IT World Canada reached out to me recently to help with an article on Active Directory attack & defense. Read the article: “IT not doing enough to secure Active Directory, says expert.” IIT World Canada also requested comments for a second story titled: “22 tips for preventing ransomware attacks“.
Tag: ActiveDirectory
Jan 05 2016
Mimikatz Update Fixes Forged Kerberos Ticket Domain Field Anomaly – Golden Ticket Invalid Domain Field Event Detection No Longer Works
In late 2014, I discovered that the domain field in many events in the Windows security event log are not properly populated when forged Kerberos tickets are used. The key indicator is that the domain field is blank or contains the FQDN instead of the short (netbios) name and depending on the tool used to …
Jan 01 2016
Attack Methods for Gaining Domain Admin Rights in Active Directory
There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Dec 31 2015
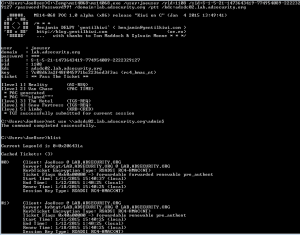
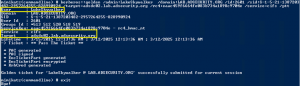
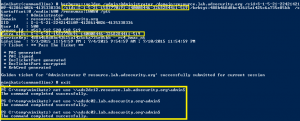
Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
Microsoft’s Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. This legacy support is enabled when using Kerberos RC4 encryption …
Nov 30 2015
Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation)
At the RSA Conference in Abu Dhabi earlier this month, Stefano Maccaglia (Incident Response Consultant with RSA) presented “Evolving Threats: dissection of a Cyber-Espionage attack.” The slides for this talk are available on the RSA Conference site (UPDATE: RSA removed the slides from their site, Presentation Slides on Yumpu). This post covers and adds some …
Nov 17 2015
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. This post continues this …
Sep 10 2015
Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Directory …
Aug 07 2015
Kerberos Golden Tickets are Now More Golden
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
May 07 2015
Windows 10 Microsoft Passport (aka Microsoft Next Generation Credential) In Detail
At the Microsoft Ignite conference this week, there are several sessions covering Windows 10 features. One of biggest changes in Windows 10 is the new credential management method and the related “Next Generation Credential”, now named Microsoft Passport. There hasn’t been much information on how the new credential system works, so I challenged myself to …

Recent Comments