A new page on ADSecurity.org just went live which is an “unofficial” guide to Mimikatz which also contains an expansive command reference of all available Mimikatz commands. Screenshots, descriptions, and parameters are included where available and appropriate. This page includes the following topics: Mimikatz Overview Mimikatz & Credentials Available Credentials by OS PowerShell & Mimikatz …
Tag: mimikatz
Nov 30 2015
Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation)
At the RSA Conference in Abu Dhabi earlier this month, Stefano Maccaglia (Incident Response Consultant with RSA) presented “Evolving Threats: dissection of a Cyber-Espionage attack.” The slides for this talk are available on the RSA Conference site (UPDATE: RSA removed the slides from their site, Presentation Slides on Yumpu). This post covers and adds some …
Nov 22 2015
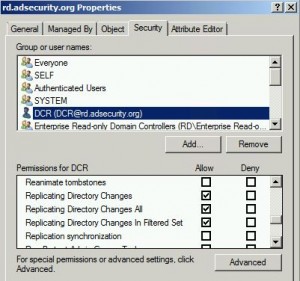
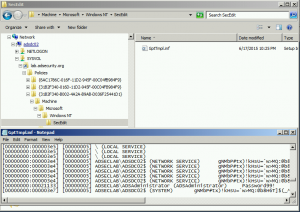
Dump Clear-Text Passwords for All Admins in the Domain Using Mimikatz DCSync
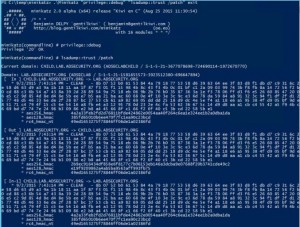
The two key goals of any attack is access and persistence. This post covers elements of each. In a post-exploitation scenario where the attacker has compromised the domain or an account with delegated rights, it’s possible to dump the clear-text passwords of admins without being a Domain Admin*. This method requires the Active Directory Domain …
Nov 17 2015
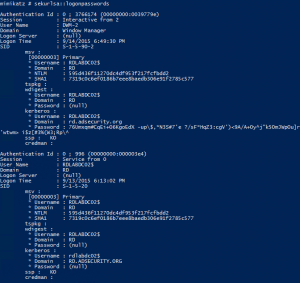
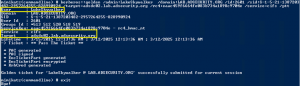
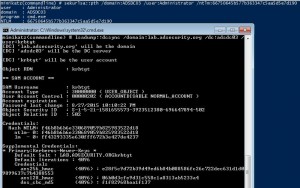
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. This post continues this …
Sep 25 2015
Sneaky Active Directory Persistence #13: DSRM Persistence v2
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method at DerbyCon (2015). I also presented and posted on DSRM as a persistence method previously. Complete list of Sneaky Active …
Sep 25 2015
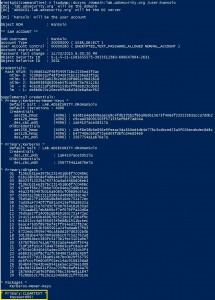
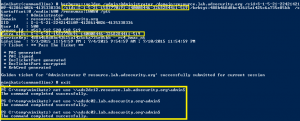
Mimikatz DCSync Usage, Exploitation, and Detection
Note: I presented on this AD persistence method at DerbyCon (2015). A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller. DCSync was written by Benjamin Delpy and Vincent Le Toux. The exploit method prior to DCSync was …
Sep 16 2015
Sneaky Active Directory Persistence #12: Malicious Security Support Provider (SSP)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Security …
Sep 10 2015
Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Directory …
Aug 07 2015
Kerberos Golden Tickets are Now More Golden
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
Jul 15 2015
It’s All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
In early 2015, I theorized that it’s possible to forge inter-realm (inter-trust) Kerberos tickets in a similar manner to how intra-domain TGTs (Golden Tickets) and TGSs (Silver Tickets) are forged. Around the same time, Benjamin Delpy updated Mimikatz to dump trust keys from a Domain Controller. Soon after, Mimikatz gained capability to forge inter-realm trust …

Recent Comments