Microsoft recently released Enhanced Mitigation Experience Toolkit (EMET) version 5.5 (it jumped from 5.2 to 5.5) which includes Windows 10 compatibility and better GPO support (among others). I’ve included information from a variety of Microsoft sources in this post so that others don’t have to search for the data separately. The resources/references are listed at the bottom of this post.
Update: I have received reports of problems with IE 11 with EMET 5.5.
EMET Benefits
EMET helps prevent application vulnerabilities from being exploited (including mitigating many 0-days). It’s a free product that effectively “wraps” popular applications so when vulnerability exploitation is attempted, the attempt is stopped at the “wrapper” and doesn’t make it to the OS.
The Enhanced Mitigation Experience Toolkit (EMET) is designed to help customers with their defense in depth strategies against cyberattacks, by helping detect and block exploitation techniques that are commonly used to exploit memory corruption vulnerabilities. EMET anticipates the most common actions and techniques adversaries might use in compromising a computer, and helps protect by diverting, terminating, blocking, and invalidating those actions and techniques. EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and antimalware software.
EMET enables custom configuration of mitigations or protections on a per application basis. To facilitate broad deployment of EMET mitigations, EMET includes a few application configuration templates out of box called “protection profiles” which include settings for common Microsoft and 3rd party applications. These files are in the Deployment\Protection Profiles folder inside the EMET installation directory. The Enhanced Mitigation Experience Toolkit (EMET) 5.5 Beta User Guide provides additional detail on EMET protection profiles:
The profiles that are included with EMET are:
Recommended Software.xml: Enables mitigations for Microsoft Internet Explorer, WordPad, applications that are part of the Microsoft Office suite, Adobe Acrobat, Adobe Reader, and Oracle Java.
Popular Software.xml: Enables mitigations for other common applications.
CertTrust.xml: Enables certificate pinning rules for the login services of Microsoft Account, Microsoft Office 365, and Skype, and other popular online services such as Twitter, Facebook, and Yahoo!.
NOTE: EMET protection profiles are optimized configurations that take into consideration the known compatibility issues of some applications. The default Certificate Trust rules available with EMET are configured with specific expiration dates that will de-activate each rule before the expiration of the protected SSL certificate.
Let’s look at some rules from Popular Software.xml.
<Product Name=”Internet Explorer”>
<Version Path=”*\Internet Explorer\iexplore.exe”/>
</Product>
This rule tells EMET to protect Internet Explorer with all available memory mitigations. By default, all mitigations, with the exception of ASR and EAF+ that require specific application settings, are enabled for all applications in a protection profile. This can be changed by editing the DefaultConfig node in the profile file.
<Product Name=”Windows Media player”>
<Version Path=”*\Windows Media Player\wmplayer.exe”>
<Mitigation Enabled=”false” Name=”MandatoryASLR”/>
<Mitigation Enabled=”false” Name=”EAF”/>
<Mitigation Enabled=”false” Name=”SEHOP”/>
</Version>
</Product>
This rule enables all mitigations for Windows Media Player, except Mandatory ASLR, EAF, and SEHOP. Another important information is the Path. We have “*\Windows Media Player\wmplayer.exe”. The path is what EMET uses to register its mitigations for an application. It has to match the target application’s path for the mitigations to be effective.
The full path name to the application must be specified. Wildcards can also be used, such as * or ?. Another option is to just use the executable name without the path, such as wmplayer.exe.
Please note that wildcards are only accepted in the path portion, and not in the executable name itself. For instance “wmplayer.exe” or “*\wmplayer.exe” are valid paths, while “*player.exe” or “*wmplayer.exe” are not. This is due to a limitation of the Application Compatibility Framework in Windows that EMET relies on.
The protection files are well commented themselves. Reading them is a great way to learn more about this feature. Protection Profiles can be enabled via the EMET Graphical User Interface, the EMET Command Line Tool or via Group Policy.
EMET greatly improves the security posture of the Windows OS and even with a default EMET install with no further configurations there are some benefits.
However, do not deploy EMET without testing first.
Also, there are bypasses for EMET protection. That’s ok. Every additional defensive layer deployed makes it more challenging for successful system exploitation – it increases attacker cost and improves detection opportunity.
New Features in Microsoft EMET 5.5:
Windows 10 compatibility
Untrusted font mitigation (Windows 10)
Windows 10 added a Blocking Untrusted Fonts feature to protect users from attacks originating from untrusted or attacker-controlled font files (You can learn more about the feature by reading the “Block untrusted fonts in an enterprise” MSDN article. The corresponding EMET mitigation setting can be used to tell the system how to take advantage of this new feature, both system wide or on a per-application basis, similar to how other system-wide mitigations like DEP are configured. Untrusted fonts are any font installed outside of the %windir%/Fonts directory. Blocking untrusted fonts helps prevent both remote (web-based or email-based) and local EOP attacks that can happen during the font file-parsing process.
- Sending a print job to a remote printer server that uses this feature and where the spooler process hasn’t been specifically excluded. In this situation, any fonts that aren’t already available in the server’s %windir%/Fonts folder won’t be used.
- Printing using fonts provided by the installed printer’s graphics .dll file, outside of the %windir%/Fonts folder. For more information, see Introduction to Printer Graphics DLLs.
- Using first or third-party apps that use memory-based fonts.
- Using Internet Explorer to look at websites that use embedded fonts. In this situation, the feature blocks the embedded font, causing the website to use a default font. However, not all fonts have all of the characters, so the website might render differently.
- Using desktop Office to look at documents with embedded fonts. In this situation, content shows up using a default font picked by Office.
There are three sets of policies that EMET exposes. Below is a description of each. More information can be found at the policy editor for each policy.
System Mitigations: Named System ASLR, System DEP and System SEHOP, these policies are used to configure system mitigations. Please note that modifying system mitigation settings may require a reboot to be effective.
Default Protections: These are default protection settings for groups of applications. The three profiles do not include each other, therefore to enable the most comprehensive list of applications to protect you need to enable all of these. Enabling Internet Explorer and Recommended Software corresponds to the configuration that the Configuration Wizard applies when EMET is installed.
- … for Internet Explorer: Enables default protections for Internet Explorer.
- … for Recommended Software: Enables default protections for WordPad, applications that are part of the Microsoft Office suite, Adobe Acrobat, Adobe Reader, and Oracle Java.
- … for Popular Software: Enables default protections for other popular software.
Application Configuration: This leads to a freeform editor where additional applications not part of the default protection profiles can be configured. The syntax is application executable name followed by an optional list of mitigations that does not need to be enabled. If no mitigation is specified, all EMET application mitigations will be enabled.
Default Action and Mitigation Settings: These settings are related to the advanced settings for the ROP mitigations, described in the paragraph Advanced Mitigations for ROP, and for the default action when an exploit is detected (Audit only or Stop).
EMET Agent Visibility: This setting allows to automatically hide the EMET Agent icon in the tray area of the taskbar.
EMET Agent Custom Message: This entry allows to define a customized message that will be displayed in the alert that is shown when EMET detects an attack. The Tray Icon reporting setting must be turned on to display this message.
Reporting: This entry allows to toggle the reporting configuration for the Windows Event Log, the Tray Icon, and the Early Warning Program.
…To view the Group Policy controlled EMET settings, run the following command using the EMET Command Line Tool.
EMET_Conf –list
It is important to note that the settings configured via Group Policy take precedence over the settings configured locally using the EMET GUI or the EMET Command Line Tool. Also, Group Policy controlled settings can only be modified or deleted via Group Policy.
For example, running EMET_Conf –delete_all will only clear the mitigations and SSL certificate pinning rules that have been defined through the EMET GUI or EMET_Conf. The mitigation settings and SSL certificate pinning rules defined via GPO will be intact.
Once EMET Group Policies are enabled, they will be written out to the registry at HKLM
\SOFTWARE\Policies\Microsoft\EMET. This registry key is monitored by the EMET Service, which will automatically apply the configuration locally.
Export Address Table Access Filtering (EAF)
In order to do something “useful”, shellcode generally needs to call Windows APIs. However, in order to call an API, shellcode must first find the address where that API has been loaded. To do this the vast majority of shellcode iterates through the export address table of all loaded modules, looking for modules that contain useful APIs. Typically this involves kernel32.dll, ntdll.dll or kernelbase.dll. Once an interesting module has been found, the shellcode can then figure out the address where an API in that module resides. This mitigation filters read accesses to the Export Address Table (EAT), allowing or disallowing a read/write access based on whether the calling code originated from a shellcode. With EMET in place, most of today’s shellcode will be blocked when it tries to look up the APIs needed for its payload.
This mitigation may have compatibility issues with software such as debuggers, software behaving like debuggers, or that use anti-debugging techniques. Examples include protection mechanisms for videogames, sandboxing solutions, DRM, debugging/tracing tools, and unpackers.
Please note this is a pseudo mitigation designed to break current exploit techniques. It is not designed to break future exploits. As exploit techniques continue to evolve, so does EMET.
Export Address Table Access Filtering Plus (EAF+)
The EAF+ mitigation is an extension of EAF that can be used independently or in combination with EAF itself. Following is the list of actions that this mitigation performs:
- Detects if the stack register is out of the allowed boundaries
- Detects mismatch of stack and frame pointer registers;
- Detects memory read access to export table pointers of KERNEL32, NTDLL and KERNELBASE originated from specific modules (typically used during the exploitation of memory corruption vulnerabilities);
- Detects memory read accesses to the MZ/PE header of specific modules (typically used during the exploitation of memory corruption vulnerabilities).
The actions described in the last two bullet points require users to specify a set of modules that will be used for validation; if no modules are specified, these two actions will be ignored.
EMET 5.5 Supported Operating System:
Windows 10 , Windows 7, Windows 8, Windows 8.1, Windows Server 2008, Windows Server 2012, Windows Server 2012 R2, Windows Vista
EMET Event Logging
EMET logs events to the “EMET” event log and these events can be forwarded to a central event server via Windows Event Forwarding.
Reporting
EMET has reporting capability provided through a Windows Service called “Microsoft EMET Service”. Once EMET is installed, the service is set to automatically start with Windows. The EMET Service is responsible to dispatch the EMET Agent, which will show up in the system tray area of the taskbar with an EMET icon.
The visibility of the EMET Agent icon in tray area can be configured via Group Policy or via the command line tool).
The EMET Service performs the following tasks:
Write events in the Windows Event Log: EMET events are logged via the event source called EMET.
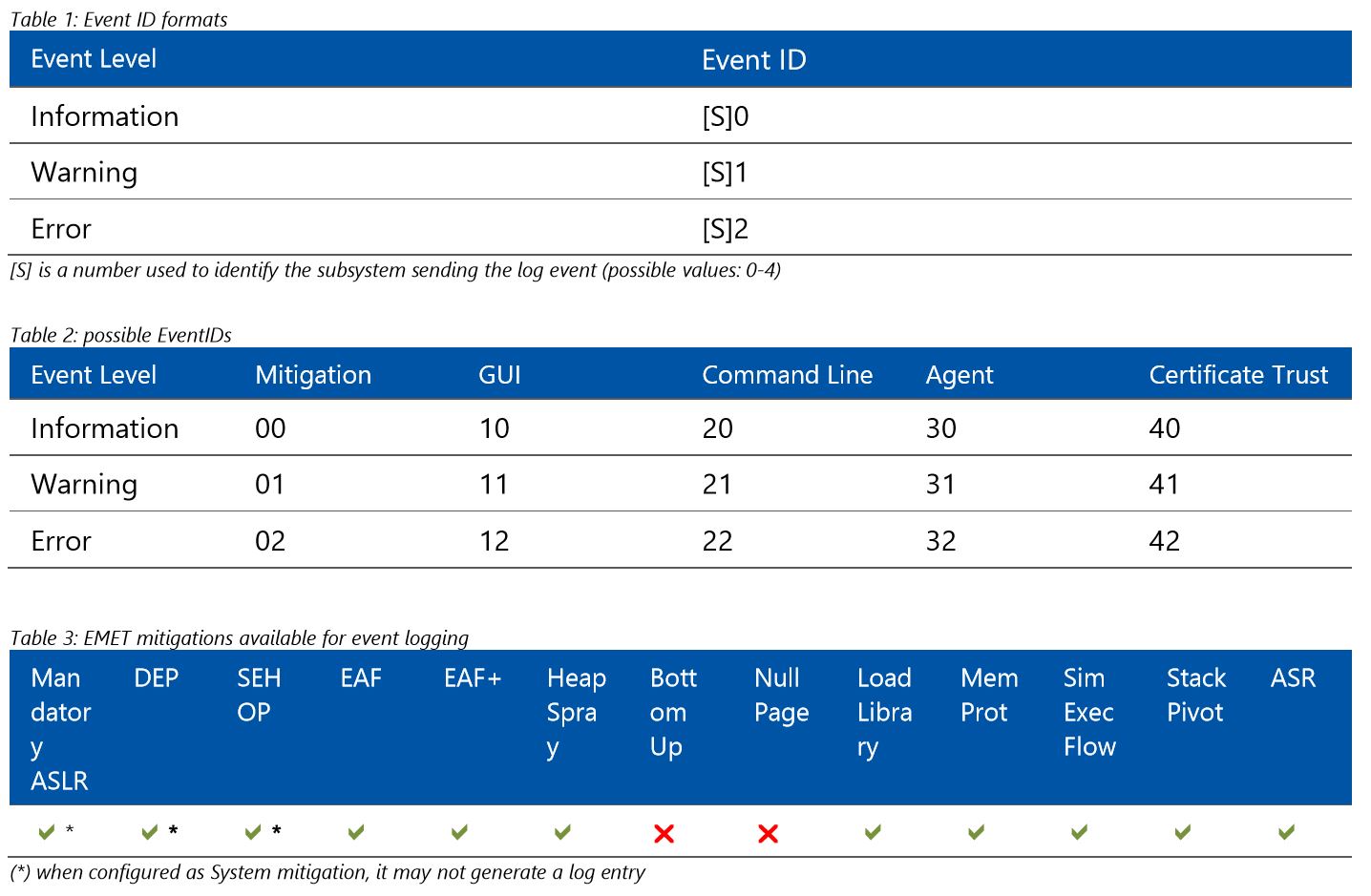
These logs can be found in the Application Log. There are 3 different levels of logging: Information, Warning and Error. Information messages are used for logging usual operation such as the EMET Agent starting. Warning messages are used when EMET settings change or to report Certificate Trust detections of SSL certificates validated by an exception rule. Error messages are used for logging cases where an untrusted SSL certificate is detected or where EMET stopped an exploit with one of its mitigations and this means a possible active attack was prevented. The list of possible EventIDs associated with EMET reporting is presented below; users should be also aware that some mitigations may not be fully logged by EMET when they are configured as System mitigations and are natively provided by the operating system.
The text above & the following graphics from the Enhanced Mitigation Experience Toolkit (EMET) 5.5 Beta User Guide shows what is logged.
EMET Mitigation Caveats
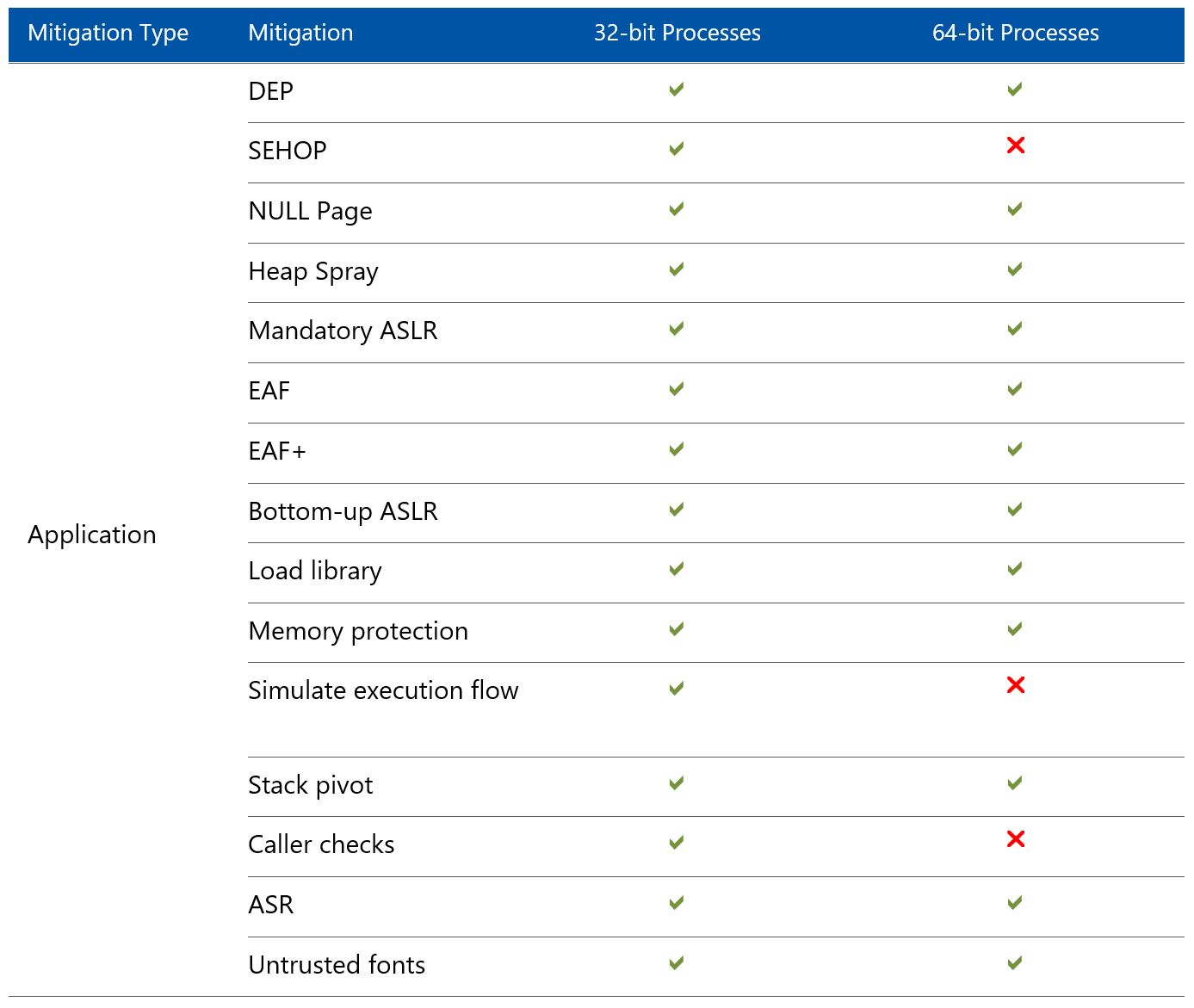
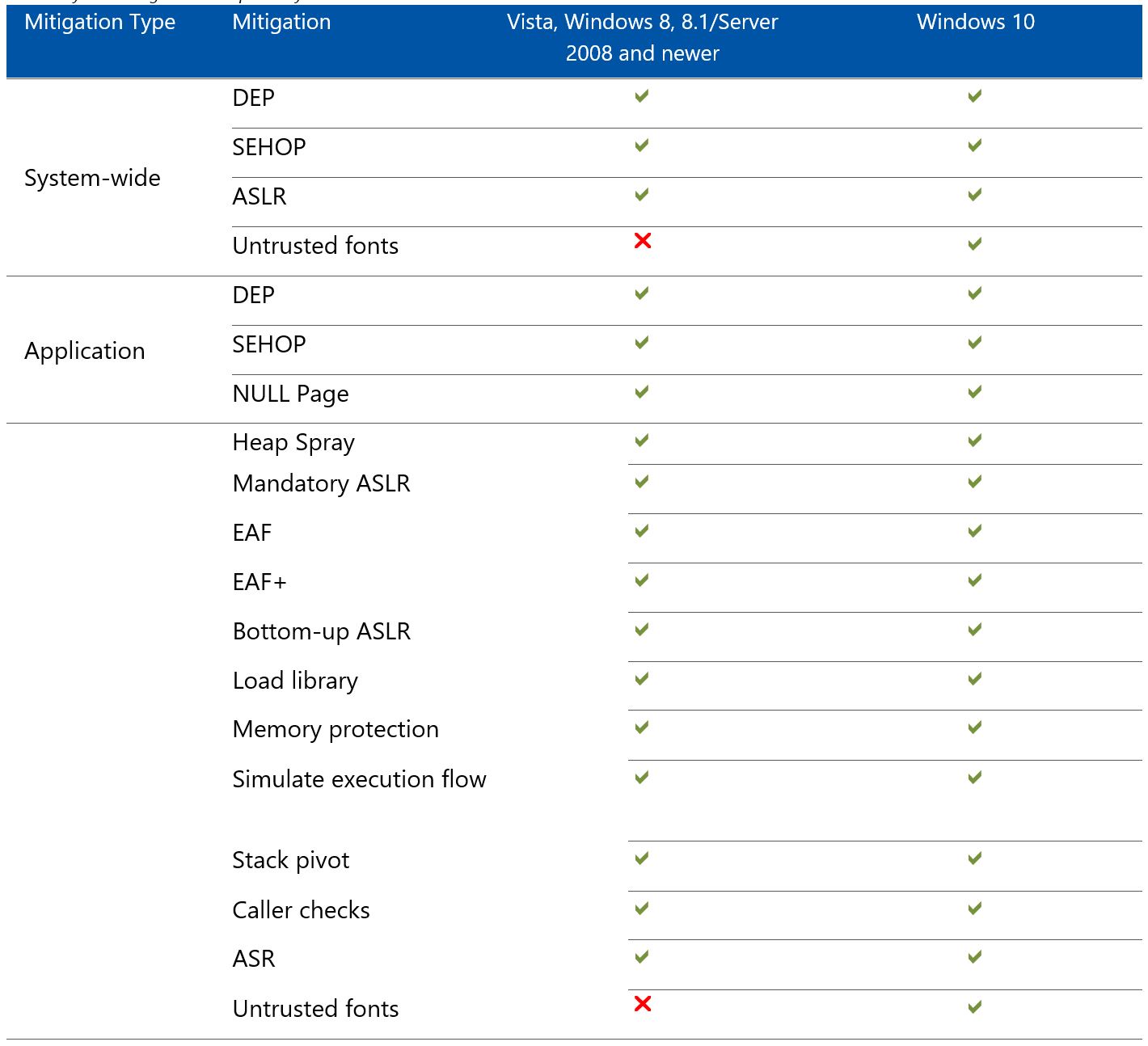
There are some protections that are not available depending on the OS version and whether the process is 32-bit or 64-bit.
The following graphics from the Enhanced Mitigation Experience Toolkit (EMET) 5.5 Beta User Guide shows mitigation support.
Hiding the EMET Icon
The EMET icon that appears in the tray area can be hidden by setting the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET\AgentStartHidden = 1
Setting it to 0 will show the EMET icon again.
References:
- Download Microsoft EMET 5.5
- Microsoft’s EMET page
- EMET 5 Presentation (Slides)
- Untrusted font mitigation (Windows 10)
- Enhanced Mitigation Experience Toolkit (EMET) 5.5 Beta User Guide
- EMET – The Ultimate Installation and Deployment Guide

Recent Comments