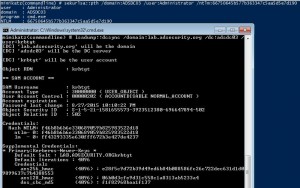
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method at DerbyCon (2015). I also presented and posted on DSRM as a persistence method previously. Complete list of Sneaky Active …
Tag: pth
Sep 06 2014
The Evolution of Protected Processes Part 1: Pass-the-Hash Mitigations in Windows 8.1
Pass-the-Hash has been around for years The post on Alex Ionescu’s blog, The Evolution of Protected Processes Part 1: Pass-the-Hash Mitigations in Windows 8.1, describes the latest mitigation techniques Microsoft is incorporating in the latest versions of Windows. He describes the importance of LSASS in his post: (emphasis/bold text is my own) The LSASS Process In …

Recent Comments