Microsoft provided several Active Directory PowerShell cmdlets with Windows Server 2008 R2 (and newer) which greatly simplify tasks which previously required putting together lengthy lines of code involving ADSI.
On a Windows client, install the Remote Sever Administration Tools (RSAT) and ensure the Active Directory PowerShell module is installed.
On a Windows server (2008 R2 or newer), run the following commands in a PowerShell console (as an Adminsitrator):
Import-Module ServerManager ; Add-WindowsFeature RSAT-AD-PowerShell
Here’s my (poor) ADSI example:
$UserID = “JoeUser” $root = [ADSI]'' $searcher = new-object System.DirectoryServices.DirectorySearcher($root) $searcher.filter = "(&(objectClass=user)(sAMAccountName= $UserID))" $user = $searcher.findall() $user
Here’s the same thing with the AD PowerShell cmdlet:
Import-module ActiveDirectory
$UserID = “JoeUser”
Get-ADUser $UserID –property *
Note that with PowerShell version 3 and newer, you don’t need to run the first line since Powershell will identify the necessary module and auto load it.
Once you have the Active Directory PowerShell module loaded, you can do cool stuff like browse AD like a file system
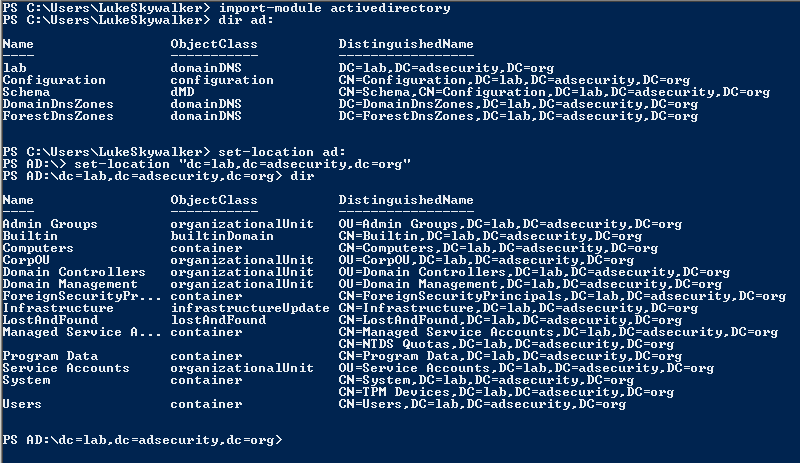
Finding Useful Commands (Cmdlets):
Discover available PowerShell modules: Get-Module -ListAvailable
Discover cmdlets in a PowerShell module: Get-Command -module ActiveDirectory
PowerShell AD Module Cmdlets:
- Windows Server 2008 R2: 76 cmdlets
- Windows Server 2012: 135 cmdlets
- Windows Server 2012 R2: 147 cmdlets
- Windows Server 2016: 147 cmdlets
(Get-Command -module ActiveDirectory).count
Finding Active Directory Flexible Master Single Operation (FSMO) Roles:
Active Directory Module:
-
(Get-ADForest).SchemaMaster
-
(Get-ADForest).DomainNamingMaster
-
(Get-ADDomain).InfrastructureMaster
-
(Get-ADDomain).PDCEmulator
-
(Get-ADDomain).RIDMaster
.NET Calls:
-
([System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest()).SchemaRoleOwner
-
([System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest()).NamingRoleOwner
-
([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).InfrastructureRoleOwner
-
([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).PdcRoleOwner
-
([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).RidRoleOwner
Active Directory PowerShell Module Cmdlet Examples:
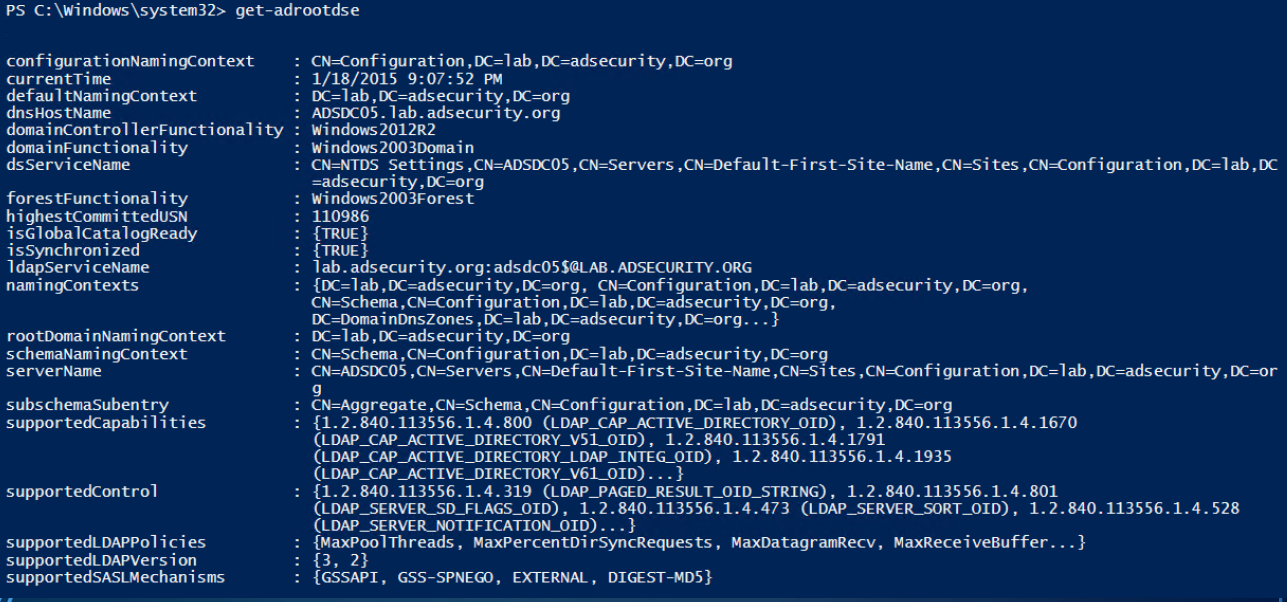
Get-RootDSE gets information about the LDAP server (the Domain Controller) and displays it. There’s some interesting information in the results like what OS the DC is running.
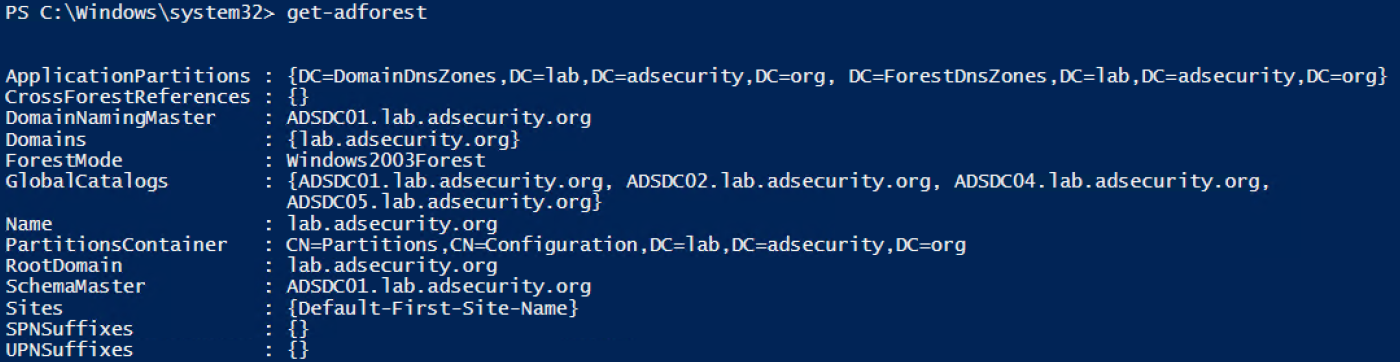
Get-ADForest provides information about the Active Directory forest the computer you run the command is in.
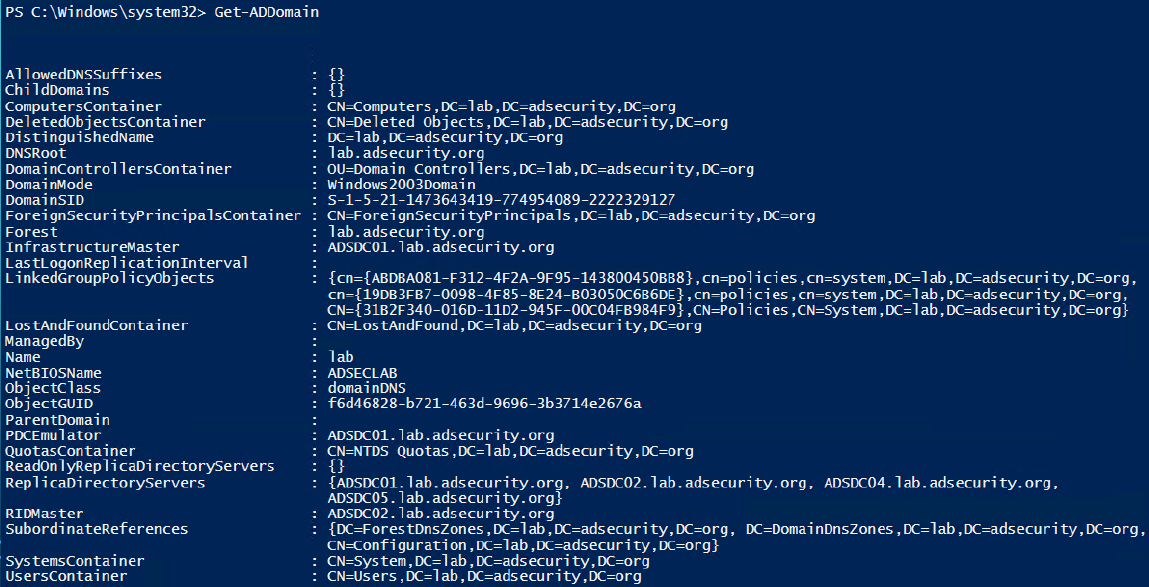
Get-ADDomain provides information about the current domain you are in.
Get-ADDomainController provides computer information specific to Domain Controllers.
This cmdlet makes it easy to find all DCs in a specific site or running an OS version.
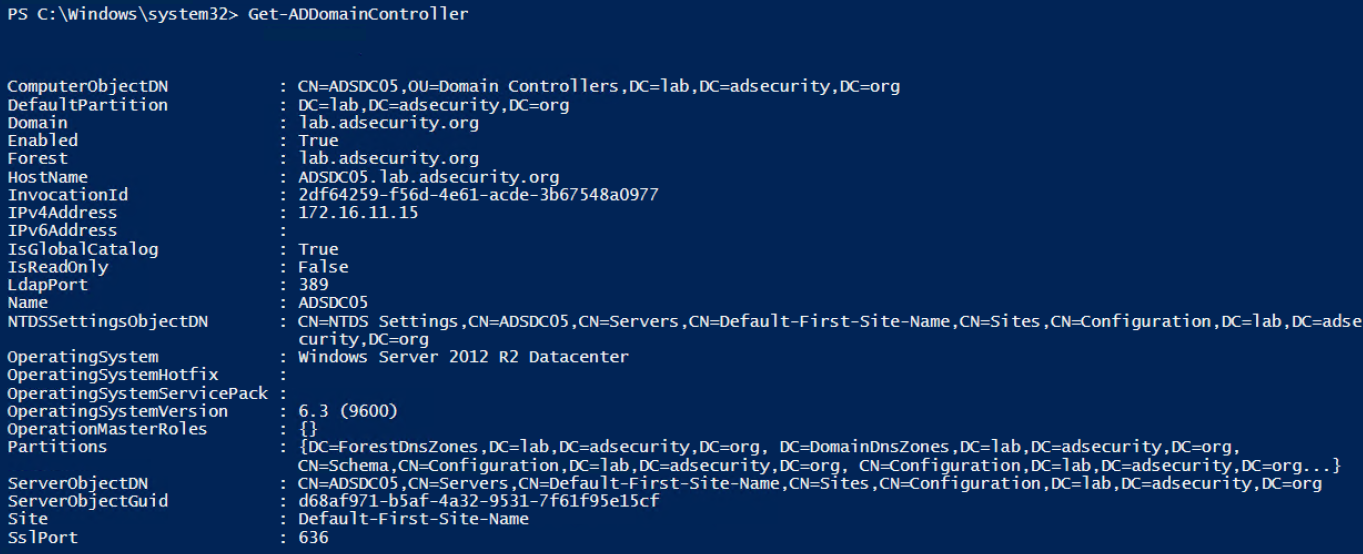
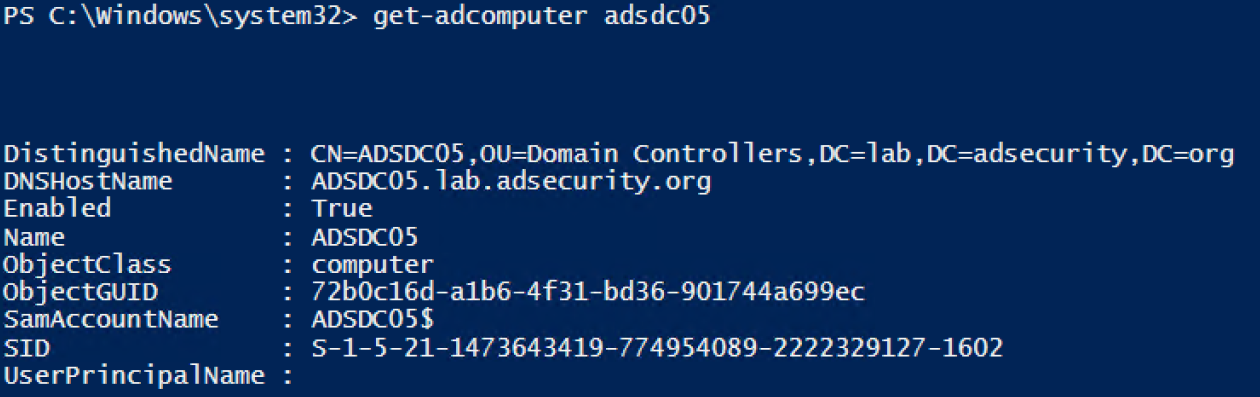
Get-ADComputer provides most of what you would want to know about a computer object in AD.
Run with “-Prop *” to show all standard properties.
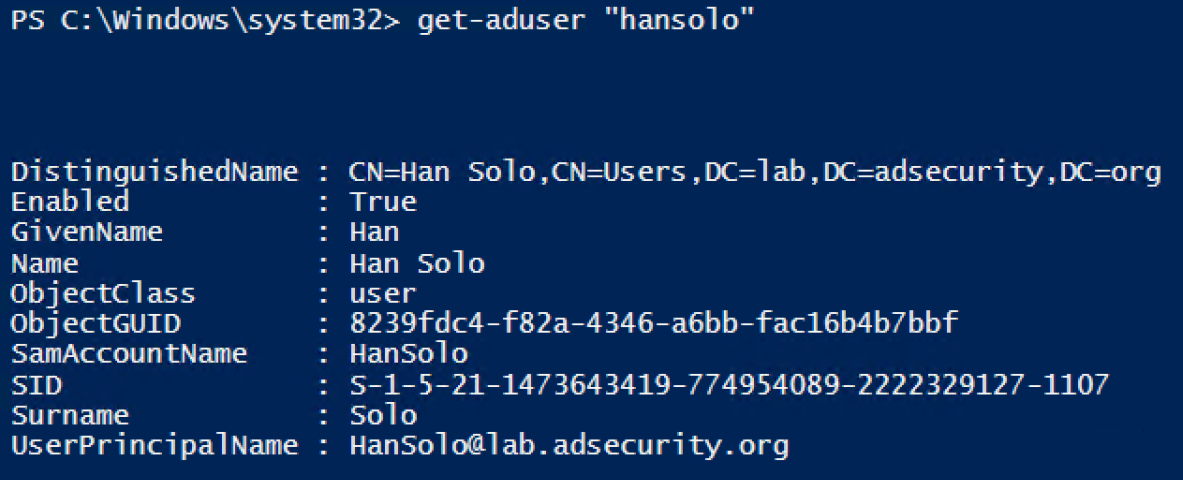
Get-ADUser provides most of what you want to know about an AD user.
Run with “-Prop *” to show all standard properties.
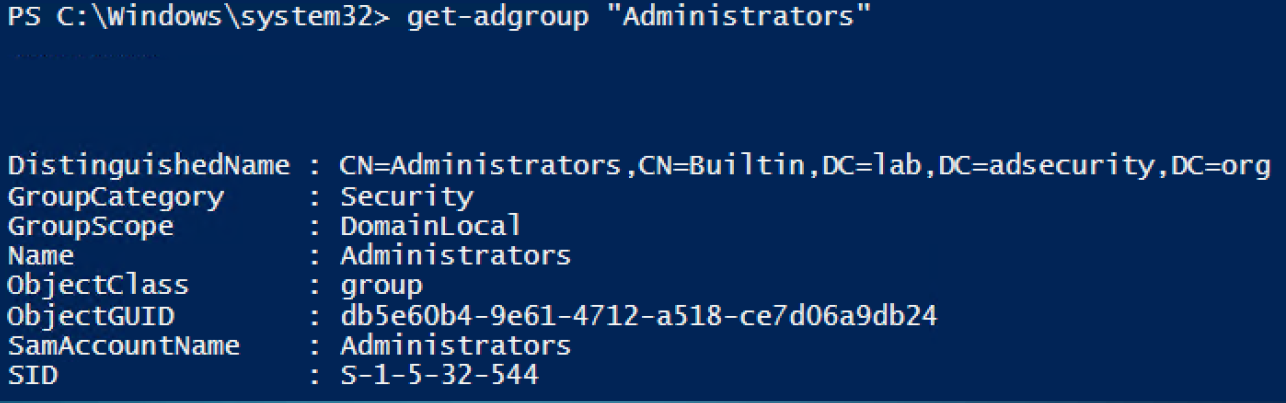
Get-ADGroup provides information about an AD group. Find all security groups by running:
Get-ADGroup -Filter {GroupCategory -eq ‘Security}
Get-ADGroupMember enumerates and returns the group members. Use the Recursive parameter to include all members of nested groups.
Get-ADGroupMember ‘Administrators’ -Recursive
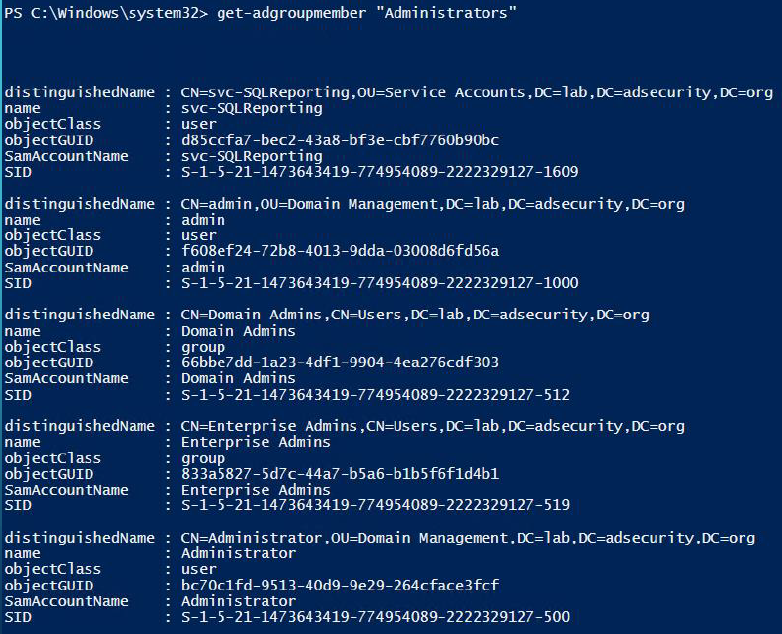
These cmdlets are useful to identify situations that previously required purchasing a product or custom scripting.
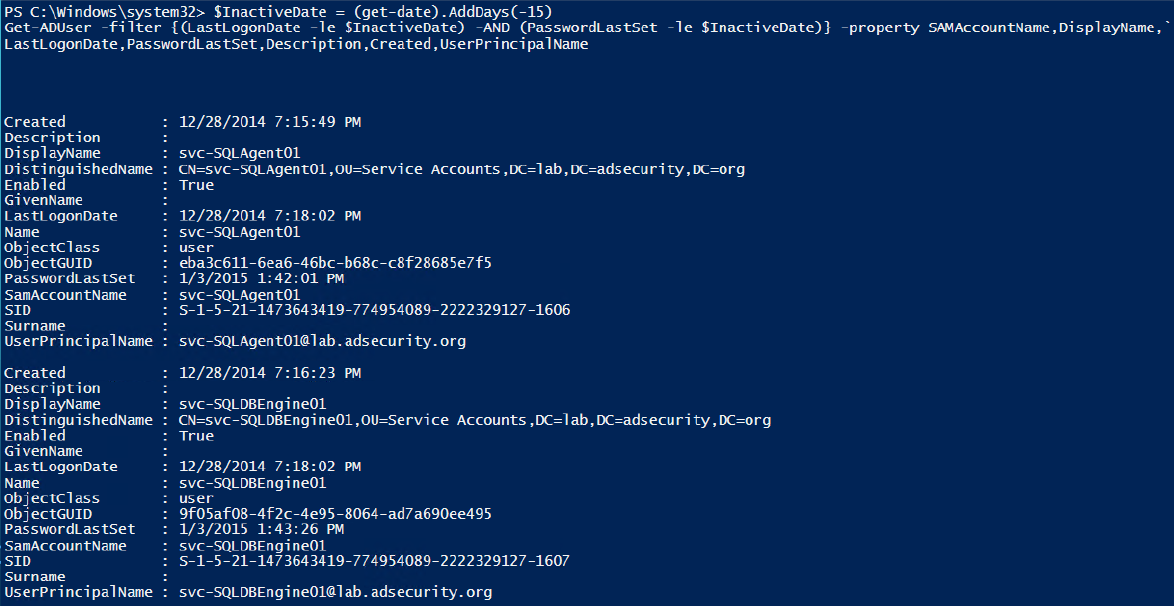
The following examples find inactive (stale) computers and users – accounts that haven’t changed their passwords in the last 10 days. Note that this is a lab example. For real-world checks, change this to 60 to 90 days for computers and 180 – 365 days for users.
Find inactive computers.
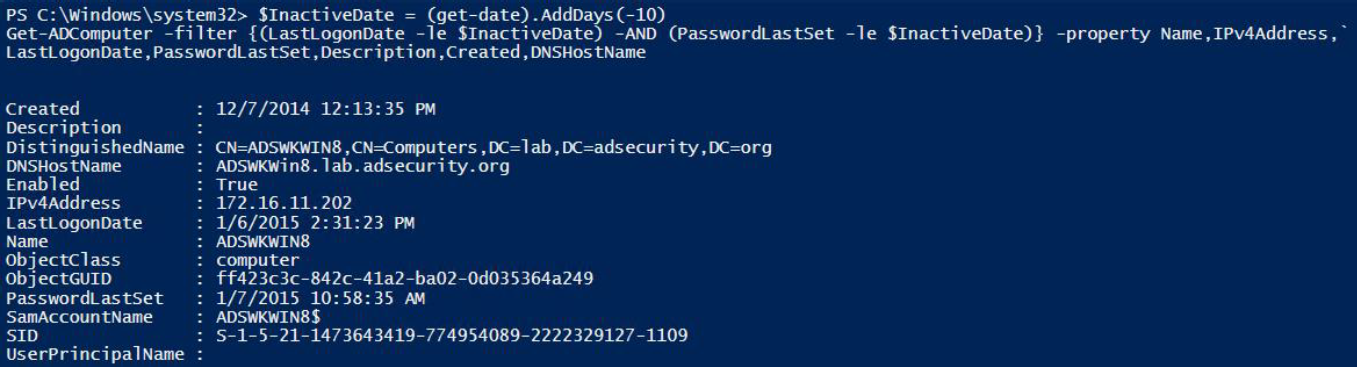
Find inactive users.
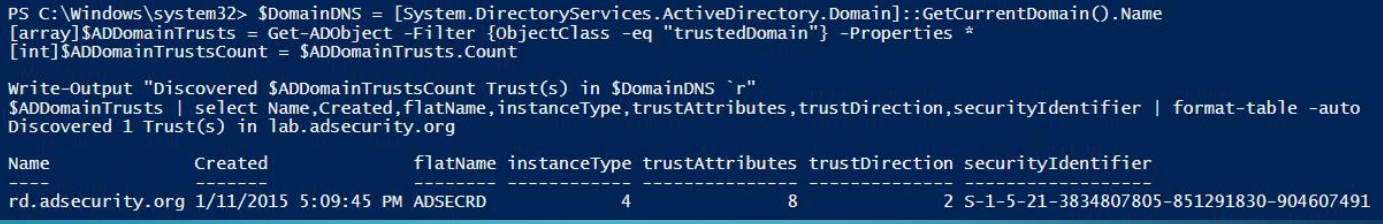
Enumerate Domain Trusts
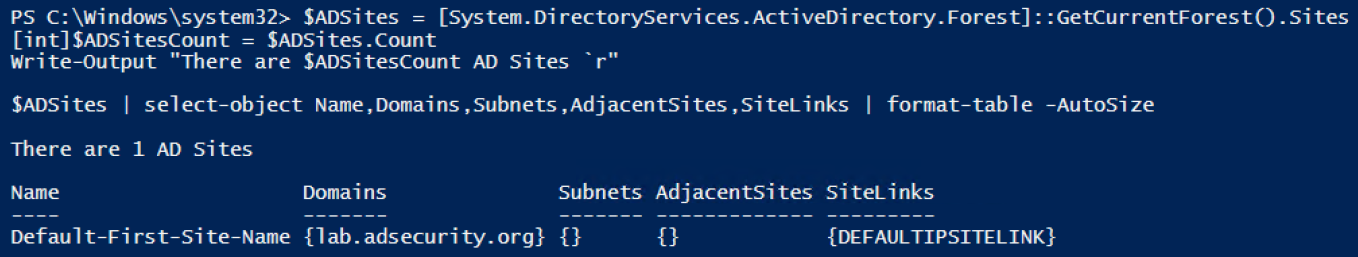
Get AD site information.
Note that the Windows 2012 module includes cmdlet for sites (Get-ADReplicationSite*).
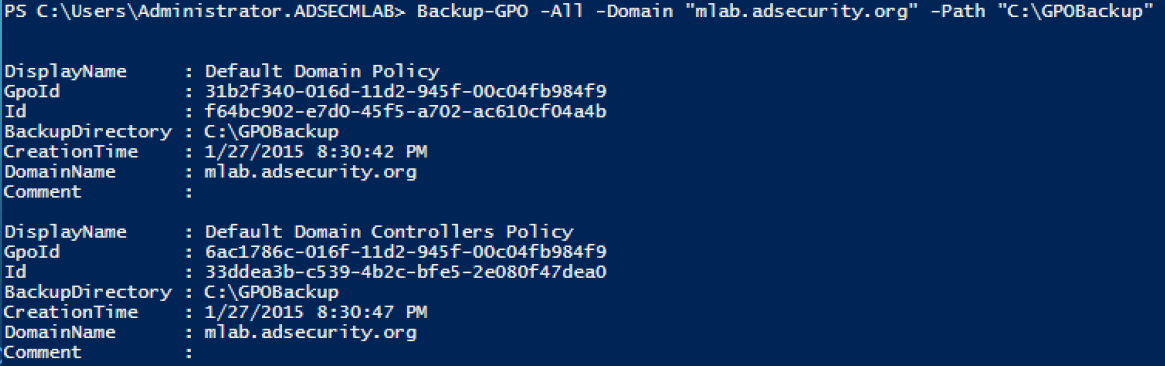
Backup domain GPOs
Note this requires that the Group Policy PowerShell module is installed, which is separate from the Active Directory module.
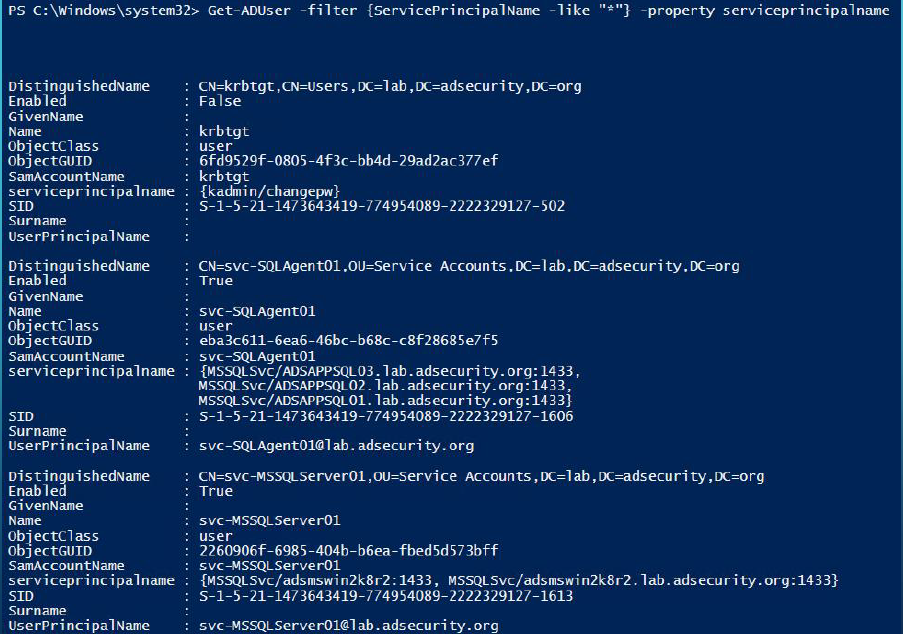
Find AD Kerberos Service Accounts
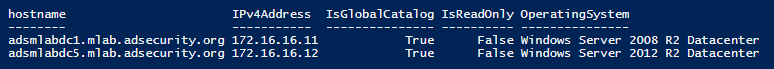
Inventory Domain Controllers
Get-ADDomainController–filter * | `select hostname,IPv4Address,IsGlobalCatalog,IsReadOnly,OperatingSystem | `format-table -auto
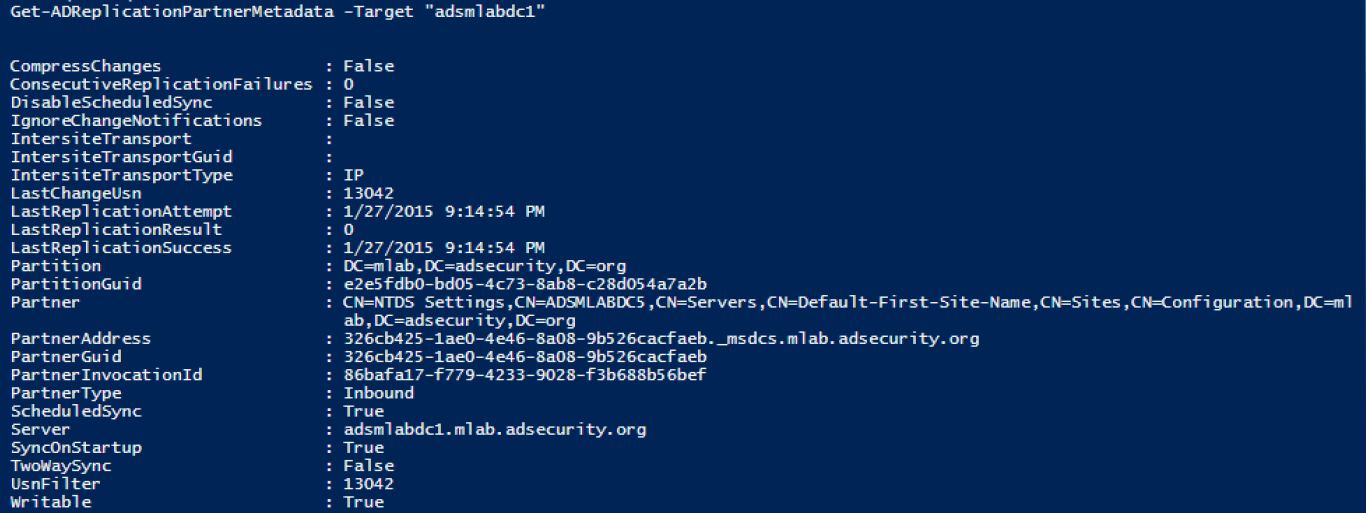
Get-ADReplicationPartnerMetadata (Windows Server 2012 and newer)
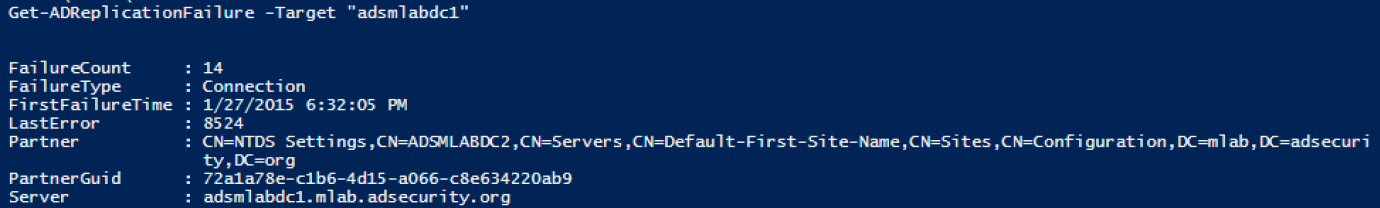
Get-ADReplicationPartnerFailure provides information on DC replication failure status.
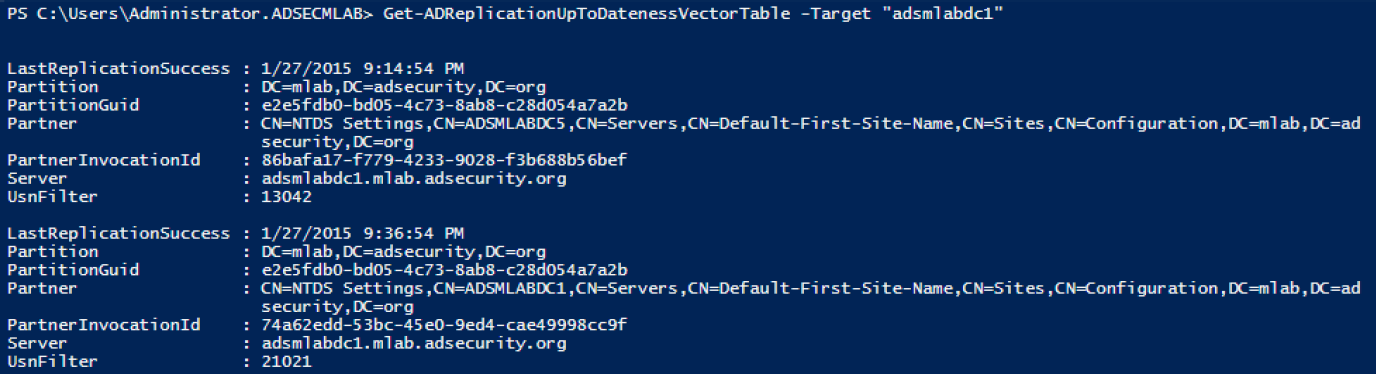
Get-ADReplicationUptodatenessVectorTable tracks replication status between Domain Controllers.
These examples and more are in these presentation slides:
http://adsecurity.org/wp-content/uploads/2015/04/NoVaPowerShellUsersGroup2015-ActiveDirectoryPowerShell.pdf

Recent Comments