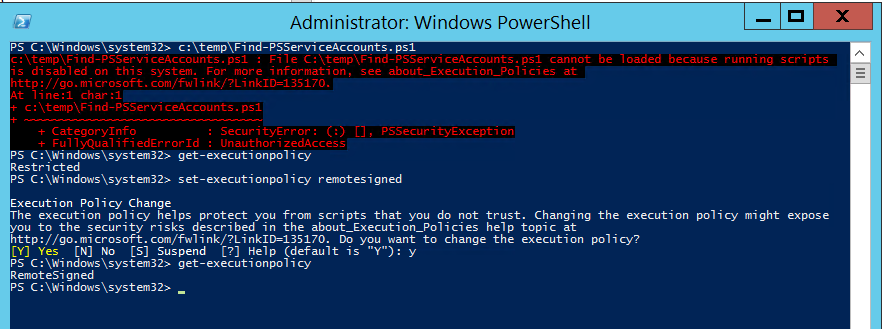
If you have worked with PowerShell recently, you may have run into an Execution Policy message:
c:\temp\Find-PSServiceAccounts.ps1 : File C:\temp\Find-PSServiceAccounts.ps1 cannot be loaded because running scripts
is disabled on this system. For more information, see about_Execution_Policies at
http://go.microsoft.com/fwlink/?LinkID=135170.
At line:1 char:1
+ c:\temp\Find-PSServiceAccounts.ps1
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (:) [], PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccess
It’s likely that Microsoft was concerned about another scripting environment where scripts run automatically without built-in controls.
However, any teeth the PowerShell execution policy may have had was significantly reduced during the development process.
From Microsoft TechNet:
It may seem odd to permit users to override an administrator-established value for the execution policy, but remember that the execution policy is intended to help stop unintended script execution. It is not intended to stop skilled users from executing scripts at all, merely to ensure that they do not do so without knowing what they are doing.
The result of this is that the Execution Policy does not provide effective security against a determined attacker with access to computers on your network.
Microsoft TechNet decribes the different options for the PowerShell Execution Policy:
The following execution policies govern scripting in Windows PowerShell:
- Restricted. Permits interactive commands only (no scripts). This is the default.
- AllSigned. Permits scripts, but requires a digital signature from a trusted publisher for all scripts and configuration files, including scripts that you write on the local computer.
- RemoteSigned. Permits scripts, but requires a digital signature from a trusted publisher for all scripts and configuration files that are downloaded from the Internet, including e-mail. A digital signature is not required for scripts that you create on the local computer.
- Unrestricted. Permits scripts, including unsigned scripts.
By default, the PowerShell exeuction policy is set to Restricted which means no script will run. Technically this is true, but it is trivial to bypass this “protection”.
The graphic shows that an admin can change the PowerShell execution policy by running set-executionpolicy.
So, an admin can change the system’s PowerShell execution policy.
However, it isn’t necessary to change the execution policy to run scripts. It is trivial to bypass the execution policy at any time.
NSPI describes 15 ways to completely bypass the PowerShell Execution Policy
I have found the following execution policy bypass methods to be the easiest:
- Run the script in PowerShell_ISE by selecting all of the code and pressing F8
- PowerShell.exe -ExecutionPolicy Bypass -File c:\temp\PowerShellScript.ps1
- PowerShell.exe -ExecutionPolicy UNRestricted -File c:\temp\PowerShellScript.ps1
- Set-Executionpolicy -Scope CurrentUser -ExecutionPolicy UnRestricted
References:

2 comments
Hi,
For other methods: https://blog.netspi.com/15-ways-to-bypass-the-powershell-execution-policy/
Author
Thank you for your comment!
In the end of the post it does reference that site:
“However, it isn’t necessary to change the execution policy to run scripts. It is trivial to bypass the execution policy at any time.
NSPI describes 15 ways to completely bypass the PowerShell Execution Policy
“