I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Sep 14 2025
Active Directory Security Tip #2: Active Directory User Accounts
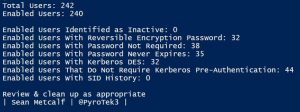
There are several different types of user accounts – at least how they are used. There are standard user accounts, service accounts, and admin accounts. There are numerous user account settings that can make them vulnerable. These configurations include: PowerShell code (using Active Directory PowerShell module):https://github.com/PyroTek3/Misc/blob/main/Get-VulnerableUserAccounts.ps1
Sep 12 2025
Active Directory Security Tip #1: Active Directory Admins
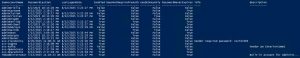
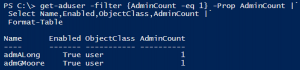
A critical part of Active Directory security is regularly reviewing your AD admins. The simplest way to do this is to recursively enumerate the membership of the domain Administrators group (that group’s members and all member group members). Check the AD Admins output for the following: PowerShell code (using Active Directory PowerShell modules):https://github.com/PyroTek3/Misc/blob/main/Get-ADAdmins.ps1
Aug 18 2025
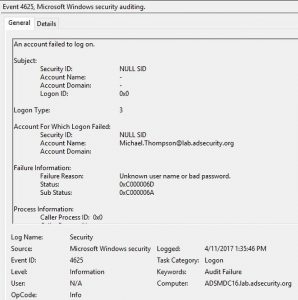
The Art of the Honeypot Account: Making the Unusual Look Normal
This article was originally posted on the Trimarc Content Hub on August 6, 2020.Updated here with authentication PowerShell code on August 18, 2025. ADSecurity.org is the new home for this article and all updates will occur here. I have had the idea for a post describing how to best create a honeypot (or honeytoken) account …
Aug 10 2025
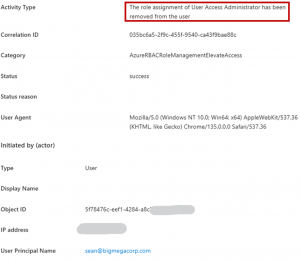
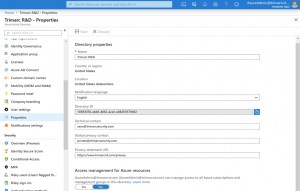
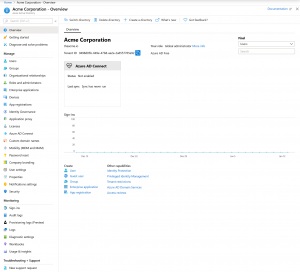
Entra & Azure Elevated Access Revisited
In early 2020, I published an article on how a Global Administrator could gain control of Azure resources, that no one would know about it, and how this access would persist even after removing them from Global Administrator. From that article: “While Azure leverages Azure Active Directory for some things, Azure AD roles don’t directly …
Dec 19 2020
Kerberos Bronze Bit Attack (CVE-2020-17049) Scenarios to Potentially Compromise Active Directory
Introduction & Attack Overview Jake Karnes (@jakekarnes42) with NetSPI published 3 articles (that’s right 3!) describing a new attack against Microsoft’s Kerberos implementation in Active Directory. He posted an Overview article, describing how the attack works, an Attack article on practical exploitation, and if you need further background on Kerberos, a Theory article. This article …
May 29 2020
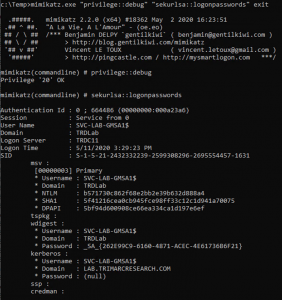
Attacking Active Directory Group Managed Service Accounts (GMSAs)
In May 2020, I presented some Active Directory security topics in a Trimarc Webcast called “Securing Active Directory: Resolving Common Issues” and included some information I put together relating to the security of AD Group Managed Service Accounts (GMSA). This post includes the expanded version of attacking and defending GMSAs I covered in the webcast.I …
Aug 07 2019
Slides Posted for Black Hat USA 2019 Talk: Attacking & Defending the Microsoft Cloud
Attacking and Defending the Microsoft Cloud (Office 365 & Azure AD) Sean Metcalf (Trimarc) & Mark Morowczynski (Principal Program Manager, Microsoft) The allure of the “Cloud” is indisputable. Organizations are moving into the cloud at a rapid pace. Even companies that have said no to the Cloud in the past have started migrating services and …


Recent Comments