Slides from both of my talks this week in Vegas are now posted. There are some differences between the talks, though the primary content is similar/same. DEF CON 23 (2015) Talk Detail Black Hat USA 2015 Talk Detail Note that while some of the content is the same (mainly Blue Team information), I describe exploiting …
Category: Technical Reference
Aug 07 2015
Kerberos Golden Tickets are Now More Golden
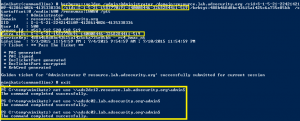
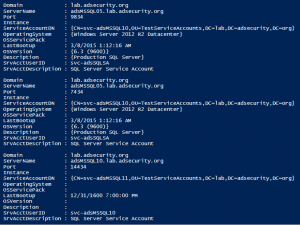
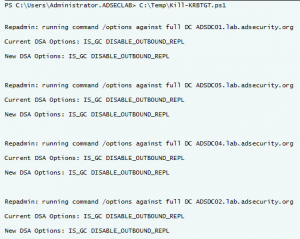
At my talk at Black Hat USA 2015, I highlighted new Golden Ticket capability in Mimikatz (“Enhanced Golden Tickets”). This post provides additional detailed on “enhanced” Golden Tickets. Over the past few months, I researched how SID History can be abused in modern enterprises. As part of this research, I reached out to Benjamin Delpy, …
May 11 2015
Detecting Mimikatz Use
Benjamin Delpy published some YARA rules in detecting Mimikatz use in your environment. More information on Mimikatz capability is in the “Unofficial Mimikatz Guide & Command Reference” on this site. YARA is described as: YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples. With YARA …
May 07 2015
Windows 10 Microsoft Passport (aka Microsoft Next Generation Credential) In Detail
At the Microsoft Ignite conference this week, there are several sessions covering Windows 10 features. One of biggest changes in Windows 10 is the new credential management method and the related “Next Generation Credential”, now named Microsoft Passport. There hasn’t been much information on how the new credential system works, so I challenged myself to …
May 06 2015
Windows Server 2016 Technical Preview 2 Now Available for Download
Windows Server 2016 Technical Preview 2 Now Available for Download (ISO or VHD): https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview What’s new in Active Directory Domain Services (AD DS) in Windows Server Technical Preview: Privileged access management Privileged access management (PAM) helps mitigate security concerns for Active Directory environments that are caused by credential theft techniques such pass-the-hash, spear phishing, and …
Apr 12 2015
SPN Scanning – Service Discovery without Network Port Scanning
The best way to discover services in an Active Directory environment is through what I call “SPN Scanning.” The primary benefit of SPN scanning for an attacker over network port scanning is that SPN scanning doesn’t require connections to every IP on the network to check service ports. SPN scanning performs service discovery via LDAP …
Feb 18 2015
Interesting KRBTGT Password Reset Behavior
Following up on Twitter conversations (@passingthehash, @scriptjunkie1, gentilkiwi, etc) on the new KRBTGT Password Reset Script and Skip Duckwall’s (@passingthehash) blog post on how KRBTGT password changes work. Microsoft KB2549833 states that the KRBTGT password is set automatically to a random string when a new password is entered. This occurs because there is special logic …
Feb 11 2015
MS15-011 & MS15-014: Microsoft Active Directory Group Policy (GPO) Vulnerabilities Patched
On February’s Patch Tuesday (2/11/2015), Microsoft released two patches that fix issues with the way Group Policy is processed by the client. Interestingly enough, one of these vulnerabilities (MS15-014) makes the other one (MS15-011) not only feasible, but quite capable. The Attack Scenario: An attacker leverages the vulnerability described in MS15-014 to prevent/stop Group Policy …
Feb 03 2015
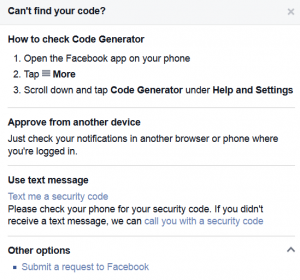
Configuring Two-Factor Authentication for Web (Cloud) Services
Don’t want your web (cloud) account password to get hacked? Enable Two-Factor Authentication (aka two-step verification)! Google Account: Visit this site and follow the instructions to configure your cell phone as a second factor Step 1: You’ll enter your password Whenever you sign in to Google, you’ll enter your password as usual. Step 2: You’ll …
Jan 27 2015
Enabling Windows 8 Hyper-V for a Portable Lab
Installing Hyper-V: Requirement: Windows 8 Pro or Windows 8 Enterprise which include Client Hyper-V. Requirement: Your computer processor must support virtualization technology (VT), though most processors in the past 5 years support VT (pretty much all Intel i-series processors, i3, i5, i7). Enable virtualization technology (VT) on your computer’s processor by editing the BIOS settings …

Recent Comments