Microsoft supported backups of Active Directory are very important to have. For backing up Domain Controllers, this is typically a System State backup. Why a Microsoft supported backup? If you are using a backup solution that isn’t fully AD aware, performing a restore may involve getting Microsoft involved and that costs $$. I know companies …
September 2025 archive
Sep 20 2025
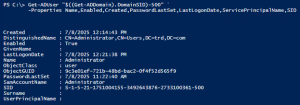
Active Directory Security Tip #8: The Domain Kerberos Service Account – KRBTGT
The domain Kerberos service account, KRBTGT (https://adsecurity.org/?p=483), is an important account since it is used to sign & encrypt Kerberos tickets. The account is disabled and the password doesn’t change except when moving from Windows 2000/2003 to Windows Server 2008 (or newer). This is a highly privileged account and if an attacker can gain knowledge …
Sep 19 2025
Active Directory Security Tip #7: The Tombstone Lifetime
The Tombstone lifetime (TSL) in Active Directory is the limit as to how long a deleted object can remain in AD. The original value was 60 (days). Windows versions since Windows 2003 SP2 have this set to 180 (days). Note that this also affects backups, how long a backup is valid and replication – if …
Sep 16 2025
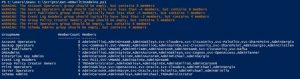
Active Directory Security Tip #4: Default/Built-In Active Directory Groups
There are several default/built-in privileged groups that should be reviewed: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups PowerShell Script leveraging the Active Directory PowerShell module: https://github.com/PyroTek3/Misc/blob/main/Get-ADBuiltInAdmins.ps1
Sep 16 2025
Active Directory Lab Build Script
Over the summer, I rebuilt my Active Directory lab environment with multiple regional domains. Instead of manually configuring common issues, I decided to create a PowerShell script to do this for me.
Sep 15 2025
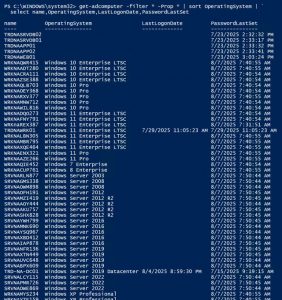
Active Directory Security Tip #3: Computer Accounts
Active Directory computers should be reviewed about once a year. Old operating systems can hold back security progress like keeping SMBv1 and NTLMv1 active. Inactive computers should be discovered and disabled when no longer in use (and eventually removed). The OperatingSystem & PasswordLastSet attributes are self-explanatory, though we can use the LastLogonDate which represents the …
Sep 15 2025
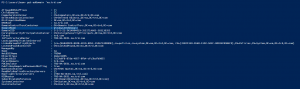
Active Directory Forest & Domain Level Capabilities
An important Active Directory setting determines what security capabilities are available which relates to the level of the forest and/or domain. This post collects the relevant capabilities of Windows domain and forest functional levels.You can easily check the domain & Forest functional levels using the Active Directory PowerShell module using the cmdlets Get-ADForest & Get-ADDomain. …
- 1
- 2



Recent Comments