In late 2014, I discovered that the domain field in many events in the Windows security event log are not properly populated when forged Kerberos tickets are used. The key indicator is that the domain field is blank or contains the FQDN instead of the short (netbios) name and depending on the tool used to generate the Kerberos tickets, other domain field anomalies may be present in the events.
The likely reason for the anomalies is that third party tools that create Kerberos tickets (TGT & TGS) don’t format the tickets exactly the same way as Windows does.
Around this time last year (early January 2015), I shared with customers these indicators for detecting forged Kerberos tickets and subsequently presented this information at BSides Charm 2015. Soon after, Mimikatz was updated with a domain field that was set to static values, usually containing the string “eo.oe”.
As of 4/16/2015: Mimikatz generated tickets may include the string “eo.oe.kiwi : ) ” in the domain field.
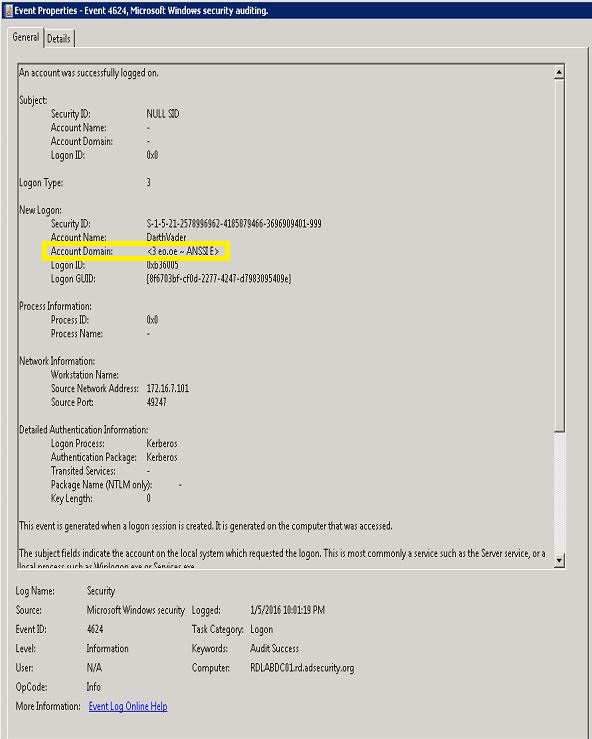
As of 6/29/2015: Mimikatz generated tickets may include the string “<3 eo.oe – ANSSI E>” in the domain field.
Few things in life are as consistent as the guarantee that things will change. In infosec, that means the attack tools will continue to evolve to evade detection and the defensive tools need to constantly evolve and improve.
If you protect your Active Directory admins (and service accounts), you will likely not have to deal with forged Kerberos Tickets since they require prior admin access. The problem is that Active Directory & Enterprises are often not secured to protect against modern threats and often, gaining Domain Admin rights to an AD domain is often too easy in many enterprises.
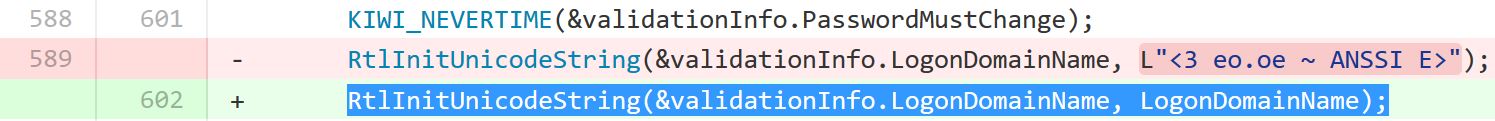
Detecting forged Kerberos tickets, including Golden Tickets and Silver Tickets, by identifying for domain field anomalies is likely no longer possible. As of the Mimikatz update dated 1/5/2016, forged Kerberos tickets no longer include a domain anomaly since the netbios domain name is placed in the domain component of the Kerberos ticket.
This means that attackers using the Mimikatz version dated 1/5/2016 and/or Invoke-Mimikatz with this updated DLL will likely not trigger alerts based on the invalid domain fields I identified in the past.
User behavior analysis tools such as Microsoft Advanced Threat Analytics (ATA) is the best current method to detect this and other attack types. The best way to detect Golden Tickets is to correlate TGS requests to prior TGT requests. If there’s no prior TGT request (within a threshold), then the TGS request may be related to a Golden Ticket.
Golden Ticket event from using Mimikatz dated (11/2015): Has the an invalid domain value (“<3 eo.oe – ANSSI E>“)
Golden Ticket event from using Mimikatz dated (1//05/2015): Has the correct domain value (“RD”)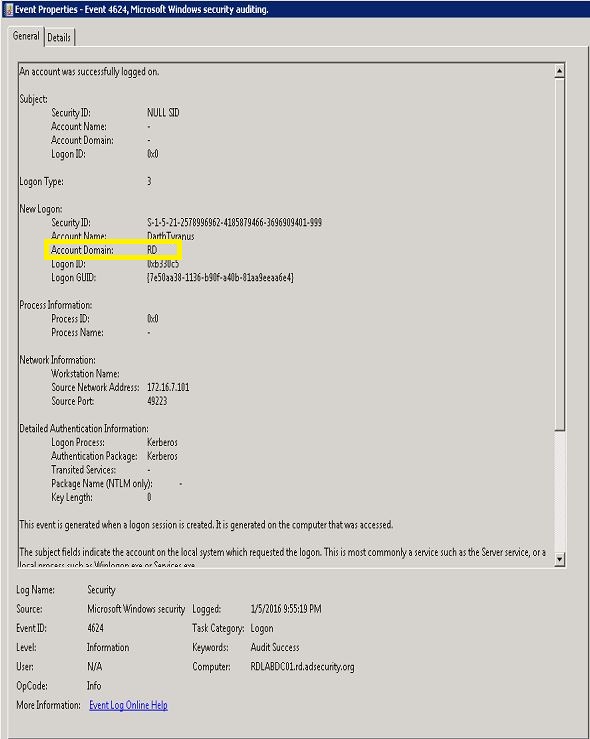
I have updated the appropriate references:

Recent Comments