I have mentioned in several presentations that Kerberos delegation is impersonation. Kerberos delegation is used when a service (ex. web server) needs to impersonate a user when connecting to a resource (ex. database).
There are a 4 types of Kerberos delegation:
- Unconstrained – impersonate authenticated user to any Kerberos service [Risk of Unconstrained delegation]
- Constrained – impersonate authenticated user to specific Kerberos services
- Kerberos Constrained Delegation Protocol Transition – impersonate any user account to specific Kerberos services
- Resource-based Constrained Delegation – enables delegation configured on the resource instead of the account
Unconstrained delegation should be converted to constrained delegation due to security concerns. Any Kerberos delegation that is no longer required should be removed. If there’s no associated Kerberos service principal name, Kerberos authentication isn’t working and this should be fixed or removed.
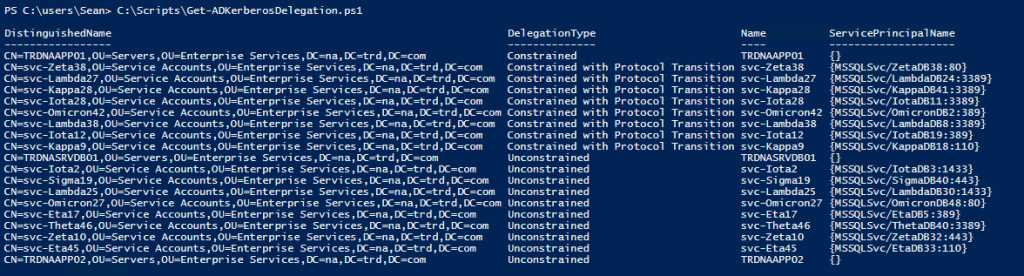
PowerShell code using the Active Directory PowerShell module:
https://github.com/PyroTek3/Misc/blob/main/Get-ADKerberosDelegation.ps1

Recent Comments