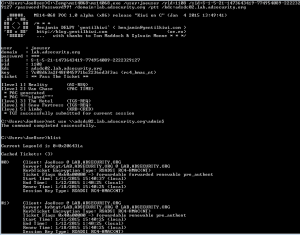
There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Tag: RunAs
Jan 01 2016
Attack Methods for Gaining Domain Admin Rights in Active Directory
- ActiveDirectory, administratorpassword, AESprivatekey, AESsharedsecret, cpassword, CredentialTheft, CredentialTheftShuffle, DomainAdmins, DomainController, DumpCredentiasls, DumpLSASS, EnterpriseAdmins, Get-GPPPassword, GoldenTickets, GPP, GroupPolicyPreferences, groups.xml, IFM, InstallFromMedia, KB2962486, KB3011780, Kekeo, Kerberoast, Kerberos, KerberosHacking, LAPS, lateralmovement, localadministratoraccountpassword, LSASS, LSASSDumpFile, MicrosoftLAPS, mimikatz, MS14068, ms14068.exe, MS14068Exploit, MSDN, ntds.dit, PAWS, Persistence, PowerSploit, PyKEK, RC4_HMAC_MD5, RDP, RunAs, scheduledtasks.xml, separateAdminWorkstation, ServicePrincipalName, Services.xml, SPN, systemcompromise, SYSVOL, TGS, TGSCracking, TGT, xml
- 2 comments
Recent Posts
Active Directory & Entra ID Security Services
Have concerns about your Active Directory environment and/or Entra ID tenant?
We help enterprises improve their security posture.
Popular Posts
- AD Reading: Windows Server 2019 Active Directory Features
- PowerShell Encoding & Decoding (Base64)
- Attack Methods for Gaining Domain Admin Rights in…
- Kerberos & KRBTGT: Active Directory’s…
- Finding Passwords in SYSVOL & Exploiting Group…
- Securing Domain Controllers to Improve Active…
- Securing Windows Workstations: Developing a Secure Baseline
- Detecting Kerberoasting Activity
- Mimikatz DCSync Usage, Exploitation, and Detection
- Scanning for Active Directory Privileges &…
Categories
- ActiveDirectorySecurity
- Apple Security
- Cloud Security
- Continuing Education
- Entertainment
- Entra ID Security
- Exploit
- Hacking
- Hardware Security
- Hypervisor Security
- Interview
- Linux/Unix Security
- Malware
- Microsoft Security
- Mitigation
- Network/System Security
- PowerShell
- RealWorld
- Security
- Security Conference Presentation/Video
- Security Recommendation
- Technical Article
- Technical Reading
- Technical Reference
- TheCloud
- Vulnerability
Tags
ActiveDirectory
Active Directory
ActiveDirectorySecurity
Active Directory Security
ActiveDirectorySecurityTip
ADReading
ADSecurity
AD Security
Azure
DCSync
DomainController
GoldenTicket
HyperV
Invoke-Mimikatz
KB3011780
KDC
Kerberoast
Kerberos
KerberosHacking
KRBTGT
LAPS
LSASS
MCM
MicrosoftEMET
MicrosoftWindows
mimikatz
MS14068
PassTheHash
PowerShell
PowerShellCode
PowerShellHacking
PowerShellv5
PowerSploit
PowerView
Presentation
Security
SilverTicket
SneakyADPersistence
SPN
TGS
TGT
Windows10
WindowsServer2008R2
WindowsServer2012
WindowsServer2012R2
Recent Posts
Archives
- January 2026
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- December 2020
- May 2020
- January 2020
- August 2019
- March 2019
- February 2019
- October 2018
- August 2018
- May 2018
- January 2018
- November 2017
- August 2017
- June 2017
- May 2017
- February 2017
- January 2017
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- April 2016
- March 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- February 2014
- July 2013
- November 2012
- March 2012
- February 2012
Categories
- ActiveDirectorySecurity
- Apple Security
- Cloud Security
- Continuing Education
- Entertainment
- Entra ID Security
- Exploit
- Hacking
- Hardware Security
- Hypervisor Security
- Interview
- Linux/Unix Security
- Malware
- Microsoft Security
- Mitigation
- Network/System Security
- PowerShell
- RealWorld
- Security
- Security Conference Presentation/Video
- Security Recommendation
- Technical Article
- Technical Reading
- Technical Reference
- TheCloud
- Vulnerability

Recent Comments