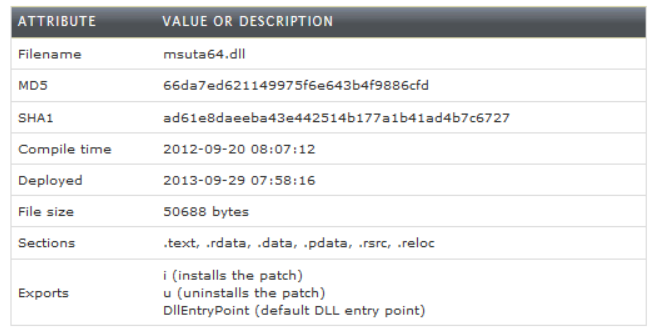
Dell SecureWorks posted about the Skeleton Key malware discovered at a customer site.
The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS.
The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins.
This enables the attacker to logon as any user they want with the master password (skeleton key) configured in the malware.
“Joe User” logs in using his usual password with no changes to his account. The attacker can log in as Joe using the skeleton key password and it is seen as a valid logon…
Key Points:
- Requires domain-level admin rights (and debug rights which admins have by default) to “patch” LSASS on a Domain Controller.
- All existing user account passwords continue working as normal.
- Adds a new password that enables the attacker to log on as any user with this password – this is the “skeleton key”.
- Active Directory Domain Controllers may experience replication issues.
- User accounts that require a smart card for authentication are not affected.
- The Skeleton Key malware currently doesn’t remain active after a reboot – rebooting the DCs removes the in-memory patch. Note that DCs are typically only rebooted about once a month.
- The Skeleton Key malware only works on the following 64-bit systems: Windows Server 2008, Windows Server 2008 R2, and Windows Server 2003 R2.
- Performs Kerberos encryption downgrade to RC4_HMAC_MD5
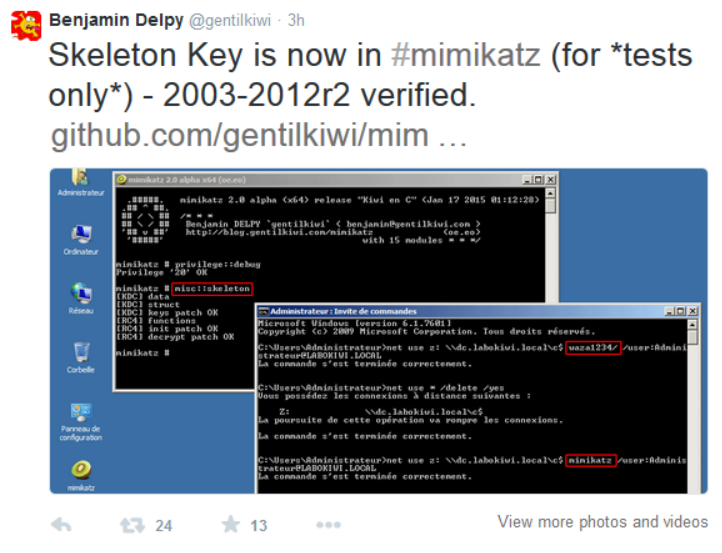
- Mimikatz now has skeleton key functionality and seems to work on all versions of Windows Server…
- Protect your Active Directory admin accounts and don’t let untrusted code run on Domain Controllers.
Skeleton Key Malware Actions:
When run, Skeleton Key performs the following tasks:
- Check for one of the following compatible 64-bit Windows versions. The malware is not compatible with 32-bit Windows versions or with Windows Server versions beginning with Windows Server 2012 (6.2).
- 6.1 (Windows 2008 R2)
- 6.0 (Windows Server 2008)
- 5.2 (Windows 2003 R2)
- Use the SeDebugPrivilege function to acquire the necessary administrator privileges to write to the Local Security Authority Subsystem Service (LSASS) process. This process controls security functions for the AD domain, including user account authentication.
- Enumerate available processes to acquire a handle to the LSASS process.
- Obtain addresses for the authentication-related functions that will be patched:
- CDLocateCSystem — located in cryptdll.dll
- SamIRetrieveMultiplePrimaryCredentials — located in samsrv.dll
- SamIRetrievePrimaryCredentials — located in samsrv.dll
- Perform OS-specific adjustments using the global variable set during the compatibility check in Step 1.
- Use the OpenProcess function to acquire a handle to the LSASS process.
- Reserve and allocate the required memory space to edit and patch the LSASS process’s memory.
- Patch relevant functions based on the operating system:
- CDLocateCSystem (all compatible Windows versions)
- SamIRetrieveMultiplePrimaryCredentials (only Windows 2008 R2 (6.1))
- SamIRetrievePrimaryCredentials (all compatible Windows versions other than Windows 2008 R2 (6.1))
Skeleton Key performs the following steps to patch each function:
- Call the VirtualProtectEx function to change the memory protection to allow writing to the required memory allocations (PAGE_EXECUTE_READWRITE, 0x40). This step allows the function’s code to be updated in memory.
- Call the WriteProcessMemory function to change the address of the target function to point to the patched code. This change causes calls to the target function to use the patch instead.
- Restore the original memory protection by calling VirtualProtectEx with the original memory protection flags. This step is likely to avoid suspicious writable and executable memory allocations.
While this issue was recently published, based on file data, it is likely it has been around for a while.
Read more about the Skeleton Key malware on the Dell SecureWorks CTU site.
Mimikatz Skeleton Key Functionality:
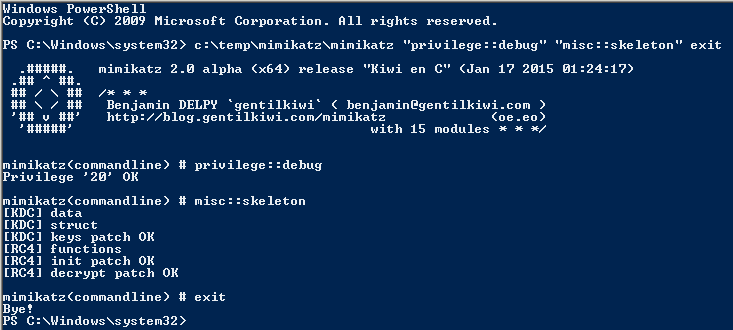
Benjamin Delpy updated Mimikatz (version 2.0 alpha, Jan 17 2015 01:24:17) with skeleton key functionality.
Mimikatz can now inject a skeleton key into LSASS on the Domain Controller by running the following command on the DC:
mimikatz.exe “privilege::debug” “misc::skeleton” exit
References:
- Dell SecureWorks Skeleton Key article
- Mimikatz Github repository
- Mimikatz Github Wiki
- Benjamin Delpy’s Blog

Recent Comments