This week let’s look at Active Directory domain permissions which are configured on the domain root and apply to the domain. There are many different type of concerning permissions, but let’s look at the most egregious.
Tag: ActiveDirectory
Oct 08 2025
Active Directory Security Tip #13: Reviewing Foreign Security Principals (FSPs)
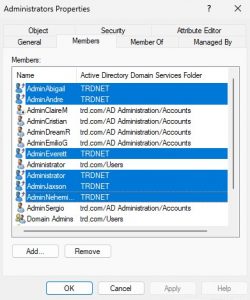
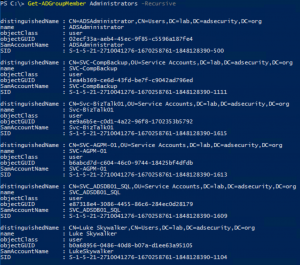
Review the membership of groups for accounts and groups from another Active Directory forest (technically another domain, but using forest here). These are called “Foreign Security Principals” (FSPs) like the ones highlighted in the image. These FSPs are accounts that exist in another forest but have rights in the AD forest. Any FSPs should be …
Sep 16 2025
Active Directory Lab Build Script
Over the summer, I rebuilt my Active Directory lab environment with multiple regional domains. Instead of manually configuring common issues, I decided to create a PowerShell script to do this for me.
Aug 18 2025
The Art of the Honeypot Account: Making the Unusual Look Normal
This article was originally posted on the Trimarc Content Hub on August 6, 2020.Updated here with authentication PowerShell code on August 18, 2025. ADSecurity.org is the new home for this article and all updates will occur here. I have had the idea for a post describing how to best create a honeypot (or honeytoken) account …
Jul 06 2016
DEF CON 24 (2016) Talk – Beyond the MCSE: Red Teaming Active Directory
This August at DEF CON 24, I will be speaking about Active Directory security evaluation in my talk “Beyond the MCSE: Red Teaming Active Directory”. This talk is focused on the Red side of AD security, specifically how to best evaluate the security of AD and quickly identify potential security issues. Whether you perform “Red …
Mar 14 2016
Sneaky Active Directory Persistence #17: Group Policy
The content in this post describes a method through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. Complete list of Sneaky Active Directory Persistence Tricks posts This post explores how an attacker could leverage the built-in Active Directory management capability called Group Policy …



Recent Comments