learned & What’s Next” (Slides & Video) where I focused on the key milestones of Active Directory security (history). This article covers my “decade of Active Directory attacks” in some detail which was correlated with public …
Oct 03 2025
Active Directory Security Tip #11: Print Service on Domain Controllers
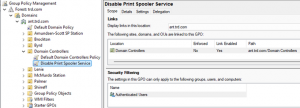
The Print Spooler service is a default service on Windows Servers and is set to run at startup. There are a number of attacks that are enabled by having the Print Spooler service running on Domain Controllers (ex.: Printer Bug: https://adsecurity.org/?p=4056) At this point it’s best to configure a GPO to disable the Print Spooler …
Oct 01 2025
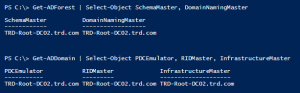
Active Directory Security Tip #10: FSMO Roles
Getting Microsoft supported backups of Domain Controllers is an important part of recovery strategy. A best practice is to locate all Flexible Master Single Operator (FSMO) roles on a single DC in the domain. That way you can more easily target the DC that hosts the FSMOs for backup. PowerShell code to check for FSMO …




Recent Comments