Earlier this year, Unix/Linux/*nix systems dealt with the “Hearbleed” OpenSSL vulnerability which affected a large portion of the web. There is a major vulnerability in Microsoft’s Schannel which was recently patched in MS14-066 (KB2992611). What is SChannel? The Secure Channel (Schannel) security package is a Security Support Provider (SSP) that implements the Secure Sockets Layer …
Category: Microsoft Security
Nov 10 2014
Kerberos & KRBTGT: Active Directory’s Domain Kerberos Service Account
Every Domain Controller in an Active Directory domain runs a KDC (Kerberos Distribution Center) service which handles all Kerberos ticket requests. AD uses the KRBTGT account in the AD domain for Kerberos tickets. The KRBTGT account is one that has been lurking in your Active Directory environment since it was first stood up. Each Active …
Nov 09 2014
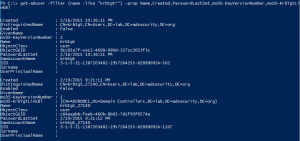
PowerShell Code: Check KRBTGT Domain Kerberos Account Last Password Change
From my GitHub Repo: Get-PSADForestKRBTGTInfo This function discovers all of the KRBTGT accounts in the forest using ADSI and returns the account info, specifically the last password change. Currently, the script performs the following actions: * Queries a Global Catalog in the Active Directory root domain for all KRBTGT accounts in the forest by querying …
Nov 07 2014
The Ultimate Movie Hacking Tool – Command Shell at Windows Logon Screen (via “StickyKeys”)
How many times have you seen a movie where the “hacker” connects to a system with a logon screen, hits a couple of keys, and gets a command shell. Here’s how this can be done for real in Windows. The issue is that the Windows Ease of Use tools are accessible at the logon screen. …
Nov 06 2014
How Attackers Extract Credentials (Hashes) From LSASS
I performed extensive research on how attackers dump credentials from LSASS and Active Directory, including pulling the Active Directory database (ntds.dit) remotely. This information is covered in two newer and greatly expanded posts: How Attackers Dump Active Directory Database Credentials Attack Methods for Gaining Domain Admin Rights in Active Directory Attackers can pull credentials …
Nov 04 2014
BackupExec Service Account Security FAIL
Yes. It actually says that if the BackupExec account is a member of Schema Admins, do not remove! To be fair, it starts off with this Solution which covers the rights required: From Symantec (http://www.symantec.com/business/support/index?page=content&id=TECH88242)
Nov 03 2014
PowerShell for Pentesters
PowerShell is extremely useful for admins. This power is also extremely useful for attackers. There are several PowerShell tools specifically for increasing access on a network: PowerSploit PowerSploit – PowerShell based pentest tool set developed by Mattifestation. PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid reverse engineers, forensic analysts, …
Oct 30 2014
BlueHat 2014 Slides: Reality Bites – The Attacker’s View of Windows Authentication and Post-exploitation
Each year, Microsoft invites security researchers (aka hackers) to speak to Microsoft employees about security issues. One of the most interesting talks listed at “BlueHat” 2014 was the one by the “Pass-the-Hash” experts, Chris Campbell, Bejamin Delpy, and Skip Duckwall. This talk will focus on the how Windows authentication works in the real world and …
Oct 25 2014
Microsoft EMET 5 Configuration to Mitigate PowerPoint Zero Day
Microsoft Security Advisory 3010060: Vulnerability in Microsoft OLE Could Allow Remote Code Execution (Published: October 21, 2014) PowerPoint Zero Day Vulnerability Executive Summary: Microsoft is aware of a vulnerability affecting all supported releases of Microsoft Windows, excluding Windows Server 2003. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft …
Oct 06 2014
Comparing ASLR on Windows & Linux
Two key differences regarding Linux & Windows Address Space Layout Randomization (ASLR): ASLR is not as prevalent in most Linux distributions as it is on modern Windows systems. ASLR cannot be force-enabled for applications on Linux, as EMET can do on Windows. Read the entire article at Cert.org

Recent Comments