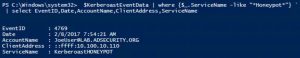
In my previous post, “Detecting Kerberoasting Activity” I explain how Kerberoasting works and describe how to detect potential Kerberoasting activity. The trick to this is understanding what activity is normal in order to filter out the noise and increase the fidelity of the alert. This post describes how to filter from millions of events to …
Tag: Detect Kerberoast Activity
Feb 05 2017
Detecting Kerberoasting Activity
Introduction Kerberoasting can be an effective method for extracting service account credentials from Active Directory as a regular user without sending any packets to the target system. This attack is effective since people tend to create poor passwords. The reason why this attack is successful is that most service account passwords are the same length …

Recent Comments