Ensuring proper Domain Controller configuration is key for Active Directory security. Part of this is making sure they are running supported versions of Windows. At this point, DCs should be running at least Windows Server 2016, preferably Windows Server 2019 or 2022. Hold off on deploying Windows Server 2025 DCs for now due to the …
Category: ActiveDirectorySecurity
Sep 16 2025
Active Directory Security Tip #4: Default/Built-In Active Directory Groups
There are several default/built-in privileged groups that should be reviewed: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups PowerShell Script leveraging the Active Directory PowerShell module: https://github.com/PyroTek3/Misc/blob/main/Get-ADBuiltInAdmins.ps1
Sep 16 2025
Active Directory Lab Build Script
Over the summer, I rebuilt my Active Directory lab environment with multiple regional domains. Instead of manually configuring common issues, I decided to create a PowerShell script to do this for me.
Sep 15 2025
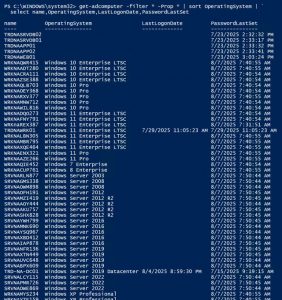
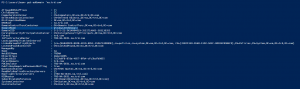
Active Directory Security Tip #3: Computer Accounts
Active Directory computers should be reviewed about once a year. Old operating systems can hold back security progress like keeping SMBv1 and NTLMv1 active. Inactive computers should be discovered and disabled when no longer in use (and eventually removed). The OperatingSystem & PasswordLastSet attributes are self-explanatory, though we can use the LastLogonDate which represents the …
Sep 15 2025
Active Directory Forest & Domain Level Capabilities
An important Active Directory setting determines what security capabilities are available which relates to the level of the forest and/or domain. This post collects the relevant capabilities of Windows domain and forest functional levels.You can easily check the domain & Forest functional levels using the Active Directory PowerShell module using the cmdlets Get-ADForest & Get-ADDomain. …
Sep 14 2025
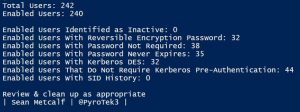
Active Directory Security Tip #2: Active Directory User Accounts
There are several different types of user accounts – at least how they are used. There are standard user accounts, service accounts, and admin accounts. There are numerous user account settings that can make them vulnerable. These configurations include: PowerShell code (using Active Directory PowerShell module):https://github.com/PyroTek3/Misc/blob/main/Get-VulnerableUserAccounts.ps1
Sep 12 2025
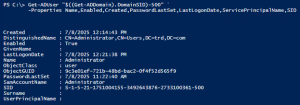
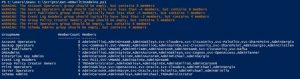
Active Directory Security Tip #1: Active Directory Admins
A critical part of Active Directory security is regularly reviewing your AD admins. The simplest way to do this is to recursively enumerate the membership of the domain Administrators group (that group’s members and all member group members). Check the AD Admins output for the following: PowerShell code (using Active Directory PowerShell modules):https://github.com/PyroTek3/Misc/blob/main/Get-ADAdmins.ps1
Dec 19 2020
Kerberos Bronze Bit Attack (CVE-2020-17049) Scenarios to Potentially Compromise Active Directory
Introduction & Attack Overview Jake Karnes (@jakekarnes42) with NetSPI published 3 articles (that’s right 3!) describing a new attack against Microsoft’s Kerberos implementation in Active Directory. He posted an Overview article, describing how the attack works, an Attack article on practical exploitation, and if you need further background on Kerberos, a Theory article. This article …




Recent Comments