I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Sep 16 2015
Sneaky Active Directory Persistence #12: Malicious Security Support Provider (SSP)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Security …
Sep 10 2015
DerbyCon V (2015): Red vs. Blue: Modern Active Directory Attacks & Defense Talk Detail
In a couple of weeks, I will be speaking at DerbyCon about Active Directory attack & defense in my talk Red vs. Blue: Modern Active Directory Attacks & Defense”. This is the 5th iteration of this talk and includes the latest updates to attack methods and defensive strategies. This DerbyCon version is a blend of …
Sep 10 2015
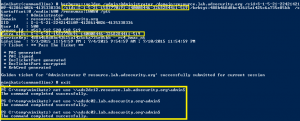
Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Directory …
Sep 02 2015
Windows Server 2016 Technical Preview 3 Download & Release Information
Looks like we are getting closer to Windows Server 2016 RTM! Microsoft released Windows Server 2016 Technical Preview 3 in late August (Download & Release Notes).
Aug 13 2015
Active Directory Security Risk #101: Kerberos Unconstrained Delegation (or How Compromise of a Single Server Can Compromise the Domain)
At Black Hat USA 2015 this summer (2015), I spoke about the danger in having Kerberos Unconstrained Delegation configured in the environment. When Active Directory was first released with Windows 2000 Server, Microsoft had to provide a simple mechanism to support scenarios where a user authenticates to a Web Server via Kerberos and needs to …
Aug 07 2015
Kerberos Golden Tickets are Now More Golden
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
Aug 02 2015
DEF CON 23 (2015) Red vs Blue: Modern Active Directory Attacks & Defense Talk Detail
This week at DEF CON 23, I will be speaking about Active Directory attack & defense in my talk “Red vs Blue: Modern Active Directory Attacks & Defense”. This is the 4th iteration of this talk and includes the latest updates to attack methods and defensive strategies.This DEF CON version has a new segment I …

Recent Comments