Billy Rios explains how security-focused agencies keep making the same mistakes – this time it’s the TSA. Some of the issues identified in the talk: Network cable connections easily accessible by the public Hardcoded passwords in body scanner systems (which run Windows 98/WinXP) Accounts are stored in a config file. Network services enabled.(with hardcoded passwords) …
Category: Security
Aug 25 2014
Microsoft Enhanced Mitigation Experience Toolkit (EMET) 5 Protection Methods
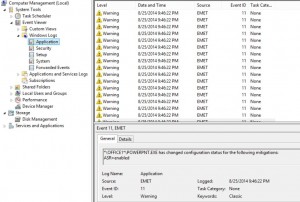
Microsoft Enhanced Mitigation Experience Toolkit (EMET) v5 security technology which I outlined in a previous post has several protection methods which will be detailed here. According to my sources at Microsoft 😉, EMET can be installed on workstations and servers (testing is always highly recommended before placing in production). Given the tremendous security improvements when …
Aug 20 2014
Microsoft EMET 5 Released
Microsoft’s EMET (Enhanced Mitigation Experience Toolkit) is a free download from Microsoft that enhances Windows security by preventing common malware and exploitation software methods. It does need to be well-tested before deployment, but there are several legacy Windows methods leveraged by malware to get into a system and take control. Installing EMET provides very strong protection …
Aug 13 2014
Apple iOS Security Whitepaper
In February of this year, 2014, Apple released an updated whitepaper describing Apple iOS Security. Overall, the operating system and its components are very securely designed. The Table of Contents: Introduction System Security Secure Boot Chain System Software Authorization Secure Enclave Touch ID Encryption and Data Protection Hardware Security Features File Data Protection Passcodes Data …
Jul 11 2014
Real-Time World Hack Map
This is an incredible map of the world that shows real-time network attacks. The animation makes it look like something out of the movie, “WarGames.” Most impressive. http://map.ipviking.com/?_ga=1.106938115.1477390587.1388686673#
May 20 2014
Microsoft BlueHat Resources
Microsoft has their own internal employee security conference called “BlueHat“. Here are session links from the past few years:
May 15 2014
Group Policy Preferences Password Vulnerability Now Patched
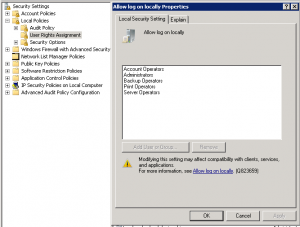
Looks like Microsoft finally removed the ability to set admin account passwords through GPP due to the Group Policy Preferences password exposure vulnerability. More information on how Group Policy Preferences are attacked is in the post “Finding Passwords in SYSVOL & Exploiting Group Policy Preferences“. Because of the security concerns with storing passwords in Group …
Jul 03 2013
Using Group Policy Preferences for Password Management = Bad Idea
Using Group Policy Preferences for Password Management = Bad Idea OR “How to Get Your Network Owned in Several Simple Steps” One of my customers recently needed to change the local administrator password on several hundred Windows 7 workstations and was trying to determine the best method: PowerShell script or Group Policy Preferences. The easy …

Recent Comments