Carlos Perez (@DarkOperator) recently posted on DarkOperator.com how to use PowerShell to get data from Active Directory. He is working on an Active Directory audit PowerShell project and is documenting most of the work put into it. He also covers leveraging functions for portability and using Pester to write better PowerShell code (as well as …
Tag: PowerShellCode
Dec 15 2014
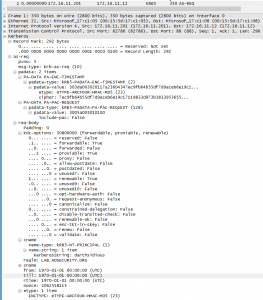
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
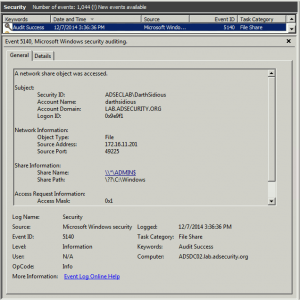
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …
Dec 05 2014
Windows Computer Primary Group IDs
Primary Group IDs are the RIDs for the Domain groups. The full list is here: Interesting Windows Computer & Active Directory Well-Known Security Identifiers (SIDs). 515 – Domain Computers 516 – Domain Controllers (writable) 521 – Domain Controllers (Read-Only) This information helps filter computer objects to return only the desired computer type. Domain Computers (Workstation …
Nov 17 2014
PowerShell: Discover Active Directory Forest Domain Controllers
Recently I needed to find all Domain Controllers in a large Active Directory forest (and see the AD Domain Functional Level for each domain). Here’s the PowerShell code which leverages the Active Directory PowerShell module cmdlets. import-module ActiveDirectory $ADForestInfo = Get-ADForest $ADForestInfoName = $ADForestInfo.Name $ADForestInfoDomains = $ADForestInfo.Domains $ADForestInfoForestMode = $ADForestInfo.ForestMode $AllDCs = $Null ForEach …
Nov 16 2014
PowerShell 101: Easy Script Timing
There are times when you want to know how long it takes for a script to run. One of the Measure-* cmdlets can be useful, but there is a simpler way to time how long it takes to run a script (or piece of code). The StopWatch .NET method is an ideal method for script …
Nov 03 2014
PowerShell Code: ADSI Convert Domain Distinguished Name to Fully Qualified Domain Name
Convert Domain Distinguished Name to Fully Qualified Domain Name: $ADObjectDN = “CN=Object1,OU=OrgUnit1,DC=child,DC=domain,DC=com” [array]$ADObjectDNArray = $ADObjectDN -Split(“,DC=”) [int]$DomainNameFECount = 0 ForEach ($ADObjectDNArrayItem in $ADObjectDNArray) { IF ($DomainNameFECount -gt 0) …
Nov 02 2014
Windows 8: Using PowerShell to Decrypt Wireless SSID Passwords with NetSH
Show the saved password for SSID named “SSID_NAME” in Windows 8. ((netsh wlan show profiles name=”SSID_NAME” key=clear | select-string “Key Content” ) -split(” Key Content : “))[1]
Oct 15 2014
PowerShell Function: Get-ADAuthGroups
Here’s a PowerShell Function that leverages Active Directory .Net to get a list of the AD authorization groups. This is extremely useful to get a complete list of security groups that comprise a user’s AD Kerberos token without having to loop or recurse AD groups. Function GetAuthGroups { Param ( $AccountID, [switch]$CountAuthGroups, [Switch]$ReturnGroups = …
- 1
- 2

Recent Comments