I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Jul 26 2015
Black Hat USA 2015 Red vs Blue Active Directory Attack & Defense Talk Detail
Next week at Black Hat USA 2015, I will be speaking about Active Directory attack & defense in my talk “Red vs Blue: Modern Active Directory Attacks Detection and Protection”. This is the 3rd iteration of this talk and includes the latest updates to attack methods and defensive strategies. I’m including lots of updates and …
Jul 15 2015
It’s All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
In early 2015, I theorized that it’s possible to forge inter-realm (inter-trust) Kerberos tickets in a similar manner to how intra-domain TGTs (Golden Tickets) and TGSs (Silver Tickets) are forged. Around the same time, Benjamin Delpy updated Mimikatz to dump trust keys from a Domain Controller. Soon after, Mimikatz gained capability to forge inter-realm trust …
Jun 24 2015
Microsoft Advanced Threat Analytics (ATA) Overview
Introduction There are several methods for identifying unusual or anomalous user activity. Traditionally these methods have required certain events be logged to the Windows event logs on workstations, servers, and Domain Controllers (DCs) and these events need to be forwarded to a central collection system. The drawback to this approach is numerous: the data logged …
May 25 2015
Summer Speaking Engagements
I am thrilled to announce I will be speaking about Active Directory security at the following security conferences: Shakacon (Waikiki Beach, HI) Black Hat USA (Las Vegas, NV) DEF CON (Las Vegas, NV) Each talk will cover current AD attack techniques and the latest defensive methods. Additionally, I will be sharing some exciting new information …
May 11 2015
Detecting Mimikatz Use
Benjamin Delpy published some YARA rules in detecting Mimikatz use in your environment. More information on Mimikatz capability is in the “Unofficial Mimikatz Guide & Command Reference” on this site. YARA is described as: YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples. With YARA …
May 08 2015
Microsoft Ignite 2015 Security Sessions
Microsoft retired several conferences this year (TechEd, MEC, MMC, etc) and merged them into a single mega-conference called Microsoft Ignite 2015. About 23,000 people (~29k including all staff and support personnel) converged on the McCormick Place Conference Center in Chicago, IL during the week of May 4th (May the Fourth be With You!). I recently …
May 07 2015
Windows 10 Microsoft Passport (aka Microsoft Next Generation Credential) In Detail
At the Microsoft Ignite conference this week, there are several sessions covering Windows 10 features. One of biggest changes in Windows 10 is the new credential management method and the related “Next Generation Credential”, now named Microsoft Passport. There hasn’t been much information on how the new credential system works, so I challenged myself to …
May 06 2015
Windows Server 2016 Technical Preview 2 Now Available for Download
Windows Server 2016 Technical Preview 2 Now Available for Download (ISO or VHD): https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview What’s new in Active Directory Domain Services (AD DS) in Windows Server Technical Preview: Privileged access management Privileged access management (PAM) helps mitigate security concerns for Active Directory environments that are caused by credential theft techniques such pass-the-hash, spear phishing, and …
May 03 2015
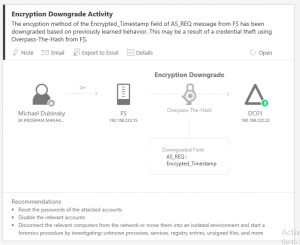
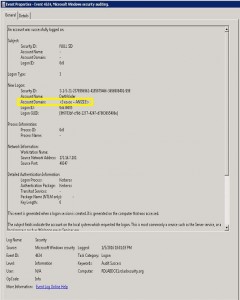
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory
Over the last 6 months, I have been researching forged Kerberos tickets, specifically Golden Tickets, Silver Tickets, and TGTs generated by MS14-068 exploit code (a type of Golden Ticket). I generated forged Kerberos tickets using Mimikatz (Mimikatz Command Reference) and MS14-068 exploits and logged the results. Over the course of several weeks, I identified anomalies …
Apr 12 2015
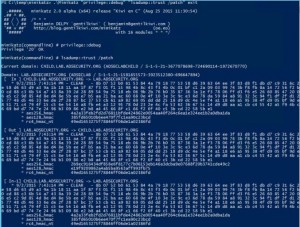
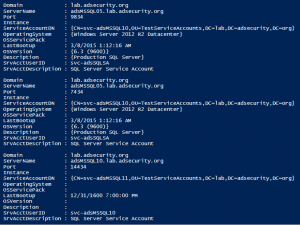
SPN Scanning – Service Discovery without Network Port Scanning
The best way to discover services in an Active Directory environment is through what I call “SPN Scanning.” The primary benefit of SPN scanning for an attacker over network port scanning is that SPN scanning doesn’t require connections to every IP on the network to check service ports. SPN scanning performs service discovery via LDAP …


Recent Comments