I improve security for enterprises around the world working for TrustedSec & I am @PyroTek3 on Twitter. Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
Jan 16 2015
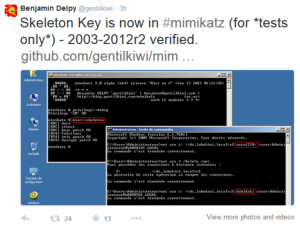
Active Directory Domain Controller Skeleton Key Malware & Mimikatz
Dell SecureWorks posted about the Skeleton Key malware discovered at a customer site. The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS. The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins. This enables the attacker to …
Jan 14 2015
Windows Server 2012 & Windows Server 2012 R2 Complete Documentation
Microsoft took all the Windows Server 2012 (& 2012 R2) documentation and posted it as a single PDF! Version: 1.0 File Name: WS12_R2_and_WS12_TechNet.pdf Date Published: 2/18/2014 File Size: 125.9 MB This download is an Adobe® PDF of the entire contents of the Windows Server 2012 R2 and Windows Server 2012 section of the Microsoft TechNet …
Jan 13 2015
“Hacker” Movies to Watch before the Blackhat Movie
Over the years, there have been lots of “hacker” movies of varying quality. Here are some good ones to watch before the movie “Blackhat” is out starring Chris Hemsworth. My favorites in bold. Tron (1982) 8.2/10 imdb Wargames (1983) 7.1/10 imdb Sneakers (1992) 7.1/10 imdb Jurassic Park (1993) 8/10 imdb Disclosure (1994) 6/10 imdb The …
Jan 07 2015
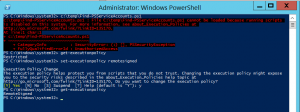
PowerShell Security: Execution Policy is Not An Effective Security Strategy – How to Bypass the PowerShell Execution Policy
If you have worked with PowerShell recently, you may have run into an Execution Policy message: c:\temp\Find-PSServiceAccounts.ps1 : File C:\temp\Find-PSServiceAccounts.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170. At line:1 char:1 + c:\temp\Find-PSServiceAccounts.ps1 + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : SecurityError: (:) [], PSSecurityException + FullyQualifiedErrorId : …
Dec 31 2014
Thunderstrike: EFI bootkits for Apple MacBooks via Thunderbolt & Option ROMs
Trammell Hudson (@qrs) developed the Thunderstrike exploit based on inherent security issues with the way Apple validates, updates, and boots from the boot ROM. The exploit takes advantage of the fact that Apple allows secure booting without hardware (software checks the ROM, but doesn’t perform a checksum!). Since the Thunderbolt port provides a way to …
Dec 26 2014
Interesting Windows Computer & Active Directory Well-Known Security Identifiers (SIDs)
The Microsoft Knowledge Base article KB243330 lists the well-known security identifiers in Windows operating systems Listed here are the more interesting ones from the article as well as some additional ones. Local Computer SIDs SID: S-1-5-2 Name: Network Description: A group that includes all users that have logged on through a network connection. Membership is …
Dec 21 2014
BadUSB Exploit: USBDriveBy
Samy posted a simple Mac OSX exploit leveraging the BadUSB vulnerability. USBdriveby is a device you stylishly wear around your neck which can quickly and covertly install a backdoor and override DNS settings on an unlocked machine via USB in a matter of seconds. It does this by emulating a keyboard and mouse, blindly typing …
Dec 19 2014
US-Cert’s Alert (TA14-353A): Targeted Destructive Malware
US-Cert has an excellent post on the Sony Malware: Alert (TA14-353A) Targeted Destructive Malware Overview US-CERT was recently notified by a trusted third party of cyber threat actors using a Server Message Block (SMB) Worm Tool to conduct cyber exploitation activities recently targeting a major entertainment company. This SMB Worm Tool is equipped with a …
Dec 15 2014
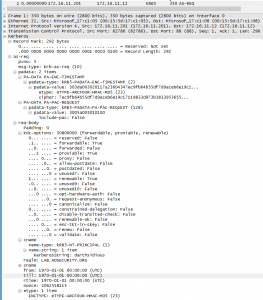
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
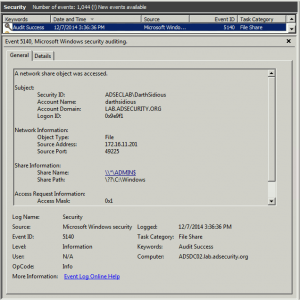
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …

Recent Comments