Securing workstations against modern threats is challenging. It seems like every week there’s some new method attackers are using to compromise a system and user credentials.
Post updated on March 8th, 2018 with recommended event IDs to audit.
The best way to create a secure Windows workstation is to download the Microsoft Security Compliance Manager (currently at version 4.0) and select “Security Compliance” option under the operating system version for which you want to create the security baseline GPO. Review the options, change as needed, and export as a GPO Backup (folder). Create a new empty GPO and Import the settings from the SCM GPO backup. Then apply this newly created GPO to your workstations. This will improve your workstation security baseline if you have minimal security settings already configured, especially if you have no existing workstation GPO.
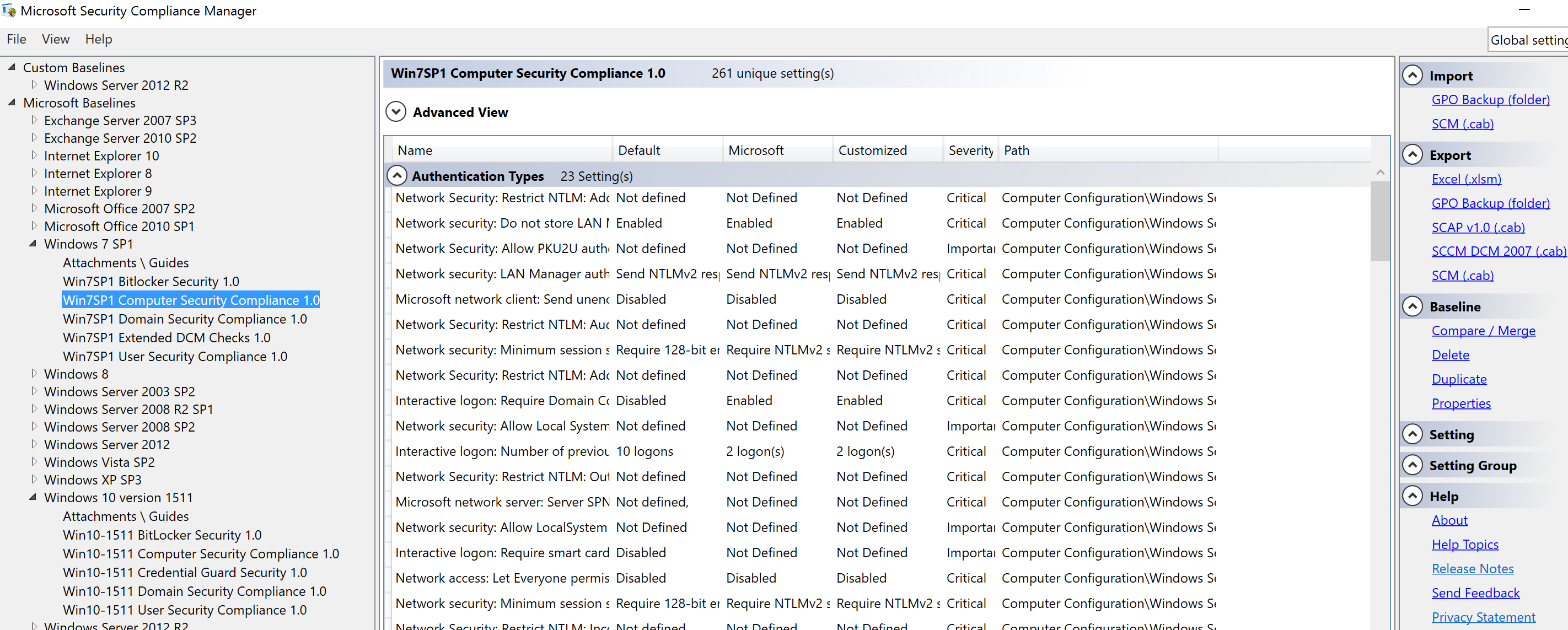
As part of developing your Windows Workstation Security Baseline GPO, there are several large organizations that have spent time and money determining what’s “secure”:
- DoD STIG: http://iase.disa.mil/stigs/os/windows
- DoD Windows 10 Secure Host Baseline files: https://github.com/iadgov/Secure-Host-Baseline
- Australian Information Security Manual: http://www.asd.gov.au/infosec/ism/index.htm
- CIS Benchmarks: https://benchmarks.cisecurity.org/downloads/browse/?category=benchmarks.os.windows
Microsoft Administrative Templates for controlling settings via Group Policy are here:
- Windows 7 & Windows Server 2008 R2: https://www.microsoft.com/en-us/download/details.aspx?id=6243
- Windows 8.1 & Windows Server 2012 R2: https://www.microsoft.com/en-us/download/details.aspx?id=43413
- Windows 10 (v1607) & Windows Server 2016: https://www.microsoft.com/en-us/download/details.aspx?id=53430
- Office 2010: https://www.microsoft.com/en-us/download/details.aspx?id=18968
- Office 2013: https://www.microsoft.com/en-us/download/details.aspx?id=35554
- Office 2016: https://www.microsoft.com/en-us/download/details.aspx?id=49030
Note that these locations are subject to change with further updates.
Group Policy Settings Reference for Windows and Windows Server
Windows 10 (v1607) & Windows Server 2016 security configuration baseline settings: https://blogs.technet.microsoft.com/secguide/2016/10/17/security-baseline-for-windows-10-v1607-anniversary-edition-and-windows-server-2016/
If you already have a GPO configuring workstation security, you can compare what you have to the SCM generated “Security Compliance” GPO using Microsoft’s Policy Analyzer.
Beyond the standard “Windows security things”, there are legacy and often unused components that linger and are carried forward from earlier Windows versions that are often no longer needed, but kept for compatibility reasons. This post covers many of these as well as other good security practices and configuration.
Obviously, you should move to the most recent version of Windows and rapidly deploy security patches when they are available.
The following items are recommended for deploying a secure Windows workstation baseline, though test first since some of these may break things.
Securing Windows Workstation:
- Deploying Free/Near-Free Microsoft Tools to Improve Windows Security
- Deploy Microsoft AppLocker to lock down what can run on the system.
-
Deploy current version of EMET with recommended software settings.
-
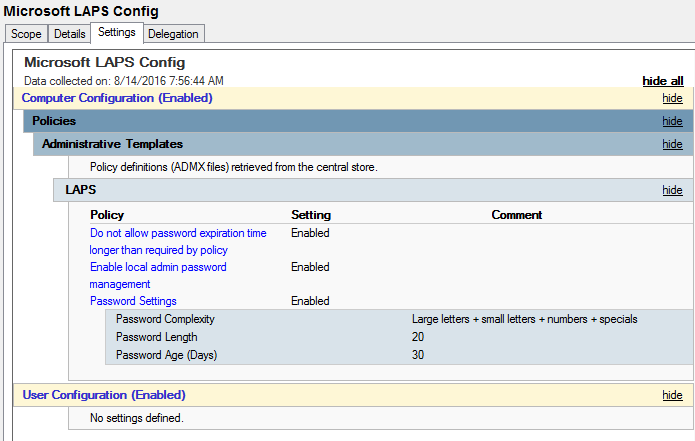
Deploy LAPS to manage the local Administrator (RID 500) password.
- Force Group Policy to reapply settings during “refresh”
- Disable Windows Legacy & Typically Unused Features
-
Disable Net Session Enumeration (NetCease)
-
Disable WPAD
- Disable LLMNR
-
Disable Windows Browser Protocol
-
Disable NetBIOS
-
Disable Windows Scripting Host (WSH) & Control Scripting File Extensions
-
Deploy security back-port patch (KB2871997).
-
Prevent local Administrator (RID 500) accounts from authenticating over the network
-
Ensure WDigest is disabled
- Remove SMB v1 support
-
-
Windows 10 & Windows 2016
-
Windows 10 & 2016 System Image Configuration
- Block Untrusted Fonts
- Enable Credential Guard
- Configure Device Guard
-
- Application Security Settings
-
Disable Microsoft Office Macros
-
Disable Microsoft Office OLE
-
- Additional Group Policy Security Settings
- Configure Lanman Authentication to a secure setting
- Configure restrictions for unauthenticated RPC clients
- Configure NTLM session security




Recent Comments