Many organizations are moving to the cloud and this often requires some level of federation. Federation, put simply, extends authentication from one system (or organization) to another. Gerald Steere (@Darkpawh) and I spoke about cloud security at DEF CON in July 2017. Presentation slides and video are here: “Hacking the Cloud” One of the key …
Category: Technical Reading
Nov 17 2015
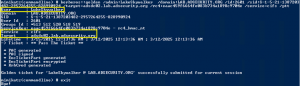
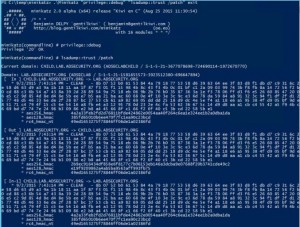
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. This post continues this …
Jul 15 2015
It’s All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
In early 2015, I theorized that it’s possible to forge inter-realm (inter-trust) Kerberos tickets in a similar manner to how intra-domain TGTs (Golden Tickets) and TGSs (Silver Tickets) are forged. Around the same time, Benjamin Delpy updated Mimikatz to dump trust keys from a Domain Controller. Soon after, Mimikatz gained capability to forge inter-realm trust …
Apr 12 2015
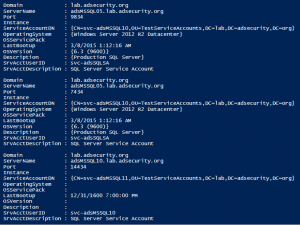
SPN Scanning – Service Discovery without Network Port Scanning
The best way to discover services in an Active Directory environment is through what I call “SPN Scanning.” The primary benefit of SPN scanning for an attacker over network port scanning is that SPN scanning doesn’t require connections to every IP on the network to check service ports. SPN scanning performs service discovery via LDAP …
Nov 11 2014
Another SSL Attack: POODLE
SSL used to be the foremost method for securing web communications until around 1999 when TLS 1.0 was released. BEAST demonstrated inherent flaws in the aging SSL 3 protocol (RC4!). Now, POODLE demonstrates that SSL3 needs to be disabled on the client AND server side. Note that the chance of this specific issue being the …
Nov 08 2014
Hack Attack Method Whitepapers
The best way to develop the best defense is to study the offense’s methods. Here are several recent reports that detail current modern network attacks: Mandiant APT Whitepaper Microsoft Security Intelligence Report Verizon Enterprise DBIR 2014
Sep 22 2014
Powershell Filter Operators
Once you get used to Powershell, you will want to do more and more with it. One of the keys to leveraging the power of PowerShell is filters. PowerShell commandlets all support filters (well, most of them anyway). This means you can drill down to resulting data subsets. If you run into commandlets that don’t …
Aug 25 2014
Microsoft Enhanced Mitigation Experience Toolkit (EMET) 5 Protection Methods
Microsoft Enhanced Mitigation Experience Toolkit (EMET) v5 security technology which I outlined in a previous post has several protection methods which will be detailed here. According to my sources at Microsoft 😉, EMET can be installed on workstations and servers (testing is always highly recommended before placing in production). Given the tremendous security improvements when …
May 06 2014
Windows Server 2012 MCSM Reading List
Here’s a link to download the MCM/MCSM Directory Services Reading List document that I developed for the MCSM Directory Services (Windows Server 2012) program and was created after the MCSM Directory Services (Windows Server 2012) test questions were written. It is based on the original one created for the MCM DS program provided to candidates. …
Apr 29 2014
AD Reading: How Key Active Directory Components Work
The following links provide in-depth information on how key Active Directory components work. AD Data Store Windows Server 2003 Active Directory Branch Office Guide Bridgehead Server Selection (Windows 2008 R2) AD Replication Model Certificate Revocation & Status Checking Core Group Policy DNS How DNS Support for AD works Windows 2000 DNS DFS Fine-Grained Password Policy …
- 1
- 2

Recent Comments