During the Summer of 2024, I had a talk at Troopers called “A Decade of Active Directory Attacks:What We’ve Learned & What’s Next” (Slides & Video) where I focused on the key milestones of Active Directory security (history). This article covers my “decade of Active Directory attacks” in some detail which was correlated with public …
Tag: mimikatz
May 29 2020
Attacking Active Directory Group Managed Service Accounts (GMSAs)
In May 2020, I presented some Active Directory security topics in a Trimarc Webcast called “Securing Active Directory: Resolving Common Issues” and included some information I put together relating to the security of AD Group Managed Service Accounts (GMSA). This post includes the expanded version of attacking and defending GMSAs I covered in the webcast.I …
Jan 01 2018
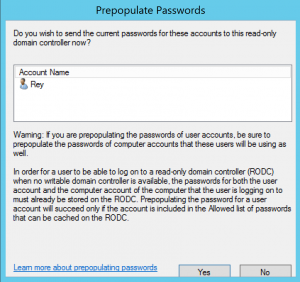
Attacking Read-Only Domain Controllers (RODCs) to Own Active Directory
I have been fascinated with Read-Only Domain Controllers (RODCs) since RODC was released as a new DC promotion option with Windows Server 2008. Microsoft customers wanted a DC that wasn’t really a DC. – something that could be deployed in a location that’s not physically secure and still be able to authenticate users. This post …
Mar 09 2016
Sneaky Active Directory Persistence #16: Computer Accounts & Domain Controller Silver Tickets
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. All posts in my Sneaky Active Directory Persistence Tricks series This post explores how an attacker could leverage computer account credentials to persist in an enterprise …
Mar 02 2016
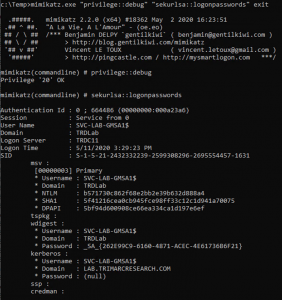
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference Updated for Mimikatz v2.1 alpha 20160229
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference page is updated for the new modules/features in Mimikatz v2.1 alpha 20160229. According to Mimikatz author, Benjamin Delpy, the following updates are included in the most recent Mimikatz version(s): Mimikatz Release Date: 2/29/2016 2.1 alpha 20160229 (oe.eo) edition System Environment Variables & other stuff [new] System Environment …
Jan 05 2016
Mimikatz Update Fixes Forged Kerberos Ticket Domain Field Anomaly – Golden Ticket Invalid Domain Field Event Detection No Longer Works
In late 2014, I discovered that the domain field in many events in the Windows security event log are not properly populated when forged Kerberos tickets are used. The key indicator is that the domain field is blank or contains the FQDN instead of the short (netbios) name and depending on the tool used to …
Jan 03 2016
How Attackers Dump Active Directory Database Credentials
I previously posted some information on dumping AD database credentials before in a couple of posts: “How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller” and “Attack Methods for Gaining Domain Admin Rights in Active Directory“. This post covers many different ways that an attacker can dump credentials from Active Directory, both …
Jan 01 2016
Attack Methods for Gaining Domain Admin Rights in Active Directory
There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Dec 31 2015
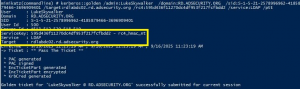
Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
Microsoft’s Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. This legacy support is enabled when using Kerberos RC4 encryption …

Recent Comments