An important Active Directory setting determines what security capabilities are available which relates to the level of the forest and/or domain. This post collects the relevant capabilities of Windows domain and forest functional levels.
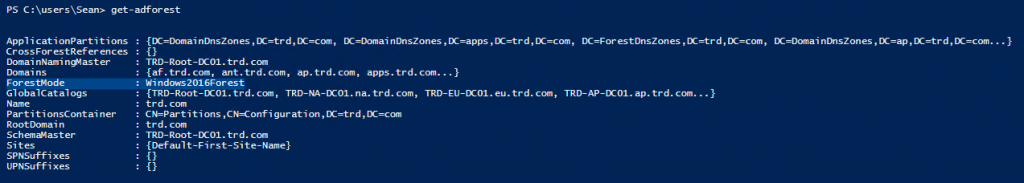
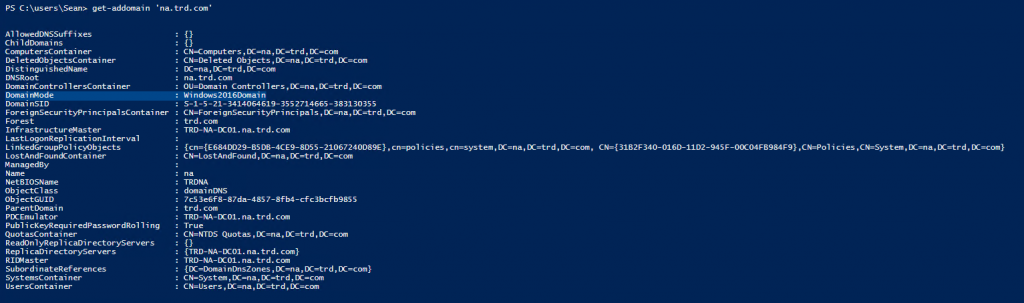
You can easily check the domain & Forest functional levels using the Active Directory PowerShell module using the cmdlets Get-ADForest & Get-ADDomain.
Get-ADForest
Get-ADDomain
There is a .Net function to get the AD Forest Mode:
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().ForestMode
There’s also a .Net function to get the AD Domain Mode:
[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain().DomainMode
Forest Functional Level Features:
- Windows 2000
- Windows 2003
- Forest trust
- Domain rename
- Linked-value replication makes it possible for you to change group membership to store and replicate values for individual members instead of replicating the entire membership as a single unit. Storing and replicating the values of individual members uses less network bandwidth and fewer processor cycles during replication, and prevents you from losing updates when you add or remove multiple members concurrently at different domain controllers.
- The ability to deploy a read-only domain controller (RODC)
- The intersite topology generator (ISTG) uses improved algorithms that scale to support forests with a greater number of sites than AD DS can support at the Windows 2000 forest functional level. The improved ISTG election algorithm is a less-intrusive mechanism for choosing the ISTG at the Windows 2000 forest functional level.
- The ability to create instances of the dynamic auxiliary class named dynamicObject in a domain directory partition
- The ability to convert an inetOrgPerson object instance into a User object instance, and to complete the conversion in the opposite direction
- The ability to create instances of new group types to support role-based authorization. These types are called application basic groups and LDAP query groups.
- Deactivation and redefinition of attributes and classes in the schema. The following attributes can be reused: ldapDisplayName, schemaIdGuid, OID, and mapiID.
- Domain-based DFS namespaces running in Windows Server 2008 Mode, which includes support for access-based enumeration and increased scalability.
- Windows 2008
- No additional features
- Windows 2008 R2
- Active Directory Recycle Bin, which provides the ability to restore deleted objects in their entirety while AD DS is running.
- Windows 2012
- No additional features
- Windows 2012 R2
- No additional features
- Windows 2016
- Privileged access management (PAM) using Microsoft Identity Manager (MIM)
- Windows 2019
- No additional features
- Windows 2022
- No additional features
- Windows 2025
- No additional features
Domain Functional Level Features:
- Windows 2000
- Universal groups for both distribution and security groups.
- Group nesting
- Group conversion, which allows conversion between security and distribution groups
- Security identifier (SID) history
- Windows 2003
- Domain Controller rename
- The lastLogonTimestamp attribute is updated with the last logon time of the user or computer. This attribute is replicated within the domain.
- The ability to set the userPassword attribute as the effective password on inetOrgPerson and user objects
- The ability to redirect Users and Computers containers
- The ability for Authorization Manager to store its authorization policies in AD DS
- Constrained delegation makes it possible for applications to take advantage of the secure delegation of user credentials by means of Kerberos-based authentication. You can restrict delegation to specific destination services only.
- Selective authentication makes it is possible for you to specify the users and groups from a trusted forest who are allowed to authenticate to resource servers in a trusting forest.
- Windows 2008
- Distributed File System (DFS) replication support for the Windows Server 2003 System Volume (SYSVOL)
- Domain-based DFS namespaces running in Windows Server 2008 Mode
- Advanced Encryption Standard (AES 128 and AES 256) support for the Kerberos protocol.
- Last Interactive Logon Information displays the following information:
- The total number of failed logon attempts at a domain-joined Windows Server 2008 server or a Windows Vista workstation
- The total number of failed logon attempts after a successful logon to a Windows Server 2008 server or a Windows Vista workstation
- The time of the last failed logon attempt at a Windows Server 2008 or a Windows Vista workstation
- The time of the last successful logon attempt at a Windows Server 2008 server or a Windows Vista workstation
- Fine-grained password policies
- Personal Virtual Desktops
- Windows 2008 R2
- Authentication mechanism assurance, which packages information about the type of logon method (smart card or user name/password) that is used to authenticate domain users inside each user’s Kerberos token. When this feature is enabled in a network environment that has deployed a federated identity management infrastructure, such as Active Directory Federation Services (AD FS), the information in the token can then be extracted whenever a user attempts to access any claims-aware application that has been developed to determine authorization based on a user’s logon method.
- Automatic SPN management for services running on a particular computer under the context of a Managed Service Account when the name or DNS host name of the machine account changes.
- Windows 2012
- The KDC support for claims, compound authentication, and Kerberos armoring KDC administrative template policy has two settings (Always provide claims and Fail unarmored authentication requests) that require Windows Server 2012 domain functional level.
- Windows 2012 R2
- DC-side protections for Protected Users. Protected Users authenticating to a Windows Server 2012 R2 domain can no longer:
- Authenticate with NTLM authentication
- Use DES or RC4 cipher suites in Kerberos pre-authentication
- Be delegated with unconstrained or constrained delegation
- Renew user tickets (TGTs) beyond the initial 4 hour lifetime
- Authentication Policies – New forest-based Active Directory policies which can be applied to accounts in Windows Server 2012 R2 domains to control which hosts an account can sign-on from and apply access control conditions for authentication to services running as an account.
- Authentication Policy Silos – New forest-based Active Directory object, which can create a relationship between user, managed service and computer, accounts to be used to classify accounts for authentication policies or for authentication isolation.
- DC-side protections for Protected Users. Protected Users authenticating to a Windows Server 2012 R2 domain can no longer:
- Windows 2016
- DCs can support automatic rolling of the New Technology LAN Manager (NTLM) and other password-based secrets on a user account configured to require public key infrastructure (PKI) authentication. This configuration is also known as Smart card required for interactive logon.
- DCs can support allowing network NTLM when a user is restricted to specific domain-joined devices.
- Kerberos clients successfully authenticating with the PKInit Freshness Extension get the fresh public key identity security identifier (SID).
- Windows 2019
- No additional features
- Windows 2022
- No additional features
- Windows 2025
- Database 32k pages optional feature.
References:
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels

Recent Comments