Service accounts are that gray area between regular user accounts and admin accounts that are often highly privileged. They are almost always over-privileged due to documented vendor requirements or because of operational challenges (“just make it work”).
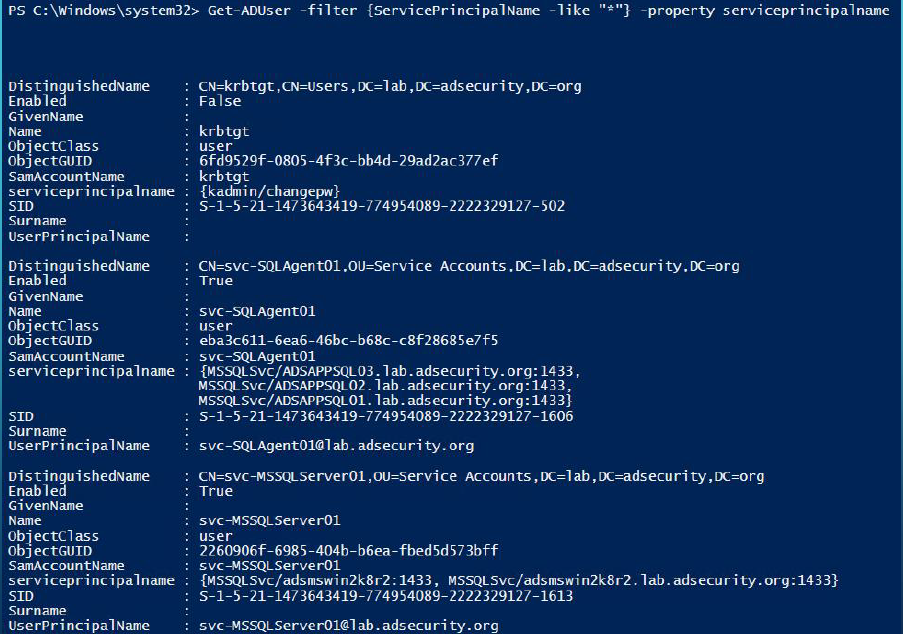
We can discover service accounts by looking for user accounts with Kerberos Service Principal Names (SPNs) which I call SPN Scanning. Service accounts without SPNs can also be discovered by querying AD accounts for ‘SVC’, or ‘Service’, or common vendor product names.
The following PowerShell commands require the Active Directory PowerShell module.
Discover service accounts (user accounts with SPNs):
get-aduser -filter {ServicePrincipalName -like “*”} -Properties PasswordLastSet,LastLogonDate,ServicePrincipalName,TrustedForDelegation,TrustedtoAuthForDelegation
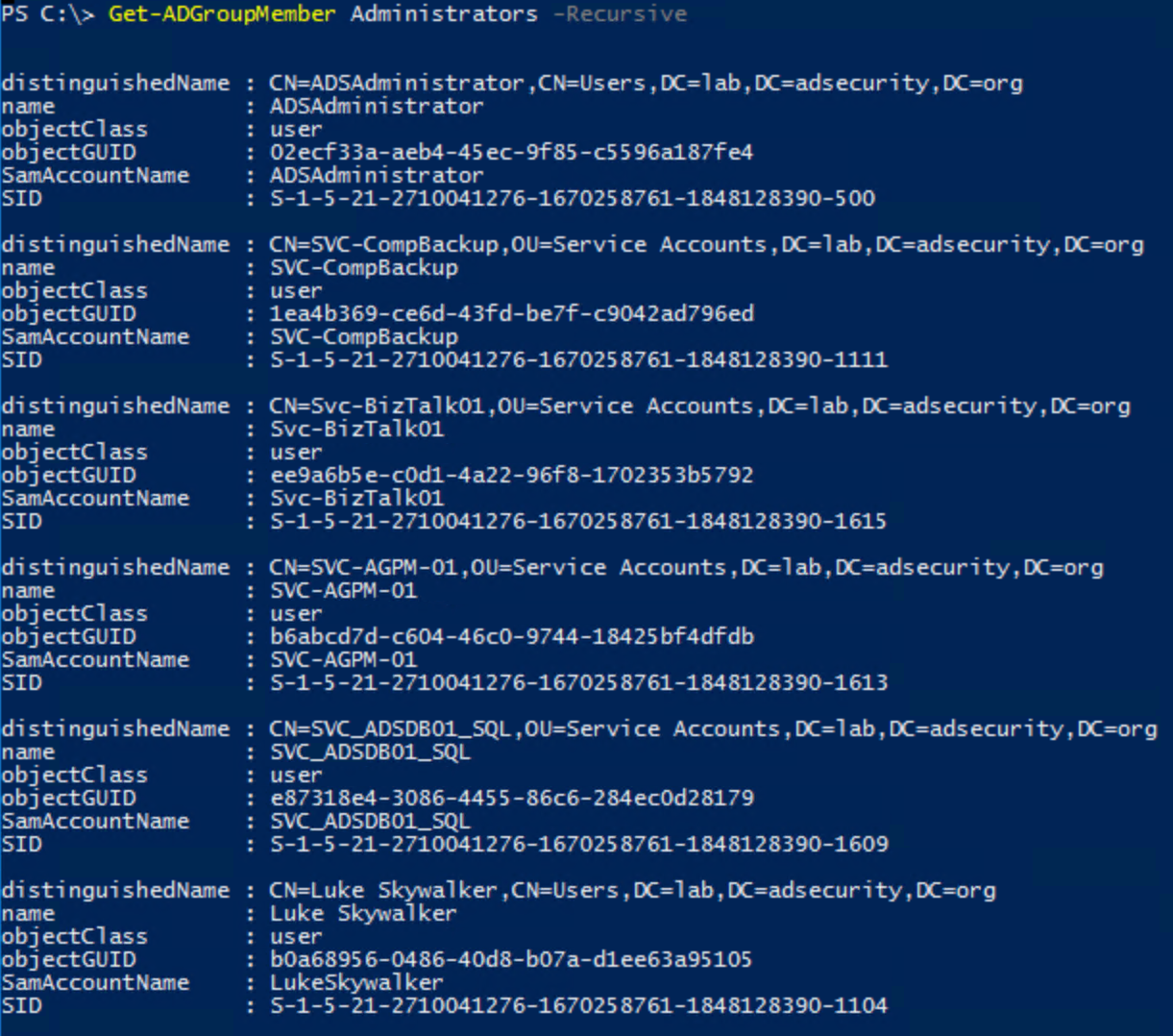
Discover probable AD Admin accounts (user accounts with AdminCount set to 1):
get-aduser -filter {AdminCount -eq 1} -Properties Name,AdminCount,ServicePrincipalName,PasswordLastSet,LastLogonDate,MemberOf

While Domain Admins is the most commonly used AD admin group, there are several others that could be used.
Common privileged AD groups that may contain Service Accounts:
- Administrators
- Full administrative rights to the AD domain and Domain Controllers.
- Domain Admins
- Full administrative rights to computers joined to the domain (default) and full administrative rights to the AD domain and DCs (through membership in the Administrators group).
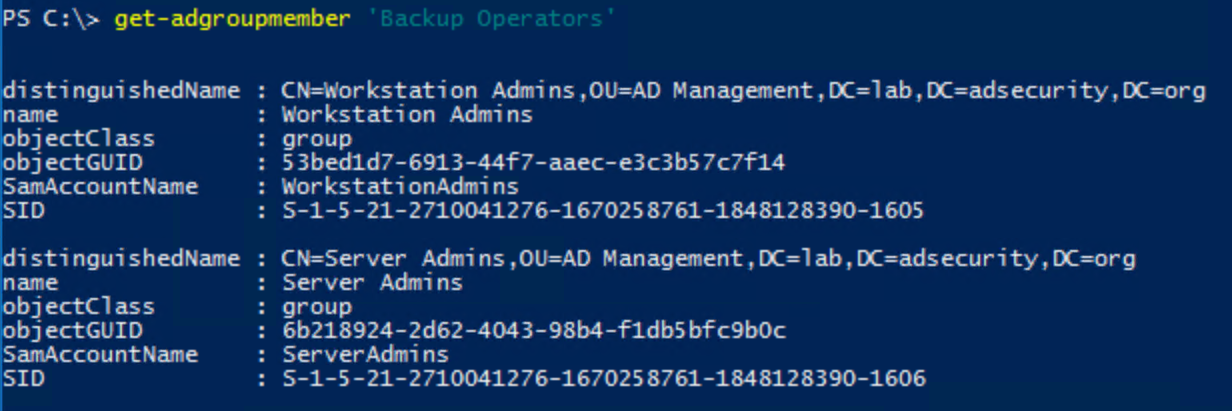
- Backup Operators
- Default rights to backup and restore Active Directory and Domain Controllers.
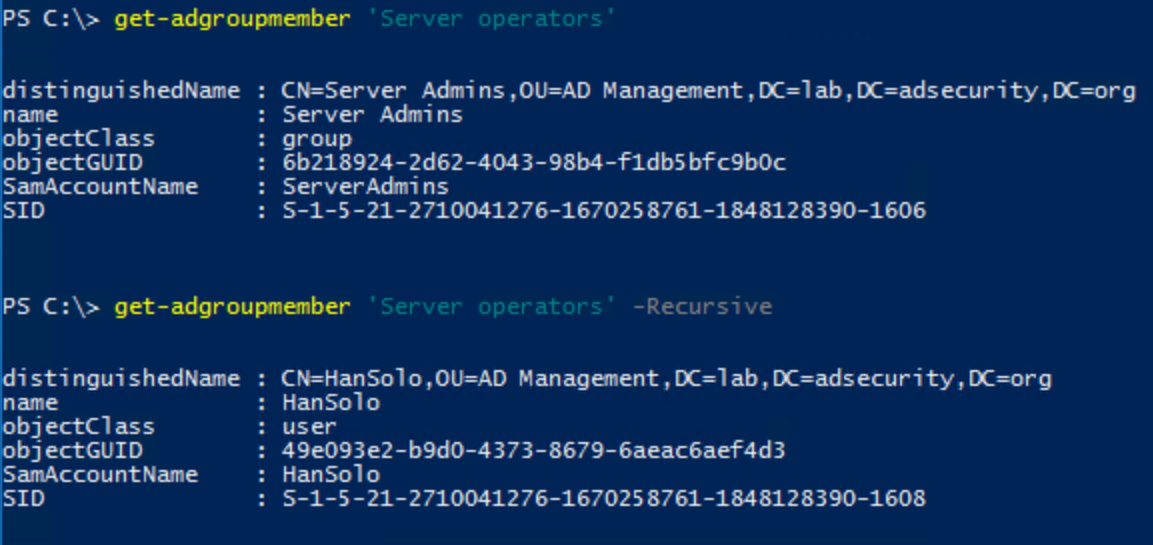
- Server Operators
- Able to logon to Domain Controllers and provides ability to perform some administrative actions on Domain Controllers.
- Enterprise Admins
- Full administrative rights to all domains and Domain Controllers in the AD forest (through membership in the Administrators group). Also has special forest admin rights such as DHCP. In a single domain forest, this group should remain empty until needed.
- Schema Admins
- Able to modify the AD schema for the forest. This group should remain empty until needed.








Recent Comments