I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
May 30 2017
AD Reading: Windows Server 2016 Active Directory Features
The following are useful resources for Windows Server 2016 Active Directory Features. Windows 2016 Features What’s New in Windows 2016 Active Directory Windows Server 2016 AD Functional Level Privileged Access Management (PAM) Windows 2016 PAM Shadow Security Principals (temporary group membership) Azure AD Join Windows 2016 Azure AD Join Microsoft Hello …
May 01 2017
BSides Charm (2017) Talk Slides Posted – Detecting the Elusive: Active Directory Threat Hunting
I recently presented my talk “Detecting the Elusive: Active Directory Threat Hunting” at BSides Charm in Baltimore, MD. Slides are now posted in the Presentations section. I cover some of the information I’ve posted here before: PowerShell Security Detecting Kerberoasting: Part 1 and Part 2 On Sunday, April 30th, 2017, I spoke at BSides Charm in …
Feb 08 2017
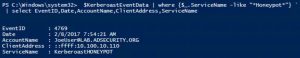
Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot
In my previous post, “Detecting Kerberoasting Activity” I explain how Kerberoasting works and describe how to detect potential Kerberoasting activity. The trick to this is understanding what activity is normal in order to filter out the noise and increase the fidelity of the alert. This post describes how to filter from millions of events to …
Feb 05 2017
Detecting Kerberoasting Activity
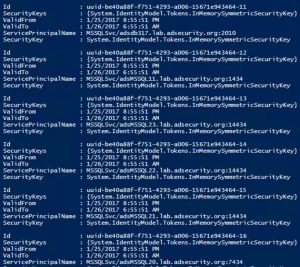
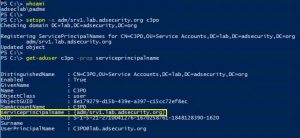
Introduction Kerberoasting can be an effective method for extracting service account credentials from Active Directory as a regular user without sending any packets to the target system. This attack is effective since people tend to create poor passwords. The reason why this attack is successful is that most service account passwords are the same length …
Nov 03 2016
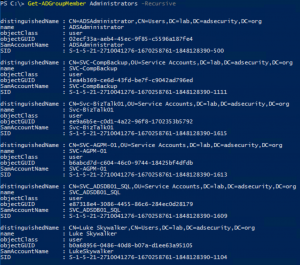
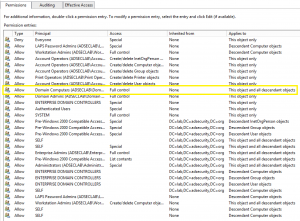
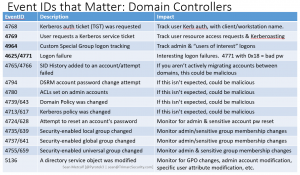
Securing Domain Controllers to Improve Active Directory Security
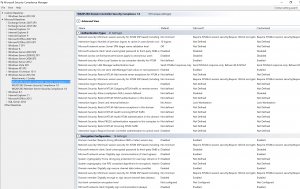
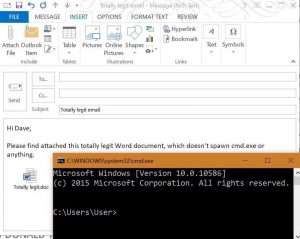
Active Directory security effectively begins with ensuring Domain Controllers (DCs) are configured securely. At BlackHat USA this past Summer, I spoke about AD for the security professional and provided tips on how to best secure Active Directory. This post focuses on Domain Controller security with some cross-over into Active Directory security. The blog is called …


Recent Comments