Active Directory Recon is the new hotness since attackers, Red Teamers, and penetration testers have realized that control of Active Directory provides power over the organization. I covered ways to enumerate permissions in AD using PowerView (written by Will @harmj0y) during my Black Hat & DEF CON talks in 2016 from both a Blue Team …
Tag: SIDHistory
Sep 26 2015
Sneaky Active Directory Persistence Tricks
The content in this post links to several methods through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. While there are an infinite number of actions an attacker can perform after compromising an enterprise, there are a finite number of pathways. In this series, …
Sep 19 2015
Sneaky Active Directory Persistence #14: SID History
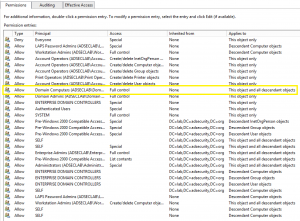
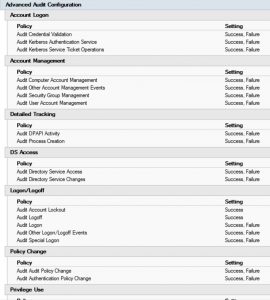
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts SID History is …
Aug 07 2015
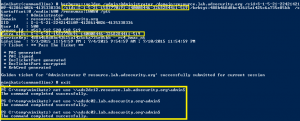
Kerberos Golden Tickets are Now More Golden
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
Aug 02 2015
DEF CON 23 (2015) Red vs Blue: Modern Active Directory Attacks & Defense Talk Detail
This week at DEF CON 23, I will be speaking about Active Directory attack & defense in my talk “Red vs Blue: Modern Active Directory Attacks & Defense”. This is the 4th iteration of this talk and includes the latest updates to attack methods and defensive strategies.This DEF CON version has a new segment I …

Recent Comments