I previously posted some information on dumping AD database credentials before in a couple of posts: “How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller” and “Attack Methods for Gaining Domain Admin Rights in Active Directory“. This post covers many different ways that an attacker can dump credentials from Active Directory, both …
Tag: PowerShellRemoting
Nov 17 2015
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. This post continues this …
Apr 12 2015
SPN Scanning – Service Discovery without Network Port Scanning
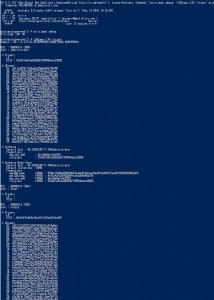
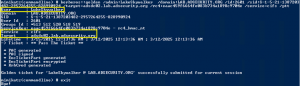
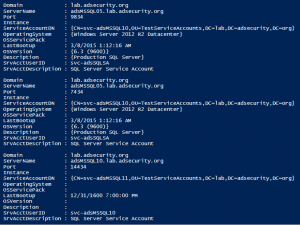
The best way to discover services in an Active Directory environment is through what I call “SPN Scanning.” The primary benefit of SPN scanning for an attacker over network port scanning is that SPN scanning doesn’t require connections to every IP on the network to check service ports. SPN scanning performs service discovery via LDAP …

Recent Comments