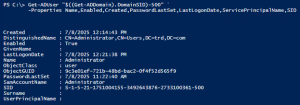
In every Active Directory domain, there’s the default domain Administrator account. Here are some key items to check: PowerShell for current domain using the AD PowerShell cmdlets:
Category: Technical Reference
Sep 16 2025
Active Directory Security Tip #4: Default/Built-In Active Directory Groups
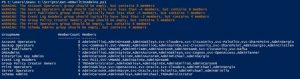
There are several default/built-in privileged groups that should be reviewed: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups PowerShell Script leveraging the Active Directory PowerShell module: https://github.com/PyroTek3/ActiveDirectory/blob/main/Get-ADBuiltInAdmins.ps1
Sep 15 2025
Active Directory Security Tip #3: Computer Accounts
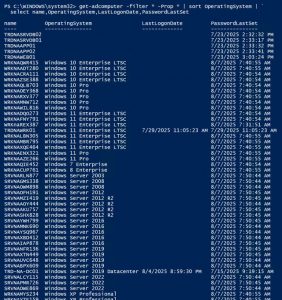
Active Directory computers should be reviewed about once a year. Old operating systems can hold back security progress like keeping SMBv1 and NTLMv1 active. Inactive computers should be discovered and disabled when no longer in use (and eventually removed). The OperatingSystem & PasswordLastSet attributes are self-explanatory, though we can use the LastLogonDate which represents the …
Sep 15 2025
Active Directory Forest & Domain Level Capabilities
An important Active Directory setting determines what security capabilities are available which relates to the level of the forest and/or domain. This post collects the relevant capabilities of Windows domain and forest functional levels.You can easily check the domain & Forest functional levels using the Active Directory PowerShell module using the cmdlets Get-ADForest & Get-ADDomain. …
Sep 14 2025
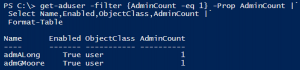
Active Directory Security Tip #2: Active Directory User Accounts
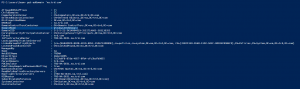
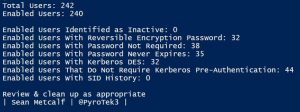
There are several different types of user accounts – at least how they are used. There are standard user accounts, service accounts, and admin accounts. There are numerous user account settings that can make them vulnerable. These configurations include: PowerShell code (using Active Directory PowerShell module):https://github.com/PyroTek3/ActiveDirectory/blob/main/Get-VulnerableUserAccounts.ps1
Aug 18 2025
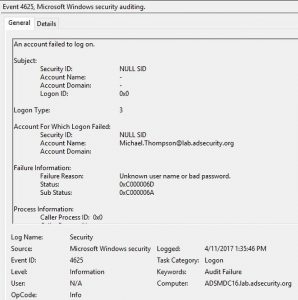
The Art of the Honeypot Account: Making the Unusual Look Normal
This article was originally posted on the Trimarc Content Hub on August 6, 2020.Updated here with authentication PowerShell code on August 18, 2025. ADSecurity.org is the new home for this article and all updates will occur here. I have had the idea for a post describing how to best create a honeypot (or honeytoken) account …
Aug 10 2025
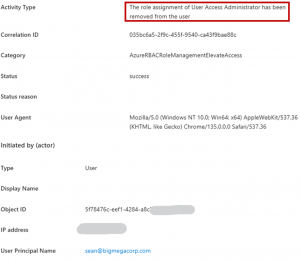
Entra & Azure Elevated Access Revisited
In early 2020, I published an article on how a Global Administrator could gain control of Azure resources, that no one would know about it, and how this access would persist even after removing them from Global Administrator. From that article: “While Azure leverages Azure Active Directory for some things, Azure AD roles don’t directly …


Recent Comments