At the RSA Conference in Abu Dhabi earlier this month, Stefano Maccaglia (Incident Response Consultant with RSA) presented “Evolving Threats: dissection of a Cyber-Espionage attack.” The slides for this talk are available on the RSA Conference site (UPDATE: RSA removed the slides from their site, Presentation Slides on Yumpu). This post covers and adds some additional detail to the attack that Stefano Maccaglia and RSA colleagues dealt with as described in this talk. I have no information about this attack other than what is covered in the slides since I wasn’t involved in the incident response. Since this RSA talk has great detail on the attack, I am taking the opportunity to point how what weaknesses the attacker exploited and how other organizations can learn from this breach. I don’t deal with attribution, so I leave it to the reader to follow the presenter’s narrative on who the attacker was.
The attack started, as many do, with a spear-phish email which was opened and code executed (in this case leveraging a Microsoft Word exploit). It is noted that the internet proxy blocked seven (7) out of nine (9) of the attacks. It only takes one success though for the attacker to gain a foothold inside the network. Note that there was a second wave which adjusted to the internet proxy configuration and was far more successful the second time around. Always expect that the attacker will quickly learn more about your environment than what you have documented.
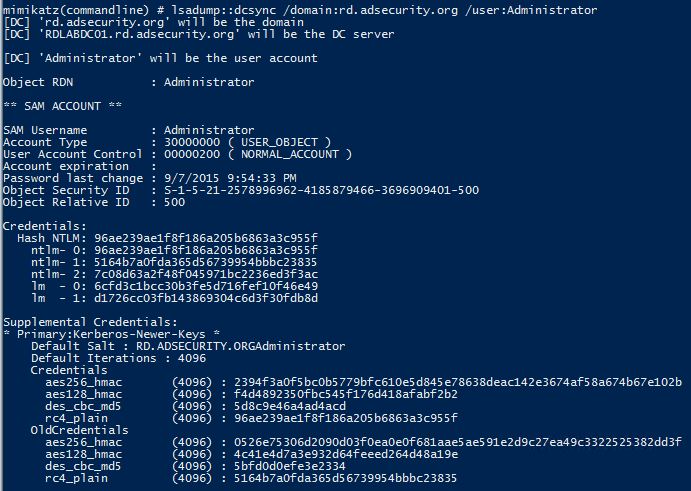
I don’t cover malware, so I won’t dig into the details of what the code did other than recon, privilege escalation, and lateral movement.
It is interesting that the attacker leveraged OWA to use stolen credentials to spread the malware using internal email addresses. The benefit to the attacker is that users often are more likely to open websites and files sent from internal email addresses.
The other interesting part is that the attacker also leveraged SharePoint to expand access by distributing the malware further. Is your organization checking for malware in SharePoint? You should.
Once the attacker has access to commonly accessed/downloaded data, any of it can be updated with malware to either expand access or persist.

Recent Comments