On Wednesday, August 3rd, I presented “Beyond the MCSE: Active Directory for the Security Professional” at Black Hat USA 2016. Here are the slides for this talk: US-16-Metcalf-BeyondTheMCSE-ActiveDirectoryForTheSecurityProfessional Here’s my talk description from the Black Hat website: Active Directory (AD) is leveraged by 95% of the Fortune 1000 companies for its directory, authentication, and management …
12 results for ms14068
Apr 13 2016
What Should I Do About BadLock (CVE-2016-2118 & CVE-2016-0128/MS16-047)?
What Should I Do About BadLock (CVE-2016-2118 & CVE-2016-0128/MS16-047)? The simple answer: Patch soon. Despite the hype, which led many to assume a Remote Code Execution (RCE) was involved, this issue requires a Man-int-the-Middle (MITM) attack in order to be successful. With that noted, it is still a serious issue that requires patching. Overview Badlock …
Top Posts
ADSecurity.org Active Directory Security Top Posts: Attack Methods for Gaining Domain Admin Rights in Active Directory Mimikatz Guide and Command Reference Microsoft Local Administrator Password Solution (LAPS) How Attackers Dump Active Directory Database Credentials Active Directory Recon Without Admin Rights The Most Common Active Directory Security Issues and What You Can Do to Fix Them …
Jan 01 2016
Attack Methods for Gaining Domain Admin Rights in Active Directory
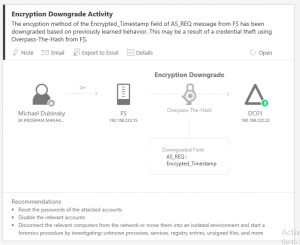
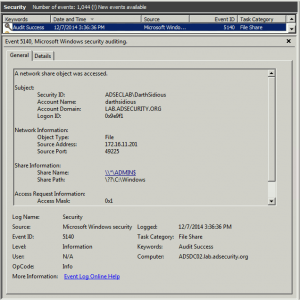
There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
Nov 30 2015
Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation)
At the RSA Conference in Abu Dhabi earlier this month, Stefano Maccaglia (Incident Response Consultant with RSA) presented “Evolving Threats: dissection of a Cyber-Espionage attack.” The slides for this talk are available on the RSA Conference site (UPDATE: RSA removed the slides from their site, Presentation Slides on Yumpu). This post covers and adds some …
Jun 24 2015
Microsoft Advanced Threat Analytics (ATA) Overview
Introduction There are several methods for identifying unusual or anomalous user activity. Traditionally these methods have required certain events be logged to the Windows event logs on workstations, servers, and Domain Controllers (DCs) and these events need to be forwarded to a central collection system. The drawback to this approach is numerous: the data logged …
Dec 15 2014
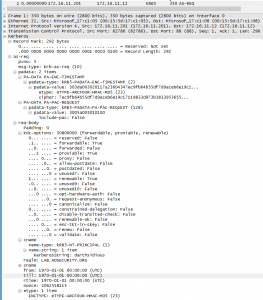
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
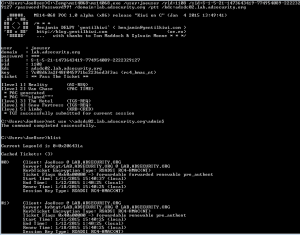
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …
- 1
- 2


Recent Comments