Microsoft Security Research and Defense blog posts that Microsoft EMET 5.2 is now available! Following is the list of the main changes and improvements: Control Flow Guard: EMET’s native DLLs have been compiled with Control Flow Guard (CFG). CFG is a new feature introduced in Visual Studio 2015 (and supported by Windows 8.1 and …
Category: Security
Feb 18 2015
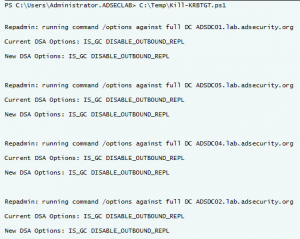
Interesting KRBTGT Password Reset Behavior
Following up on Twitter conversations (@passingthehash, @scriptjunkie1, gentilkiwi, etc) on the new KRBTGT Password Reset Script and Skip Duckwall’s (@passingthehash) blog post on how KRBTGT password changes work. Microsoft KB2549833 states that the KRBTGT password is set automatically to a random string when a new password is entered. This occurs because there is special logic …
Feb 11 2015
MS15-011 & MS15-014: Microsoft Active Directory Group Policy (GPO) Vulnerabilities Patched
On February’s Patch Tuesday (2/11/2015), Microsoft released two patches that fix issues with the way Group Policy is processed by the client. Interestingly enough, one of these vulnerabilities (MS15-014) makes the other one (MS15-011) not only feasible, but quite capable. The Attack Scenario: An attacker leverages the vulnerability described in MS15-014 to prevent/stop Group Policy …
Feb 03 2015
Configuring Two-Factor Authentication for Web (Cloud) Services
Don’t want your web (cloud) account password to get hacked? Enable Two-Factor Authentication (aka two-step verification)! Google Account: Visit this site and follow the instructions to configure your cell phone as a second factor Step 1: You’ll enter your password Whenever you sign in to Google, you’ll enter your password as usual. Step 2: You’ll …
Jan 19 2015
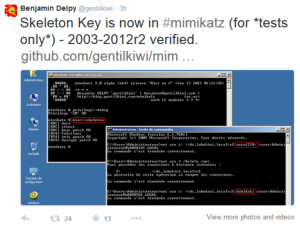
Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
Once an attacker has gained Domain Admin rights to your Active Directory environment, there are several methods for keeping privileged access. Skeleton Key is an ideal persistence method for the modern attacker. More information on Skeleton Key is in my earlier post. Note that the behavior documented in this post was observed in a lab …
Jan 16 2015
Active Directory Domain Controller Skeleton Key Malware & Mimikatz
Dell SecureWorks posted about the Skeleton Key malware discovered at a customer site. The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS. The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins. This enables the attacker to …
Jan 07 2015
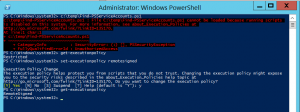
PowerShell Security: Execution Policy is Not An Effective Security Strategy – How to Bypass the PowerShell Execution Policy
If you have worked with PowerShell recently, you may have run into an Execution Policy message: c:\temp\Find-PSServiceAccounts.ps1 : File C:\temp\Find-PSServiceAccounts.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170. At line:1 char:1 + c:\temp\Find-PSServiceAccounts.ps1 + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : SecurityError: (:) [], PSSecurityException + FullyQualifiedErrorId : …
Dec 31 2014
Thunderstrike: EFI bootkits for Apple MacBooks via Thunderbolt & Option ROMs
Trammell Hudson (@qrs) developed the Thunderstrike exploit based on inherent security issues with the way Apple validates, updates, and boots from the boot ROM. The exploit takes advantage of the fact that Apple allows secure booting without hardware (software checks the ROM, but doesn’t perform a checksum!). Since the Thunderbolt port provides a way to …
Dec 26 2014
Interesting Windows Computer & Active Directory Well-Known Security Identifiers (SIDs)
The Microsoft Knowledge Base article KB243330 lists the well-known security identifiers in Windows operating systems Listed here are the more interesting ones from the article as well as some additional ones. Local Computer SIDs SID: S-1-5-2 Name: Network Description: A group that includes all users that have logged on through a network connection. Membership is …
Dec 21 2014
BadUSB Exploit: USBDriveBy
Samy posted a simple Mac OSX exploit leveraging the BadUSB vulnerability. USBdriveby is a device you stylishly wear around your neck which can quickly and covertly install a backdoor and override DNS settings on an unlocked machine via USB in a matter of seconds. It does this by emulating a keyboard and mouse, blindly typing …

Recent Comments