There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Tag: KerberosHacking
Aug 13 2015
Active Directory Security Risk #101: Kerberos Unconstrained Delegation (or How Compromise of a Single Server Can Compromise the Domain)
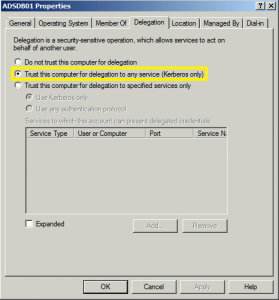
At Black Hat USA 2015 this summer (2015), I spoke about the danger in having Kerberos Unconstrained Delegation configured in the environment. When Active Directory was first released with Windows 2000 Server, Microsoft had to provide a simple mechanism to support scenarios where a user authenticates to a Web Server via Kerberos and needs to …
Aug 07 2015
Kerberos Golden Tickets are Now More Golden
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
Aug 02 2015
DEF CON 23 (2015) Red vs Blue: Modern Active Directory Attacks & Defense Talk Detail
This week at DEF CON 23, I will be speaking about Active Directory attack & defense in my talk “Red vs Blue: Modern Active Directory Attacks & Defense”. This is the 4th iteration of this talk and includes the latest updates to attack methods and defensive strategies.This DEF CON version has a new segment I …
Jul 26 2015
Black Hat USA 2015 Red vs Blue Active Directory Attack & Defense Talk Detail
Next week at Black Hat USA 2015, I will be speaking about Active Directory attack & defense in my talk “Red vs Blue: Modern Active Directory Attacks Detection and Protection”. This is the 3rd iteration of this talk and includes the latest updates to attack methods and defensive strategies. I’m including lots of updates and …
Dec 15 2014
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
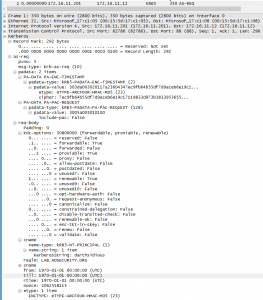
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
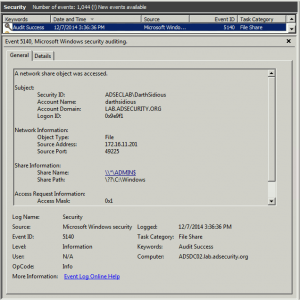
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
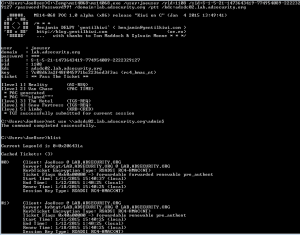
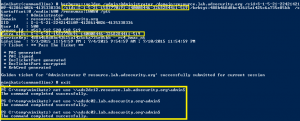
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …
Nov 21 2014
MS14-068: Active Directory Kerberos Vulnerability Patch for Invalid Checksum
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works The folks at BeyondTrust have …
Nov 19 2014
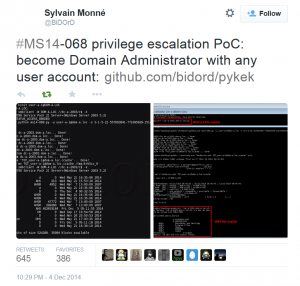
Kerberos Vulnerability in MS14-068 (KB3011780) Explained
Thanks to Gavin Millard (@gmillard on Twitter), we have a graphic that covers the issue quite nicely (wish I had of thought of it!) Exploit Code is now on the net! As of December 4th, 2014, there is Proof of Concept (POC) code posted that exploits MS14-068 by Sylvain Monné by using Python to interact with …



Recent Comments