This August at DEF CON 24, I will be speaking about Active Directory security evaluation in my talk “Beyond the MCSE: Red Teaming Active Directory”. This talk is focused on the Red side of AD security, specifically how to best evaluate the security of AD and quickly identify potential security issues. Whether you perform “Red …
Category: Security
Apr 24 2016
BSides Charm Presentation Posted: PowerShell Security: Defending the Enterprise from the Latest Attack Platform
This was my second year speaking at BSides Charm in Baltimore. Last year I spoke about Active Directory attack & defense and it was my first time speaking at a conference. 🙂 The presentation slides for my talk “PowerShell Security: Defending the Enterprise from the Latest Attack Platform” are now on the Presentations tab here …
Apr 13 2016
What Should I Do About BadLock (CVE-2016-2118 & CVE-2016-0128/MS16-047)?
What Should I Do About BadLock (CVE-2016-2118 & CVE-2016-0128/MS16-047)? The simple answer: Patch soon. Despite the hype, which led many to assume a Remote Code Execution (RCE) was involved, this issue requires a Man-int-the-Middle (MITM) attack in order to be successful. With that noted, it is still a serious issue that requires patching. Overview Badlock …
Mar 14 2016
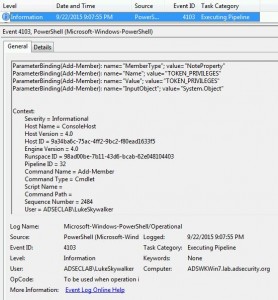
Sneaky Active Directory Persistence #17: Group Policy
The content in this post describes a method through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. Complete list of Sneaky Active Directory Persistence Tricks posts This post explores how an attacker could leverage the built-in Active Directory management capability called Group Policy …
Mar 09 2016
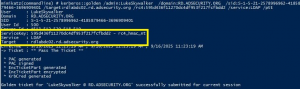
Sneaky Active Directory Persistence #16: Computer Accounts & Domain Controller Silver Tickets
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. All posts in my Sneaky Active Directory Persistence Tricks series This post explores how an attacker could leverage computer account credentials to persist in an enterprise …
Mar 02 2016
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference Updated for Mimikatz v2.1 alpha 20160229
ADSecurity.org’s Unofficial Guide to Mimikatz & Command Reference page is updated for the new modules/features in Mimikatz v2.1 alpha 20160229. According to Mimikatz author, Benjamin Delpy, the following updates are included in the most recent Mimikatz version(s): Mimikatz Release Date: 2/29/2016 2.1 alpha 20160229 (oe.eo) edition System Environment Variables & other stuff [new] System Environment …
Feb 11 2016
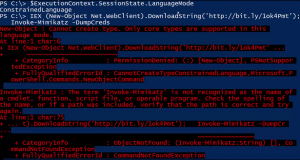
Detecting Offensive PowerShell Attack Tools
At DerbyCon V (2015), I presented on Active Directory Attack & Defense and part of this included how to detect & defend against PowerShell attacks. Update: I presented at BSides Charm (Baltimore) on PowerShell attack & defense in April 2016. More information on PowerShell Security: PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection The most …
Feb 11 2016
PowerShell Version 5 Security Enhancements
PowerShell version 5 is RTM (As of 12/18/2015). Prior to this there was a “production preview” available since August which means it was supported, but not final. With the final release of PowerShell v5 now available, I highly recommend you download PowerShell v5 and start testing to prepare for production deployment. While the PowerShell v5 …
Jan 31 2016
Microsoft EMET 5.5 Released – Benefits, New Features, Protection, Logging, & GPO Config
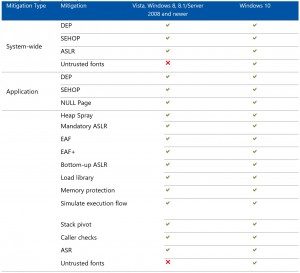
Microsoft recently released Enhanced Mitigation Experience Toolkit (EMET) version 5.5 (it jumped from 5.2 to 5.5) which includes Windows 10 compatibility and better GPO support (among others). I’ve included information from a variety of Microsoft sources in this post so that others don’t have to search for the data separately. The resources/references are listed at …
Jan 27 2016
Active Directory Recon Without Admin Rights
A fact that is often forgotten (or misunderstood), is that most objects and their attributes can be viewed (read) by authenticated users (most often, domain users). The challenge is that admins may think that since this data is most easily accessible via admin tools such as “Active Directory User and Computers” (dsa.msc) or “Active Directory …


Recent Comments