During the Summer of 2024, I had a talk at Troopers called “A Decade of Active Directory Attacks:What We’ve Learned & What’s Next” (Slides & Video) where I focused on the key milestones of Active Directory security (history). This article covers my “decade of Active Directory attacks” in some detail which was correlated with public …
Tag: MimikatzDCSync
Jan 03 2016
How Attackers Dump Active Directory Database Credentials
I previously posted some information on dumping AD database credentials before in a couple of posts: “How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller” and “Attack Methods for Gaining Domain Admin Rights in Active Directory“. This post covers many different ways that an attacker can dump credentials from Active Directory, both …
Nov 17 2015
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. This post continues this …
Sep 25 2015
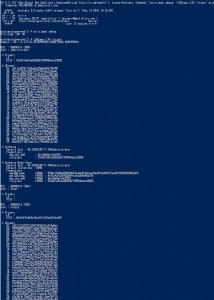
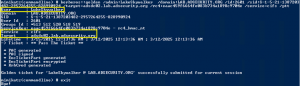
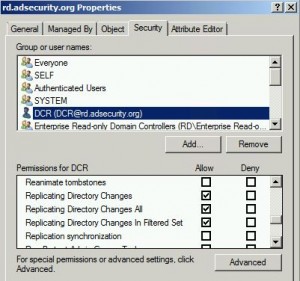
Mimikatz DCSync Usage, Exploitation, and Detection
Note: I presented on this AD persistence method at DerbyCon (2015). A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller. DCSync was written by Benjamin Delpy and Vincent Le Toux. The exploit method prior to DCSync was …

Recent Comments