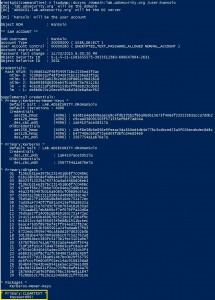
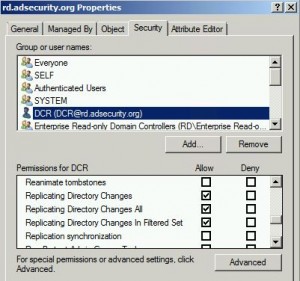
The two key goals of any attack is access and persistence. This post covers elements of each. In a post-exploitation scenario where the attacker has compromised the domain or an account with delegated rights, it’s possible to dump the clear-text passwords of admins without being a Domain Admin*. This method requires the Active Directory Domain …
Tag: DCSyncRights
Sep 25 2015
Mimikatz DCSync Usage, Exploitation, and Detection
Note: I presented on this AD persistence method at DerbyCon (2015). A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller. DCSync was written by Benjamin Delpy and Vincent Le Toux. The exploit method prior to DCSync was …

Recent Comments