Trammell Hudson (@qrs) developed the Thunderstrike exploit based on inherent security issues with the way Apple validates, updates, and boots from the boot ROM. The exploit takes advantage of the fact that Apple allows secure booting without hardware (software checks the ROM, but doesn’t perform a checksum!). Since the Thunderbolt port provides a way to get code running when the system boots, it is possible to modify the boot ROM code.
Update 1/27/2015: Looks like Apple is patching the Boot ROM issue that Thunderstrike exploits in Mac OS X 10.10.2 (Yosemite). When 10.10.2 is available, update ASAP!
Trammell Hudson also did quite a bit of work on Canon camera firmware which led to him releasing Magic Lantern in 2009 which adds additional functionality to Canon cameras. Certainly, he has with a bit of experience with hardware hacking. 🙂
“Magic Lantern is not a “hack”, or a modified firmware, it is an independent program that runs alongside Canon’s own software. Each time you start your camera, Magic Lantern is loaded from your memory card. Our only modification was to enable the ability to run software from the memory card.”
Trammell’s presentation is fantastic! Watch the video.
He describes Thunderstrike on his website:
Thunderstrike is the name for the Apple EFI firmware security vulnerability that allows a malicious Thunderbolt device to flash untrusted code to the boot ROM. It was presented at 31c3 and the you can read an annotated version of the presentation or watch the hour long video.
Thunderstrike is worse than BadUSB and affects Apple MacBooks (Pro/Air/Retina) with Thunderbolt ports.
Thunderstrike in its current form has been effective against every MacBook Pro/Air/Retina with Thunderbolt that I’ve tested, which is most models since 2011. The proof of concept is hardcoded for the 10,1 system, but the underlying vulnerability seems to be present and is independent of OS X version. Weaponization to attack all the different models is within the means of a dedicated attacker.
Thunderstrike Key Points:
- Exploiting a Mac with Thunderstrike requires momentary physical access to plug a specially designed dongle into the Thunderbolt port. Think “evil maid” cleaning your hotel room while you are at breakfast.
- You can have an encrypted hard drive and a boot up password as well as other best practice security methods in place. Thunderstrike bypasses all of these.
- It can infect Thunderbolt devices in order to propagate. This is one measure that could be leveraged to attack air-gapped networks.
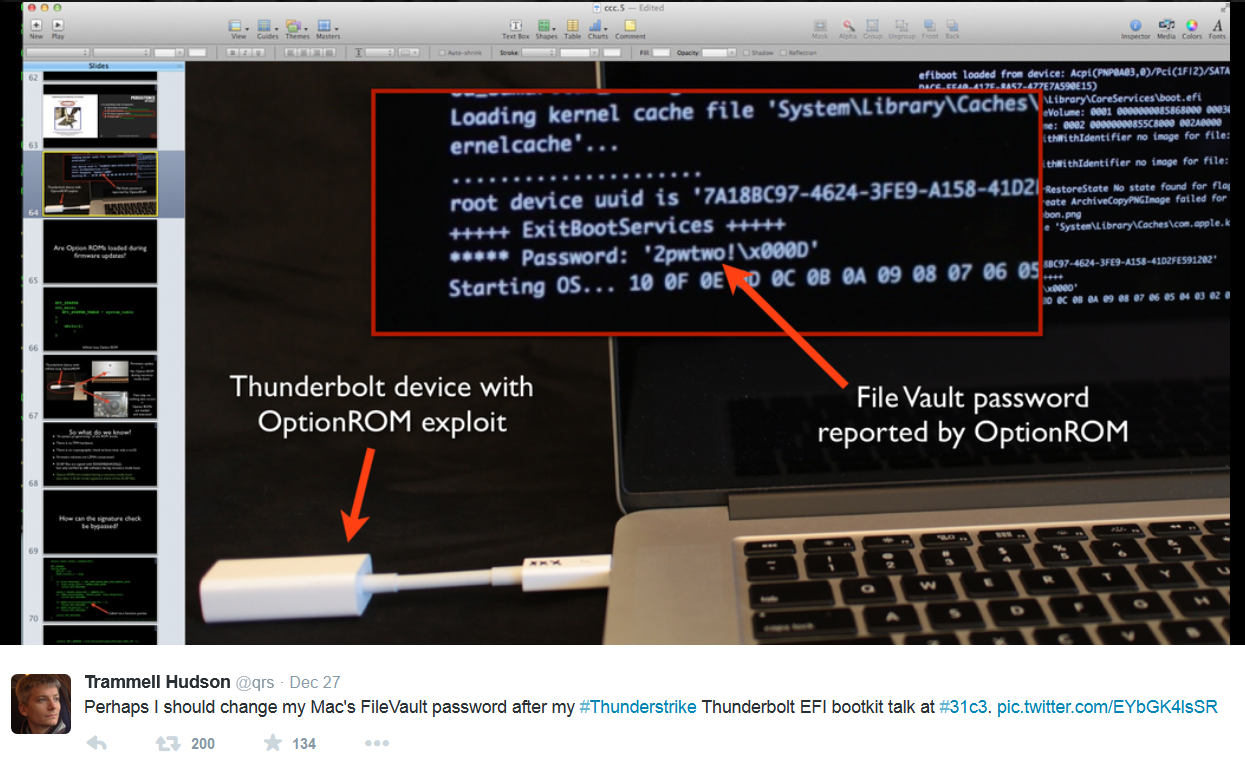
“The Thunderstrike bootkit is also in a position to be able to flash new Option ROMs into attached Thunderbolt devices with its own exploit. Like Stuxnet, this capability allows it to spread virally across air-gap security perimeters through shared peripheral devices. Since so few users need the Option ROMs, the device remains fully functional, despite carrying the malicious payload. Implementing this functionality would need a minor amount of work to weaponize and port to various devices, but an attacker of modest means could easily do so.“ - FileVault keys and passwords for encrypted boot volumes can be extracted.
- This exploit can install an undetectable and unremovable bootkit that persists through hard drive replacement and OS reinstall.
- RSA public keys are changed in the boot ROM preventing replacement by Apple’s firmware update programs. Apple software updates can’t remove it.
- Since it modifies code used to boot the system, every method used to detect it at or after boot time can be subverted.
- One installed, the Thunderstrike bootkit can not be removed by software. A hardware in-system-programming device is the only way to restore the stock firmware.
- There is no cryptographic check of the boot ROM (and no hardware TPM chip), only a software-based boot-time crc32. This does not provide security validation only verifies successful flashing of the ROM.
- This is not a DMA attack – it uses a PCIe Option ROM at boot time to launch the attack against the firmware update system.
- This is not the “Option ROM” attack, but Thunderbolt Option ROMs can help in flashing new firmware of the attacker’s choosing by circumventing flash security.
“The Option ROM attacks works like this: a Thunderbolt device that has been flashed with the exploit is plugged in and the system booted. The attacker’s code can hook any EFI or OS functions and do things like bypass firmware passwords, log keystrokes, install kernel backdoors, etc. This is the evil-maid attack described by Snare over two years ago, although this is not Thunderstrike: while an attacker can install a root kit to the drive, the Option ROM was loaded too late from the external device to be able to rewrite the ROM.” - Supply chain attack – every MacBook your company purchases could be compromised and you would never know it.
It is possible to use a Thunderbolt Option ROM to circumvent the cryptographic signature checks in Apple’s EFI firmware update routines. This allows an attacker with physical access to the machine to write untrusted code to the SPI flash ROM on the motherboard and creates a new class of firmware bootkits for the MacBook systems.
There are neither hardware nor software cryptographic checks at boot time of firmware validity, so once the malicious code has been flashed to the ROM, it controls the system from the very first instruction. It could use SMM, virtualization and other techniques to hide from attempts to detect it.
Our proof of concept bootkit also replaces Apple’s public RSA key in the ROM and prevents software attempts to replace it that are not signed by the attacker’s private key. Since the boot ROM is independent of the operating system, reinstallation of OS X will not remove it. Nor does it depend on anything stored on the disk, so replacing the harddrive has no effect. A hardware in-system-programming device is the only way to restore the stock firmware.
Additionally, other Thunderbolt devices’ Option ROMs are writable from code that runs during the early boot and the bootkit could write copies of itself to new Thunderbolt devices. The devices remain functional, which would allow a stealthy bootkit to spread across air-gap security perimeters through shared Thunderbolt devices.
While the two year old Thunderbolt Option ROM vulnerability that this attack uses can be closed with a few byte patch to the firmware, the larger issue of Apple’s EFI firmware security and secure booting without trusted hardware is more difficult to fix.
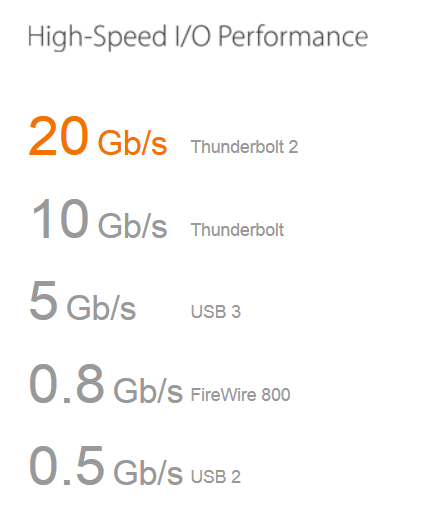
Thunderbolt (aka LightPeak) is a technology co-developed by Apple and and Intel and released in early 2011 as a next-generation I/O interface technology (kind of like USB & FireWire meets HDMI). With a single cable, one can connect a 4K HDTV, an external RAID Array, a webcam, gigabit networking, etc. With faster speeds than USB and more power on the line, it can support I/O intensive loads such as 4k graphic editing on a Thunderbolt-connected hard drive array.
From Wikipedia:
Thunderbolt combines PCI Express (PCIe) and DisplayPort (DP) into one serial signal alongside a DC connection for electric power, transmitted over one cable. Up to six peripherals may be supported by one connector through various topologies.
From Apple’s website:
So Thunderbolt is fast and can connect a myriad of demanding devices using a single interface. In order to get this performance, Thunderbolt extends the PCI Express bus and has direct memory access which could be leveraged for evil purposes. Quoting Wikipedia again:
If Thunderbolt is used to extend the PCI Express bus, which is the main expansion bus in current systems, it allows very low-level access to the system. System-bus devices usually have unlimited access to memory, and thus could be used to compromise security by performing DMA attacks.
Trammell Hudson (@qrs) presented “Thunderstrike: EFI bootkits for Apple MacBooks” at the Schedule 31. Chaos Communication Congress (31c3) on December 29th, 2014.
Thunderstrike lecture abstract:
(emphasis mine)
In this presentation we demonstrate Thunderstrike, a vulnerability that allows the installation of persistent firmware modifications into the EFI boot ROM of Apple’s popular MacBooks. The bootkit can be easily installed by an evil-maid via the externally accessible Thunderbolt ports and can survive reinstallation of OSX as well as hard drive replacements. Once installed, it can prevent software attempts to remove it and could spread virally across air-gaps by infecting additional Thunderbolt devices.
It is possible to use a Thunderbolt Option ROM to circumvent the cryptographic signature checks in Apple’s EFI firmware update routines. This allows an attacker with physical access to the machine to write untrusted code to the SPI flash ROM on the motherboard and creates a new class of firmware bootkits for the MacBook systems.
There are neither hardware nor software cryptographic checks at boot time of firmware validity, so once the malicious code has been flashed to the ROM, it controls the system from the very first instruction. It could use SMM and other techniques to hide from attempts to detect it.
Our proof of concept bootkit also replaces Apple’s public RSA key in the ROM and prevents software attempts to replace it that are not signed by the attacker’s private key. Since the boot ROM is independent of the operating system, reinstallation of OS X will not remove it. Nor does it depend on anything stored on the disk, so replacing the harddrive has no effect. A hardware in-system-programming device is the only way to restore the stock firmware.
Additionally, Thunderbolt devices’ Option ROMs are writable from code that runs during the early boot and the bootkit could write copies of itself to new Thunderbolt devices. The devices remain functional, which would allow a stealthy bootkit to spread across air-gap security perimeters through shared Thunderbolt devices.
While the two year old Option ROM vulnerability that this attack uses can be closed with a few byte patch to the firmware, the larger issue of Apple’s EFI firmware security and secure booting with no trusted hardware is more difficult to fix.
Mitigation:
While there is nothing that completely mitigates the Thunderstrike attack, the following can help:
- Disable PCIe on Thunderbolt. [Not Trivial]
- Disable Option ROMs if not required. [Difficult to Implement]
“If you don’t need Option ROMs, and I would wager that the vast majority of users do not, you can build your own ROM image with them disabled. This is a two byte patch to jump around the call to ProcessOptionRom. You had better believe that all of my machines have this modification and the firmware flashed by the Thunderstrike proof of concept also patches it. “ - Epoxy the Thunderbolt port so it can’t be used.
Apple needs to step up and address this issue with a series of updates, both in how boot checks are performed and how Option ROMs are handled. Additionally, TPM chips can be put back in the hardware and leveraged for boot ROM verification (yes, Apple used to have Trusted Boot hardware, aka TPM chips, but removed them since they weren’t used).
Some of the mitigations may not even fully mitigate security issues until Apple fixes the core issues:
“Even disabling Option ROMs alone might not be sufficient since the Thunderbolt port still is subject to active DMA attacks. The ALLOYVIPER decoy VGA adapter passes through to a real VGA adapter, but also connects to a SLOTSCREAMER PCIe card that can install backdoors into a running OSX system and likely be used to springboard a Thunderstrike style firmware update. How many of you here plugged into the projector and might have fallen into an evil-conference-organizer attack? ”
References:
- Thunderbolt [Wikipedia]
- Thunderbolt [Apple.com]
- Thunderstrike FAQ on Trammel’s site trmm.net
- Video of Trammel Hudson’s presentation at 31c3
- Overview of the Thunerstrike Presentation
- Black Hat Presentation: Hacking the Extensible Firmware Interface
- Inception DMA Hacking on live computers via FireWire, Thunderbolt, ExpressCard, PC Card and any other PCI/PCIe interfaces.

Recent Comments