This article is a cross-post from TrimarcSecurity.com
Original article: https://www.trimarcsecurity.com/single-post/2019/02/12/Mitigating-Exchange-Permission-Paths-to-Domain-Admins-in-Active-Directory
The Issue
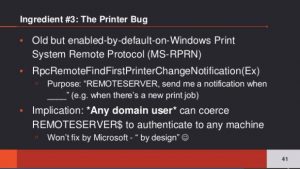
Recently a blog post was published by Dirk-jan Mollema titled “Abusing Exchange: One API call away from Domain Admin ” (https://dirkjanm.io/abusing-exchange-one-api-call-away-from-domain-admin/)which highlighted several issues with Exchange permissions and a chained attack which would likely result in a regular user with a mailbox being able to become a Domain Admin in the AD forest. Tools have been released to take advantage of this issue.
He highlights the key components of the issue in the blog post introduction:
This blog combines a few known vulnerabilities and known protocol weaknesses into a new attack. There are 3 components which are combined to escalate from any user with a mailbox to Domain Admin access:
* Exchange Servers have (too) high privileges by default
* NTLM authentication is vulnerable to relay attacks
* Exchange has a feature which makes it authenticate to an attacker with the computer account of the Exchange server
…
The main vulnerability here is that Exchange has high privileges in the Active Directory domain. The Exchange Windows Permissions group has WriteDacl access on the Domain object in Active Directory, which enables any member of this group to modify the domain privileges, among which is the privilege to perform DCSync operations. Users or computers with this privilege can perform synchronization operations that are normally used by Domain Controllers to replicate, which allows attackers to synchronize all the hashed passwords of users in the Active Directory.
Exchange Permissions in Active Directory
At the Microsoft Blue Hat in 2017, Sean Metcalf, Trimarc founder and Active Directory Subject Matter Expert (SME) highlighted issues with Exchange permissions. Some slides from this presentation are shown here as representative samples (the full presentation slide deck is in the Presentations section.





More information about this issue has been highlighted in presentations by Andy Robbins (@_wald0) and Will (@Harmj0y), including at Black Hat USA 2017.
The Bloodhound tool written by Andy Robbins, Rohan Vazarkar, and Will can identify attack paths involving Exchange permissions configured in Active Directory.
Microsoft recently published an article (https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV190007) on how to configure EWS throttling which will mitigate the issue(s) that Dirk-jan Mollema raised. The issue with this is that EWS throttling could negatively impact applications like Outlook for Mac and doesn’t resolve the escalation path with Exchange permissions configured in AD.
Trimarc has discovered Exchange having elevated permissions in AD in many customer environments while performing Active Directory Security Assessments (ADSAs).



Recent Comments