I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Dec 05 2014
Windows Computer Primary Group IDs
Primary Group IDs are the RIDs for the Domain groups. The full list is here: Interesting Windows Computer & Active Directory Well-Known Security Identifiers (SIDs). 515 – Domain Computers 516 – Domain Controllers (writable) 521 – Domain Controllers (Read-Only) This information helps filter computer objects to return only the desired computer type. Domain Computers (Workstation …
Nov 25 2014
BlueHat Security Briefings: Fall 2014 Sesions
Microsoft has posted videos and slides from the Microsoft internal “BlueHat” security conference from October 2014. BlueHat Security Briefings educate Microsoft engineers and executives on current and emerging security threats as part of continuing efforts to help protect our customers and secure our products, devices, and services. BlueHat serves as a great opportunity for invited …
Nov 24 2014
Microsoft Consolidated Technology Conference: Microsoft Ignite
Microsoft announced over the Summer they are merging the individual technology conferences such as the SharePoint Conference, Exchange Conference, and TechEd into a single unified technology conference. Details are finally available for the Microsoft Ignite Conference which promises to be the conference to attend if you are interested in Microsoft technology solutions. Who is Ignite …
Nov 22 2014
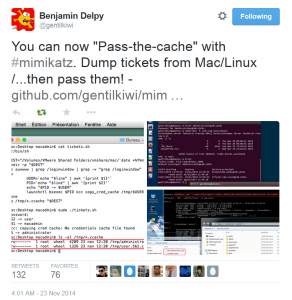
Mimikatz and Active Directory Kerberos Attacks
NOTE: While this page will remain, the majority of the Mimikatz information in this page is now in the “Unofficial Mimikatz Guide & Command Reference” which will be updated on a regular basis. Mimikatz is the latest, and one of the best, tool to gather credential data from Windows systems. In fact I consider Mimikatz …
Nov 21 2014
MS14-068: Active Directory Kerberos Vulnerability Patch for Invalid Checksum
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works The folks at BeyondTrust have …
Nov 21 2014
Microsoft KB2871997: Back-Porting Windows 8.1/Win2012R2 Enhanced Security & Pass The Hash Mitigation to Windows 7, Windows 8, & Windows 2008R2
In June 2014, Microsoft released KB2871997 which takes many of the enhanced security protection mechanisms built into Windows 8.1 & Windows Server 2012 R2 and “back-ports” them to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012. The enhanced security features reduce the credential data stored in memory and supports modern authentication (Kerberos …
Nov 19 2014
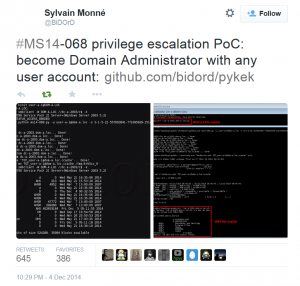
Kerberos Vulnerability in MS14-068 (KB3011780) Explained
Thanks to Gavin Millard (@gmillard on Twitter), we have a graphic that covers the issue quite nicely (wish I had of thought of it!) Exploit Code is now on the net! As of December 4th, 2014, there is Proof of Concept (POC) code posted that exploits MS14-068 by Sylvain Monné by using Python to interact with …
Nov 18 2014
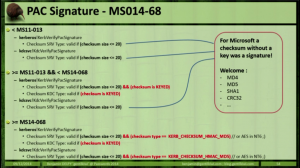
MS14-068: Vulnerability in (Active Directory) Kerberos Could Allow Elevation of Privilege
Active Directory leverages the Kerberos protocol for authentication. The vulnerability patches an issue with how the Domain Controller validates group membership in Kerberos tickets (hint: the ticket is always validated by the DC if the checksum is set to certain values). Microsoft KB3011780 patches this issue. According to Microsoft: “When this security bulletin was issued, …
Nov 17 2014
PowerShell: Discover Active Directory Forest Domain Controllers
Recently I needed to find all Domain Controllers in a large Active Directory forest (and see the AD Domain Functional Level for each domain). Here’s the PowerShell code which leverages the Active Directory PowerShell module cmdlets. import-module ActiveDirectory $ADForestInfo = Get-ADForest $ADForestInfoName = $ADForestInfo.Name $ADForestInfoDomains = $ADForestInfo.Domains $ADForestInfoForestMode = $ADForestInfo.ForestMode $AllDCs = $Null ForEach …


Recent Comments