Aug 12 2018
Black Hat & DEF CON Presentation Slides Posted
I just uploaded the slides from my Black Hat & DEF CON talks from the past week in Vegas. They are a bit different with the BH talk more Blue (defensive) and the DC talk mostly Red (Offensive) in focus. Also note that the only real overlap in content is the MFA & password vault sections and those were updated in my DEF CON talk to focus on the attack aspect.
An important note: The methods I show are real and work well in many real-world customer deployments. The issues with MFA and password vaults I highlight are often deployment issues and not necessarily vendor best practices. With that noted, I have seen enterprise password vaults deployed with poor security so often that I don’t think customers are very familiar with the vendor security best practices.
Slides are in the Presentations section.
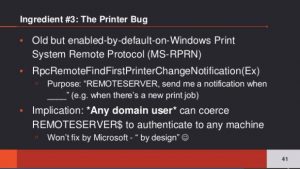
Black Hat USA 2018 Talk: “From Workstation to Domain Admin: Why Secure Administration isn’t Secure and How to Fix it”

This talk walks the audience through how AD administration has evolved over time with newer, more “secure” methods and the potential ways to exploit modern AD administration. I explore some methods to exploit current implementation weaknesses in many deployments of multi-factor authentication (MFA) and enterprise password vaults. The latter third of the talk dives into the best defenses and how to employ and deploy them appropriately.
[Slides]
Black Hat Talk Agenda:
- Current State
- Evolution of Administration
- Exploiting Typical Administration
- Common Methods of Protecting Admins (& bypassing them)
- MFA
- Enterprise Password Vaults
- Admin Forest
- Building the Best Defenses
DEF CON 26 Talk: “Exploiting Active Directory Administrator Insecurities”

This talk repeats the slide concepts from my Black Hat talk specific to exploiting current implementation weaknesses in many deployments of multi-factor authentication (MFA) and enterprise password vaults. The talk adds in some challenges in properly discovering AD admins and some additional methods of exploiting current AD environments. I also cover how in many environments it may be possible to compromise a Read-Only Domain Controller to compromise the AD forest. This talk also includes a special, new sneaky AD persistence method which only the DEF CON audience was privy to (not in the slides, at least not directly). I will post a blog article as time allows. 🙂
[Slides]
DEF CON Talk Agenda:
- Evolution of Admin Discovery
- Exploiting Typical Administration
- Multi-Factor Authentication (MFA)
- Password Vaults
- Admin Forest
- Attacking RODCs
Thank you all for your support and your kind words!
– Sean
May 20 2018
NolaCon (2018) Active Directory Security Talk Slides Posted
I recently presented my talk “Active Directory Security: The Journey” at Nolacon in New Orleans, LA.
Slides are now posted here.
On Sunday, May 19th, 2018, I spoke at NolaCon at 11am.
Here’s the talk description:
Active Directory is only the beginning.
Attackers have set their sights squarely on Active Directory when targeting a company, though this typically isn’t the primary objective. The motivation and end goals range from stealing data to impacting corporate operations. In this regard, gaining control of Active Directory is a means to an end; compromising Active Directory is an easy way to gain access to all critical corporate resources. Effectively protecting Active Directory has become critical in limiting the impact of a breach.
This talk takes the audience on a journey covering the various security milestones and challenges with Active Directory. A variety of AD security posture are highlighted along with the challenges they encounter with securing their systems. Key elements involve how enterprise “”AD aware”” applications can weaken Active Directory security and how leveraging cloud services complicate securing infrastructure. Also explored is what an attacker can do in an environment without having Domain Admin rights.
This talk covers the critical issues affecting organizations today, as well as the biggest challenges; current attack techniques; and the most effective defensive techniques to prevent and mitigate compromise (including limitations to these approaches).
For the curious, here’s an outline of the talk:
Jan 01 2018
Attacking Read-Only Domain Controllers (RODCs) to Own Active Directory
I have been fascinated with Read-Only Domain Controllers (RODCs) since RODC was released as a new DC promotion option with Windows Server 2008. Microsoft customers wanted a DC that wasn’t really a DC. – something that could be deployed in a location that’s not physically secure and still be able to authenticate users.
This post covers a few different scenarios on how to attack Read-Only Domain Controllers in order to escalate privilege. Since RODCs are typically untrusted and viewed as not having the same level of access as writable DCs, it’s possible in many environments to compromise a RODC to escalate privileges. Given certain scenarios, it’s possible to escalate from a Read-Only Domain Controller to a full writable Domain Controller. This post covers these scenarios and enables Red and Blue teams to better understand and check RODC configurations for issues.
The information in this post is not from any one customer environment I have seen, but a combination of several. I have found that many AD domains that have RODCs are configured very similarly: many more accounts, both user and computer, have passwords cached on RODCs than is necessary and the ability to manage RODCs is not limited or secured appropriately. This post shows what is possible given common real world RODC deployment configuration. As part of our Active Directory security review services, we scrutinize RODC configuration and identify potential issues with the configuration. Furthermore, we find that when RODCs are deployed in an environment, they are frequently configured with weak security settings (as noted in “RODCs in the Real World” and “Attacking RODCs” below).
The information here describes what is possible in many Active Directory environments with Read-Only Domain Controllers and doesn’t highlight a misconfiguration, but common configuration issues that could be exploited to escalate privileges in the domain since the RODC is often treated as “just another server” (or worse, as a workstation). Accounts are regularly cached on RODCs (since RODCs that don’t cache passwords aren’t very useful) and once an attacker gains access to it, these passwords are available and may include delegated Active Directory admin accounts which could be compromised.
If you want to simply know how best to “harden Read-Only Domain Controllers”, skip to the end to read the “Securing RODCs Against Attack” section.
Note that throughout this post, I use the Microsoft Active Directory PowerShell cmdlets and some of the attribute names are adjusted in the output from what they are actually named in AD.
Enter the Read-Only Domain Controller
When Microsoft released Windows Server 2008, a new type of Domain Controller was added called the “Read-Only Domain Controller”. The Read-Only Domain Controller (RODC) performs similar services as a writable Domain Controller except they are “read-only”. But what does that really mean?
Nov 24 2017
Securing Microsoft Active Directory Federation Server (ADFS)
Many organizations are moving to the cloud and this often requires some level of federation. Federation, put simply, extends authentication from one system (or organization) to another.
Gerald Steere (@Darkpawh) and I spoke about cloud security at DEF CON in July 2017.
Presentation slides and video are here: “Hacking the Cloud”
One of the key items we covered was protecting Federation Servers, specifically Microsoft Active Directory Federation Servers (ADFS).
Microsoft is currently updating guidance for securing ADFS.
This post describes key ADFS concepts and a short-list of security recommendations on how to properly protect ADFS.
Federation Overview
The federation server typically lives on the internal network with a proxy server in the DMZ. There are certificates installed on the Federation server.
ADFS uses the following certificates:
- Service communication
- Token-decrypting
- Token-signing
ADFS terminology also includes:
- Relying party trusts: cloud services and applications
- Claim rules: determine what type of access and from where access is allowed.
Key Federation Points:
- Federation: trust between organizations leveraging PKI (certificates matter)
- Cloud SSO often leverages temporary or persistent browser cookies (cookies provide access)
- Several protocols may be supported, though typically SAML. (protocols and versions matter)
- Federation server (or proxy) is on public internet via port 443 (HTTPS).
Conceptual federation authentication flow Continue reading
May 30 2017
AD Reading: Windows Server 2016 Active Directory Features
The following are useful resources for Windows Server 2016 Active Directory Features.
Windows 2016 Features
Privileged Access Management (PAM)
Azure AD Join
Microsoft Hello for Business (formerly Microsoft Passport)
May 01 2017
BSides Charm (2017) Talk Slides Posted – Detecting the Elusive: Active Directory Threat Hunting
I recently presented my talk “Detecting the Elusive: Active Directory Threat Hunting” at BSides Charm in Baltimore, MD.
Slides are now posted in the Presentations section.
I cover some of the information I’ve posted here before:
- PowerShell Security
- Detecting Kerberoasting: Part 1 and Part 2
On Sunday, April 30th, 2017, I spoke at BSides Charm in Track 2 at 2pm.
Here’s the talk description from the BSides Charm website:
Detecting the Elusive: Active Directory Threat Hunting
Attacks are rarely detected even after months of activity. What are defenders missing and how could an attack by detected?This talk covers effective methods to detect attacker activity using the features built into Windows and how to optimize a detection strategy. The primary focus is on what knobs can be turned and what buttons can be pushed to better detect attacks.
One of the latest tools in the offensive toolkit is “”Kerberoast”” which involves cracking service account passwords offline without admin rights. This attack technique is covered at length including the latest methods to extract and crack the passwords. Furthermore, this talk describes a new detection method the presenter developed.
The attacker’s playbook evolves quickly, defenders need to stay up to speed on the latest attack methods and ways to detect them. This presentation will help you better understand what events really matter and how to better leverage Windows features to track, limit, and detect attacks
This presentation covers the type of log data required to properly
For the curious, here’s an outline of the talk:

Recent Comments